DarkGate Loader Delivered via Microsoft Teams – How It Works, How to Mitigate It and How Forescout Can Help
The threat intelligence data that Forescout Research – Vedere Labs curates comes from the millions of connected devices that we monitor, attacks we observe and dissect in our sandboxes, data relating to attacks that is traded on the Darknet, and from our Adversary Engagement Environment. We see a lot of data. One thing no cybersecurity researcher wants to see, however, is an attack on their own organization.
That’s exactly what happened on September 25, when Forescout was targeted in a highly tailored phishing attack abusing Microsoft Teams functionality to deliver the DarkGate Loader malware. Since many of us are cybersecurity professionals, and all employees receive regular training on how to spot phishing attempts, our Information Security team was able to quickly intervene. No Forescout employee, customer or resource was affected by this incident since the malicious message was blocked before any employees could accept it.
Since then, we have analyzed the attack in detail. Here’s what we found…
The incident: SPIM campaign abusing Microsoft Teams to drop malware
Forescout Vedere Labs has been tracking a new Instant Messaging Spam campaign (often called SPIM) that is abusing Microsoft Teams functionality to send malicious attachments. The usage of Microsoft Teams to deliver SPIM was observed since Jan 2022 (right after Microsoft Teams released the new function allowing users from one organization to communicate with users in another). Threat actors began using compromised Office 365 accounts to send Microsoft Teams messages to other unconnected organizations to trick their users into downloading or opening malware.
In the case we recently analyzed, the payload in the ZIP archive delivered the DarkGate Loader malware. DarkGate Loader emerged in 2018 and was initially distributed via infected Torrent files or over email, often leveraging hijacked email threads. DarkGate is a modular loader. It includes native file download and execution, information stealing, remote access and control, keylogging and privilege escalation capabilities, and can be used to deliver secondary payloads including ransomware, bots, cryptocurrency miners and more.
The figure below shows the whole attack chain from when the Microsoft Teams message is sent to when the DarkGate Loader is executed.
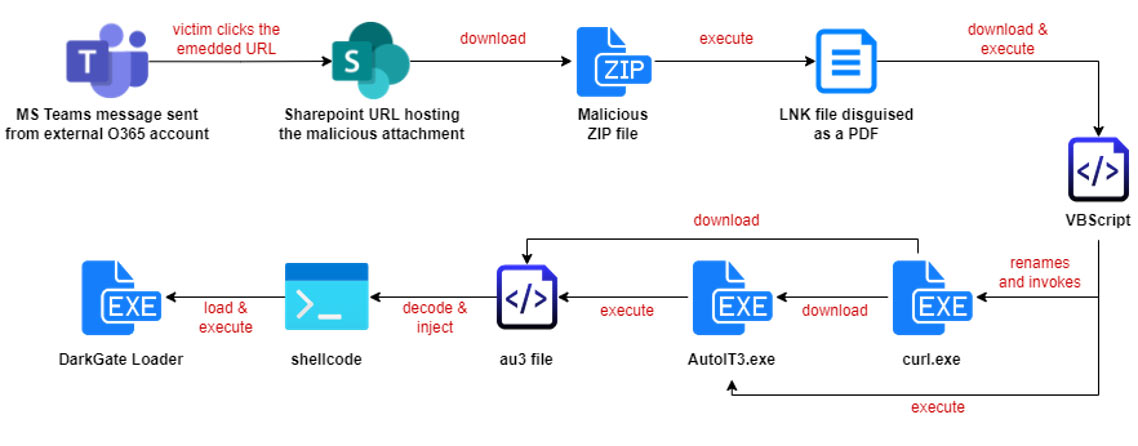
Targeted attacks leveraging generative AI
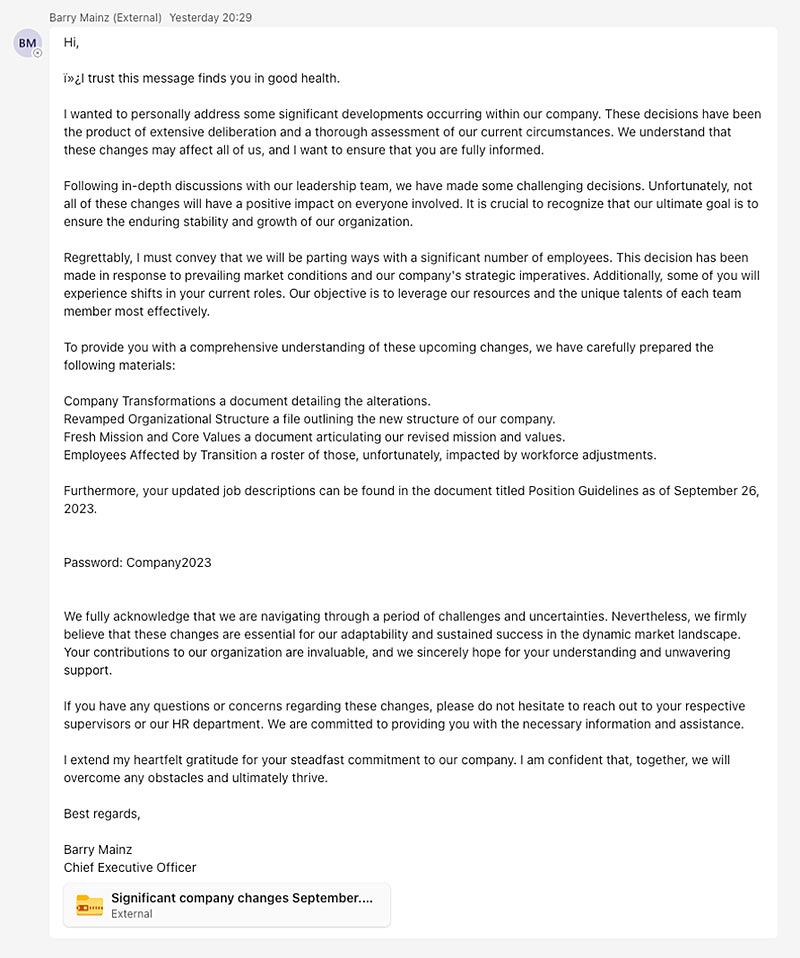
The campaign we observed was targeting Forescout, with the malicious ZIP archive delivered via a highly tailored Microsoft Teams message, appearing to be sent by Forescout’s CEO. The phishing message was well written, using credible business terminology that led us to suspect it was created by using generative AI. AI detectors score the message as high as 71% likely to have been written by AI. This seems to hint at the fact that threat actors are leveraging generative AI to make phishing messages virtually indistinguishable from legitimate ones. Here is the full text of the message. For the full technical analysis of the payload, read our technical report.
Recommended mitigations and response
Here are some mitigations helpful to protect organizations from malware delivered via Microsoft Teams:
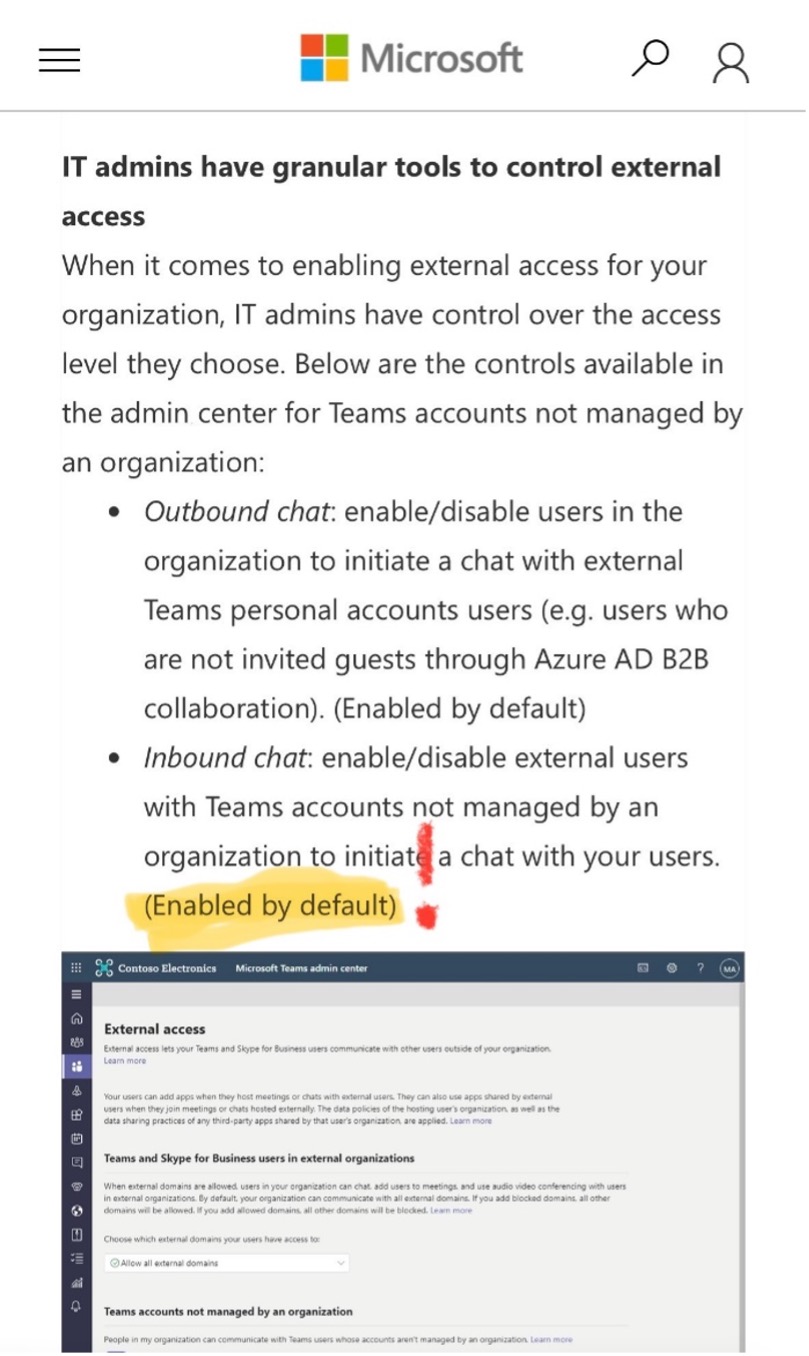
- Microsoft Teams can be configured to disable communication from external users (see screenshot below).
- In case of attacks, response teams should rapidly block the domain that the message is coming from (e.g., by using network access solutions).
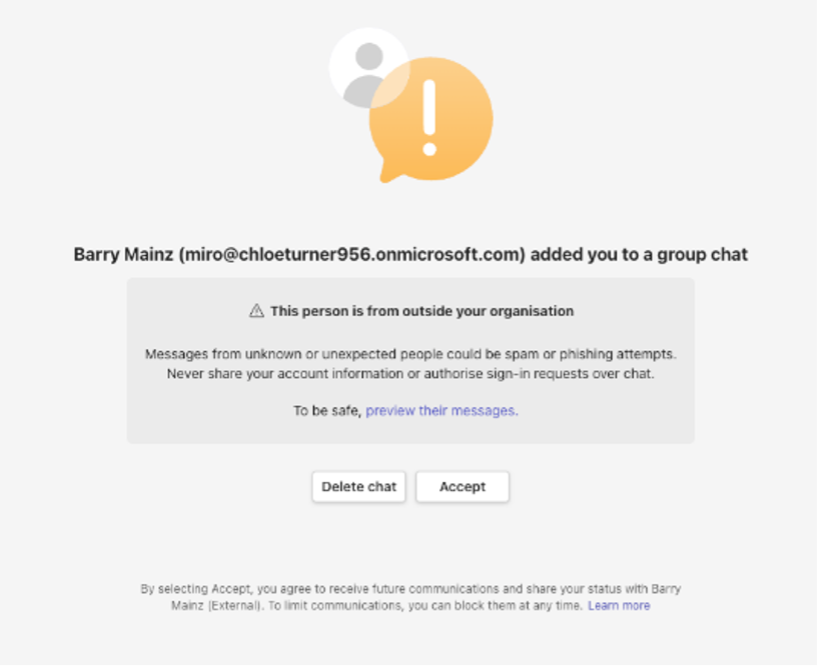
- Microsoft Teams users should be wary of external messages coming from untrusted/unknown domains (see splash screen below).
 |
 |
How Forescout can help
Forescout’s Threat Detection & Response solution can help to directly detect and respond to this threat. Below is a list of possible threat hunting opportunities. For each opportunity, we list which TDR detection rules could possibly fire, helping SOC analysts during their hunting activities.
| Threat Hunting Opportunity | Forescout TDR Rules That Can Help | Associated MITRE Tactic |
|---|---|---|
| Suspicious File Execution by Wscript/Cscript
This hunt identifies uncommon file execution by Wscript.exe and Cscript.exe in user folders. Attackers often use such suspicious scripts to execute malware and LOLBINS as Wscript or Cscript child processes. This activity could indicate attempts to evade traditional security measures or carry out malicious actions on a system. |
|
Execution |
| Suspicious Process – Curl to External IP Address
This hunt identifies the cURL utility being used to connect to a remote IP address. Malicious actors often use cURL to download additional payloads after gaining access to a target resource. |
|
Command & Control
|
| File Created in Startup Folder
This indicator rule triggers on detecting files being created in the Windows startup directory. This can automatically execute a program during system boot or logon to maintain persistence or gain higher-level privileges on compromised systems. |
|
Persistence |
| IP Address Accessed Directly Instead of Domain
This hunt looks for connections made to an IP address directly instead of a domain. Malware often downloads malicious payloads from remote servers. By accessing these servers directly, malware can avoid being detected by security solutions that block domain names associated with known malware distribution sites. |
|
Command & Control |
| Stored Browser Credentials Accessed
This hunt looks for instances of browser credentials being accessed by a process other than browser process itself. Adversaries may acquire credentials from web browsers by reading files specific to the target browser. |
|
Credential Access |
| Remote Monitoring and Management (RMM) Tool Usage Detected
This hunt looks for usage of RMM tools that are not used by the organization. An adversary may use legitimate desktop support and remote access software, such as Team Viewer, AnyDesk, Go2Assist, LogMein, AmmyyAdmin, etc, to establish an interactive command and control channel to target systems within networks. |
|
Command & Control
|
| Windows Defender Exclusion Added Using PowerShell
This hunt detects attempts to add to the exclusions list of Windows Defender using PowerShell. Adding a process, an extension or a path to Windows Defender’s Exclusion List will stop Windows Defender from scanning and monitoring such files. This can allow attackers to safely drop and execute malware without being detected. |
|
Defense Evasion |
| System Information Discovery This hunt detects attempts to get detailed information about operating systems and hardware, including version, patches, hot fixes, service packs and architecture. Adversities may use the information obtained during automated discovery, to shape follow-on behavior, including whether the adversary fully infects the target or attempts specific actions. |
|
Discovery |
| IOC Search Search for known Indicators of Compromise (IOCs) |
|
Command & Control
|
| Hunt for Phishing Emails
Hunt for phishing emails using email gateway logs. |
|
Initial Access |
IOCs relevant to DarkGate malware SPIM campaign
Forescout Vedere Labs is constantly tracking emerging threats such as the DarkGate malware and generating IOCs that can help threat hunting activities. Information about the following relevant IOCs is available by subscribing to our Vedere Labs Threat Feeds Service. Our feeds are also directly consumed by the Forescout Platform, including our Threat Detection & Response solution.
| Type | Indicators |
|---|---|
| IP address | 185.39.18.170
5.188.87.58 |
| SHA256 | fd758ef8e211fbd7eca6fa5d817a6c17
a5c037dadbb68777e54b5b10a7362ce1 f3ebac62f6f648bbb02775e5b53bd4ba 6222785ea87e7a8ed5a554fe9b14dad1 652a4dd6f0c5cc44aa934c6a83f9d796 c56b5f0201a3b3de53e561fe76912bfd 7fdd6ea882945269ca95e4ae677f2723 c58efaa542aa3c052a23fa7aec37a4ef |
| ULR | hxxps–//ChloeTurner956-my.sharepoint.com/personal/miro_chloeturner956_onmicrosoft_com/Documents/Microsoft%20Teams%20Chat%20Files/Significant?company%20changes%20September.zip |
Download the full threat briefing report for more details on the incident and the deployed payload.