On March 9th, the world woke up to the news of yet another large-scale security breach. A group of hackers got access to and control of thousands of security cameras developed and managed by Verkada, a Silicon Valley-based company that sells security as a service. They provide their customers with hardware (their IP cameras) that is installed in key areas within those customers’ facilities. The footage collected by the cameras is then uploaded to the cloud, where its software systems provide a dashboard for the visualization of the videos. In this way, the customers’ physical security teams can monitor all their sites from any browser and device.
Figure 1 shows a sketch of how this works.
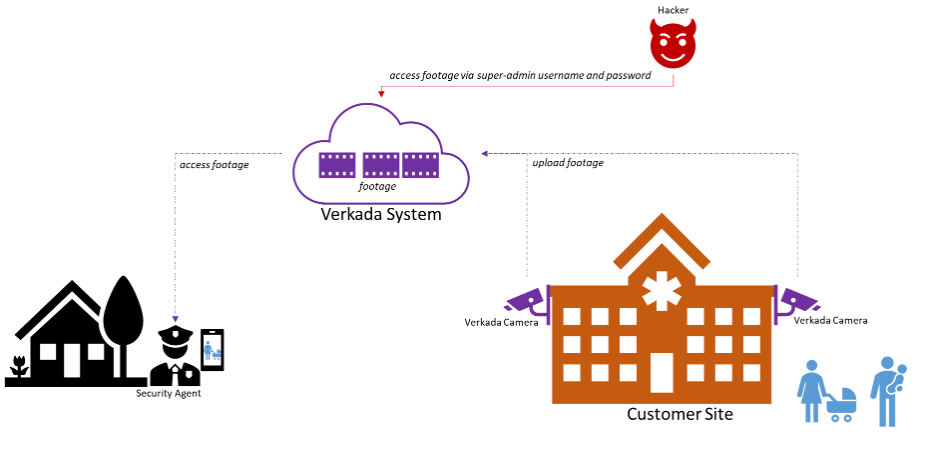
Unfortunately, a hacker group managed to find online a username and a password associated with a super-admin account. A super-admin is an account with permissions to access and control cameras across multiple customers. By leveraging this account, the hackers could access footage data stored on the cloud that came from thousands of cameras deployed in hospitals, jails, offices, manufacturing plants and other facilities.
It is important to note that this was not a complex hack. No software vulnerability was exploited, and the hackers did not get access to Verkada’s customer networks. They ‘simply’ accessed the video footage coming from the cameras deployed at those customers.
This incident is a real example of hackers having access to and exfiltrating sensitive data (video and audio) from critical facilities, but even worse attack scenarios are possible with connected cameras and access control systems used in smart buildings. When malicious actors take control of these types of devices, they can inject fake footage, control access to sensitive locations and clear the way for physical attacks, as Forescout Research Labs has demonstrated before.
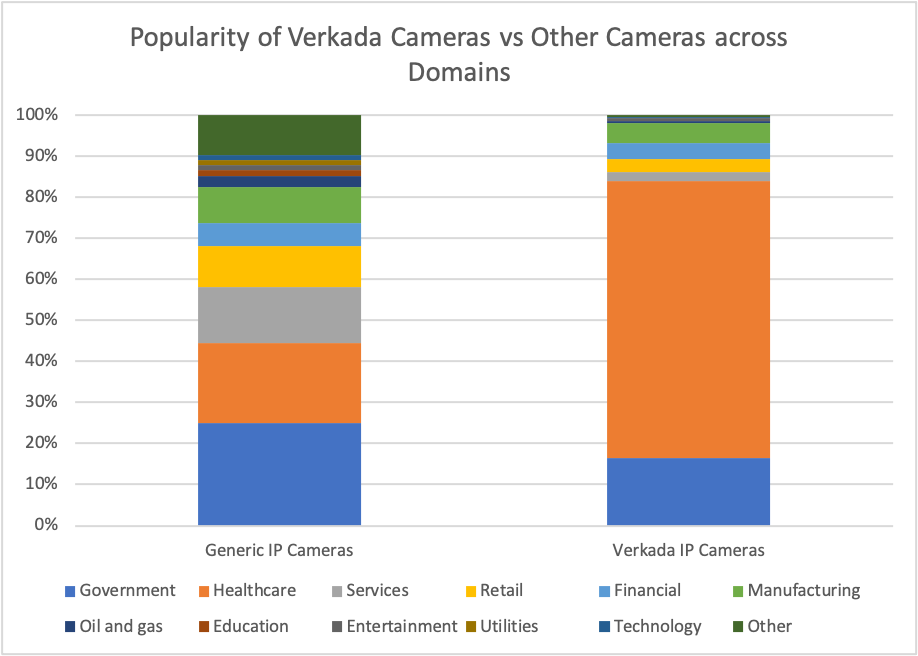
To help us understand how widespread these threats are among our customer base, we looked at data from the Forescout Device Cloud, which contains data from about more than 12 million devices coming from our product installations at thousands of customers. Figure 2 shows how popular Verkada cameras are across the networks that we monitor, in comparison with other IP camera vendors (not all of which provide a cloud-based service). Looking at that data, we could determine that these cameras are most popular in Healthcare and Government facilities, and we see 4 times more Verkada cameras in Healthcare than in Government.
This is concerning because the data (including video) from healthcare facilities is extremely sensitive and, when it is managed by a third-party, healthcare organizations are implicitly putting a lot of trust in that third-party. Data breaches, even when they happen because of third-parties, can have a large impact on a company’s reputation.
Access to an organization’s devices and data are naturally becoming more distributed nowadays, for instance with data uploaded to cloud services and VPN access for remote work and maintenance, which means there may be new weak links added to a network regularly. That makes it essential for organizations to map all their external access points, understand which of their devices receive or send data to outside networks and assess the risks of this data being shared with the service providers. At the same time, service providers must ensure that they do their utmost to protect the data entrusted with them, starting by not using default or hard-coded credentials that allow for access to all the data and adopting two-factor authentication amongst other things.
To help mitigate against this in future, it is important to cover basic cyber hygiene. Make sure you know where these devices are on your network and what they have access to. We find that Forescout customers use our solution to automate isolation of the device if the profile changes and reduce the scope of any incident that occurs.
Forescout provides visibility into every connected IP-camera including Verkada to pin-point high risk cameras. Forescout eyeControl works with your existing network infrastructure and security tools to automate security policies for isolating and mitigating risk from anomalous behaviors and eyeSegment will ensure cameras are isolated from other networks segment with more critical devices (e.g. MRIs in healthcare) so that even when breaches like this happen, hackers cannot use cameras as entry point to more sensitive targets.