CYBERSECURITY A-Z
What Is NERC CIP?
In the United States, critical infrastructure industries are governed either by self-regulation or specific government regulations tailored to each sector. Among these, the North American Electric Reliability Corporation Critical Infrastructure Protection stands out with more than 100 standards designed to safeguard critical assets in North America’s bulk electric systems (BES).
These standards are mandatory for large-scale power systems, typically operating at 100 kV or higher, including assets for power generation, transmission, and distribution. These standards ensure the reliable delivery of electricity across the U.S., Canada, and parts of Mexico.
“The vision for the Electric Reliability Organization Enterprise, which is comprised of NERC and the six Regional Entities, is a highly reliable and secure North American bulk power system. Our mission is to assure the effective and efficient reduction of risks to the reliability and security of the grid.”1
This non-profit international regulatory body provides a comprehensive framework to mitigate risks from cyberattacks, physical intrusions, and insider threats. Certified by the Federal Energy Regulatory Commission (FERC) to oversee grid reliability, these standards are enforced through audits and oversight by the North American Electric Reliability Corporation and its regional entities.
What Kind of Organizations Are Impacted by NERC CIP Requirements?
Essentially, any organization identified as a “Registered Entity” and involved in operating or supporting the BES must comply with the standards to ensure their operational systems remain resilient and secure.
Specifically, it applies to entities that are part of North America’s bulk electric system, including, but not limited to:
- Electric Utilities
- Transmission Operators
- Generation Operators
- Balancing Authorities
- Independent System Operators (ISOs) and Regional Transmission Organizations (RTOs)
- Organizations that manage the flow of electricity on the grid and coordinate regional transmission.
- Reliability Coordinators
- Entities responsible for ensuring that the BES operates reliably under varying conditions.
- Electric Cooperatives and Municipal Utilities
- Smaller utility providers also fall under the standard depending on their involvement with BES assets. That said, these standards are only partially applicable to generation facilities producing less than 20 megawatts (MW) of electricity. Smaller power generation systems (e.g., certain renewable energy sources) may not be subject to the same rigorous regulatory requirements as larger BES assets, though they must still adhere to baseline security and reliability standards.
Why Do NERC CIP Standards Matter?
According to ASIS, the following serve 145 million households and businesses in the U.S.2:
- 7,300 power plants
- 300,000 transmission and distribution stations
- 160,000 miles of high-voltage transmission lines
- 5 million miles of local distribution lines
Moreover, the number of susceptible points on the U.S. electrical networks has been increasing by about 60 per day, making them increasingly vulnerable to cyberattacks.3 The standards play a critical role in protecting North America’s power grid from evolving threats, and the electricity portion of the Energy sector is a primary target for cyberattacks and physical intrusions, given the potential cascading effects of disrupting electricity supply.
Compliance addresses the concerns associated with these threats:
- Preventing Blackouts. Protecting critical assets ensures the uninterrupted delivery of electricity, reducing the risk of large-scale outages.
- National Security. The power grid is integral to the functioning of society, such as transportation, healthcare, and water systems. Securing it is vital to national security.
- Trust and Resilience. Compliance builds trust and confidence in the reliability of the electricity supply among stakeholders, including governments, businesses, and consumers.
- Evolving Threat Landscape. As cyber threats become more sophisticated, this framework and standards provide a roadmap for organizations to adapt and improve their defenses.
Common NERC CIP Requirements
While the 13 active standards address different aspects of infrastructure protection, they collectively aim to create a robust security posture for BES operations to ensure all aspects of physical and cyber security are addressed.
CIP-002: Bulk Electric System (BES) Cyber System Categorization
Ensures that organizations determine the impact of systems on reliable BES operations and apply appropriate protections.
Key aspects include:
- Asset Identification: Listing all BES Cyber Assets within a facility and identifying those that meet specific criteria for criticality.
- Impact Assessment: Evaluating each asset’s potential impact on the reliability of the BES to classify systems as low, medium, or high impact.
- Documentation: Maintaining clear records of identified assets and their categorizations, providing a basis for compliance with other bulk electric standards.
- Applicability: This standard applies to responsible entities such as Transmission Operators, Generation Operators, and Reliability Coordinators.
CIP-003: Security Management Controls
Focuses on establishing and maintaining policies and procedures for security management to ensure that the appropriate roles, responsibilities, and processes are in place to protect critical assets within the BES.
Key elements include:
- Cybersecurity Policies: Developing documented policies that address cybersecurity requirements and aligning them with other bulk electric standards.
- Awareness and Training: Ensuring personnel understand the security requirements and receive relevant training to maintain compliance.
- Accountability: Assigning clear responsibilities for implementing and enforcing security policies.
- Exception Management: Establishing a formal process for documenting, reviewing, and approving any exceptions to the standard.
CIP-004: Personnel & Training
Focuses on ensuring personnel with access to critical assets are adequately trained and vetted to mitigate risks associated with insider threats and human error.
Key elements include:
- Personnel Risk Assessment: Conducting background checks and risk assessments for individuals with authorized access to critical systems.
- Training Programs: Providing security awareness training tailored to the roles and responsibilities of personnel.
- Access Management: Granting access only to those who have completed required training and demonstrated trustworthiness.
- Recordkeeping: Documenting all training, assessments, and access-related decisions for audit and compliance purposes.
CIP-005: Electronic Security Perimeters (ESP)
Ensures the prevention of unauthorized access and the monitoring of communication within these perimeters.
Key elements include:
- Electronic Security Perimeters: Establishing boundaries around critical systems and identifying all access points.
- Access Controls: Implementing measures to manage and monitor electronic access, including user authentication and authorization.
- Monitoring and Logging: Ensuring continuous monitoring of ESP access points and maintaining detailed logs of all activities for auditing purposes.
- External Connections: Assessing and controlling communications between systems inside the ESP and external systems to prevent unauthorized access or data breaches.
CIP-006: Physical Security of BES Cyber Systems
Focuses on protecting physical access to infrastructure to prevent unauthorized access and physical tampering.
Key elements include:
- Physical Security Plans: Developing and implementing documented security plans for BES systems and their associated assets.
- Access Controls: Establishing measures to manage and monitor physical access to secure locations, including authentication mechanisms such as badges or biometrics.
- Monitoring and Surveillance: Implementing physical monitoring systems, such as video surveillance or alarm systems, to detect and respond to unauthorized access attempts.
- Physical Barriers: Installing secure barriers, such as fences or locked doors, to prevent unauthorized entry to critical areas.
- Visitor Management: Maintaining records of individuals who access secure areas, including visitors, to ensure accountability.
CIP-007: Systems Security Management
Outlines requirements for system configuration, maintenance, and monitoring to ensure security best practices are applied.
Key elements include:
- Patch Management: Regularly identifying, testing, and applying security patches to address known vulnerabilities.
- Malware Prevention: Deploying mechanisms to detect and prevent malware infections, such as antivirus software or application whitelisting.
- System Access Controls: Ensuring only authorized personnel can access systems and their associated data.
- Logging and Monitoring: Maintaining logs of system activity to detect unauthorized actions and support incident response.
- Vulnerability Assessments: Performing periodic evaluations to identify and mitigate potential security risks.
CIP-008: Incident Reporting and Response Planning
Focuses on ensuring a timely and effective response to cybersecurity incidents affecting systems.
Key elements include:
- Incident Response Plans: Establishing formal plans to address and manage cybersecurity incidents, including predefined roles and responsibilities.
- Incident Identification and Reporting: Detecting and categorizing incidents based on their potential impact on BES operations and reporting them to the appropriate regulatory authorities.
- Mitigation and Recovery: Implementing measures to contain and remediate the effects of incidents while restoring normal system functionality.
- Post-Incident Review: Conducting thorough evaluations of incidents to identify root causes and improve future response strategies.
- Documentation: Maintaining detailed records of incidents, actions taken, and lessons learned to demonstrate compliance and enhance preparedness.
CIP-009: Recovery Plans for BES Cyber Systems
Focuses on maintaining and testing plans to enable a quick and effective return to normal operations after incidents.
Key elements include:
- Recovery Plan Development: Creating detailed plans that outline the steps to restore systems after a disruption. Plans should address all potential scenarios, including natural disasters, cyberattacks, or equipment failures.
- Plan Testing and Updates: Regularly testing plans through exercises and simulations to validate their effectiveness and making necessary updates based on test results or changes in the operating environment.
- Backup and Restoration Procedures: Ensuring the availability of system backups and defining processes for their secure restoration.
- Resource Allocation: Identifying and securing the resources needed for recovery, including personnel, tools, and facilities.
- Documentation and Communication: Maintaining comprehensive documentation of plans and ensuring clear communication protocols during restoration efforts.
CIP-010: Configuration Change Management and Vulnerability Assessments
Focuses on ensuring the secure management of changes and conducting threat assessments for critical infrastructure.
Key elements include:
- Configuration Change Management: Putting in place processes to manage changes of critical systems, ensuring that these changes don’t compromise security or operations. This includes documenting, reviewing, and testing changes before implementation.
- Vulnerability Assessments: Regularly assessing and identifying potential security weaknesses in critical systems. These assessments must be documented, with the organization taking appropriate actions to mitigate any identified risks.
CIP-011: Information Protection
Focuses on protecting sensitive information from unauthorized access or misuse.
Key elements include:
- Access Control: Limiting access to sensitive information based on need-to-know principles.
- Information Handling: Proper handling, storage, and transmission of sensitive data to prevent unauthorized access or disclosure.
- Information Retention and Disposal: Establishing guidelines for retaining and securely disposing of sensitive information.
The goal of CIP-011 is to ensure that critical information is protected, reducing the risk to the reliability of the power grid.
CIP-012: Cyber Security
Focuses on protecting communication networks and systems used for the transmission of critical data in the electric grid.
Key elements include:
- Data Encryption: Ensuring that sensitive information transmitted over communication networks is encrypted to prevent unauthorized access or tampering.
- Access Control: Implementing measures to restrict access to communication networks to authorized personnel only.
- Security Practices: Adopting best practices to secure communications, including monitoring for potential issues and responding to threats.
CIP-013: Supply Chain Risk Management
Focuses on mitigating risks associated with supply chain dependencies for critical systems.
Key elements include:
- Risk Assessments: Identifying and evaluating cybersecurity risks posed by suppliers of critical equipment and services.
- Security Requirements: Establishing cybersecurity controls and requirements for suppliers to ensure their products and services meet the necessary security standards.
- Ongoing Monitoring: Continuously monitoring the supply chain to detect emerging risks and ensure compliance with security measures.
CIP-014: Physical Security
Focuses on the physical security of critical facilities and infrastructure essential to the reliable operation of the electric grid.
Key elements include:
- Risk Assessment: Identifying potential physical threats and vulnerabilities to critical assets, such as substations and control centers.
- Physical Security Measures: Implementing security measures like access controls, surveillance, and protective barriers to safeguard critical infrastructure from physical attacks or unauthorized access.
- Threat Mitigation: Taking appropriate actions to address identified risks, including securing physical locations against sabotage, terrorism, or natural disasters.
A proposed reliability standard is NERC CIP-015-14, which focuses protecting real-time monitoring and control systems used in the operation of the electric grid.
Key elements include:
- Cybersecurity Requirements: Implementing controls to safeguard real-time systems from unauthorized access and cyber threats, including the use of firewalls, encryption, and access management.
- System Availability: Ensuring that monitoring and control systems remain functional during emergencies or disruptions, with provisions for backup systems and continuity of operations.
- Incident Response: Developing and testing response plans to quickly address security breaches or system failures, minimizing downtime.
The goal of CIP-015-1 is to protect the integrity and availability of real-time monitoring and control systems, which are crucial for the reliable operation of the bulk electric system.
Common Compliance Challenges
Achieving and maintaining compliance is a complex and ongoing process. Many organizations face the following challenges:
- Identifying BES Assets: Properly identifying and categorizing systems can be challenging, especially in large, complex environments with numerous assets.
- Understanding Vulnerabilities: Compliance with these requirements can be a challenge as organizations often lack complete visibility into devices on their Operational Technology (OT) networks – or whether the devices are accurately configured.
- Managing Access Controls: Ensuring only authorized personnel have access to critical systems while maintaining audit trails can be difficult to enforce consistently.
- Monitoring and Reporting: Real-time monitoring of security perimeters, logging access attempts, and generating detailed compliance reports require sophisticated tools and processes.
- Supply Chain Risks: Managing third-party risks and ensuring vendors comply with CIP-013 requirements adds complexity to compliance efforts.
- Keeping Pace with Evolving Standards: These standards are updated regularly to address emerging threats. Staying current requires continuous effort and adaptation.
- Resource Constraints: Compliance efforts demand skilled personnel, time, and financial investment, which can strain organizations, particularly smaller utilities.
- Penalties for Non-Compliance: Noncompliance with standards can incur significant penalties5, with the potential for fines of up to $1 million per day per violation. The high stakes of non-compliance, including financial penalties and reputational damage, make achieving compliance even more critical but also more stressful.
How Forescout Can Help with NERC CIP Compliance
Forescout provides advanced network security solutions that help organizations streamline and strengthen their compliance efforts.
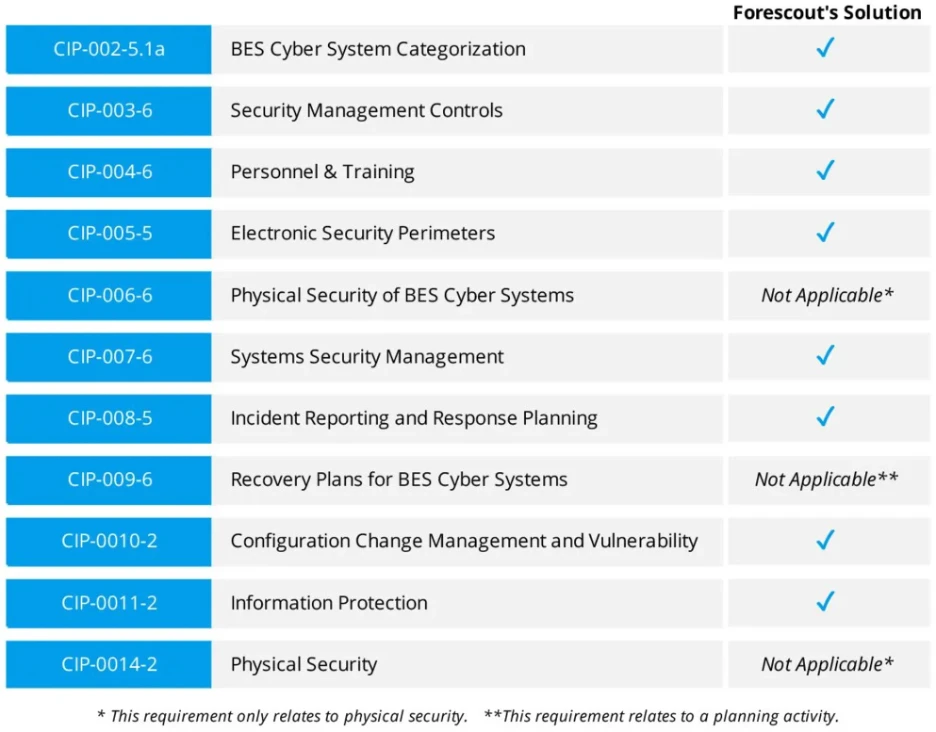
- Asset Discovery and Classification: Forescout’s platform automatically identifies and categorizes all assets within the network, including IT, OT, and IoT devices, ensuring no critical assets are overlooked during CIP-002 compliance efforts.
- Access Control and Monitoring: The platform enforces and monitors access controls to ensure that only authorized personnel can interact with systems. This supports CIP-004 and CIP-005 compliance by managing access within secure perimeters.
- Real-Time Monitoring and Alerts: Forescout provides continuous visibility into network activity, detecting unauthorized access attempts and unusual behavior. This helps organizations maintain their Electronic Security Perimeters (CIP-005) and manage system vulnerabilities (CIP-007).
- Configuration and Change Management: Automates monitoring and tracks changes across the network to ensure compliance with CIP-010 requirements.
- Supply Chain Risk Management: Assists in identifying and mitigating supply chain risks, helping organizations comply with CIP-013 by validating vendor access and monitoring third-party interactions.
- Comprehensive Reporting: Forescout’s platform generates detailed compliance reports, simplifying audit preparation and ensuring organizations can demonstrate adherence to these standards.
- Scalability and Flexibility: Designed to scale with the size and complexity of any organization, Forescout’s solutions integrate seamlessly with existing IT and OT environments, ensuring compliance efforts grow with organizational needs.
While the journey to compliance is complex, leveraging advanced solutions provided by Forescout can simplify the process, mitigate risks, and help organizations stay ahead of evolving threats.
1 NERC. Home page. Accessed December 20, 2024 from the following source: https://www.nerc.com/Pages/default.aspx
2 ASIS International. Girding the Grid. Accessed December 20, 2024 from the following source: https://www.asisonline.org/security-management-magazine/monthly-issues/security-technology/archive/2024/february/girding-the-grid/
3 Reuters. US electric grid growing more vulnerable to cyberattacks, regulator says. Accessed December 20, 2024 from the following source: https://www.reuters.com/technology/cybersecurity/us-electric-grid-growing-more-vulnerable-cyberattacks-regulator-says-2024-04-04/
4 Forescout. New NERC CIP standards: Why utilities shouldn’t wait to deploy, May 30, 2024 https://www.forescout.com/blog/new-cip-standards-why-utilities-should-not-wait-to-deploy/
5 NERC. Enforcement Actions 2023. Accessed December 20, 2024 from the following source: https://www.nerc.com/pa/comp/CE/Pages/Actions_2023/Enforcement-Actions-2023.aspx