Thousands of companies compromised by REvil Ransomware – the supply chain strikes again
On July 2, news emerged of a large-scale attack leveraging the Kaseya VSA network monitoring and management solution to deploy a variant of the REvil ransomware. The attackers claimed that more than a million devices had been infected and they demanded $70 million in Bitcoin to publish a tool to decrypt the files of all victims.
Since then Kaseya recommended customers to disable on-premise VSA servers immediately, took their SaaS offering offline, then released patches for the on-premise vulnerabilities and restored the SaaS servers.
This recent event is illustrative of three very important trends in the current attacker landscape. First, the rise of Cybercrime-as-a-Service. Second, the use of ransomware, which is sometimes coupled with extortion and threats of publishing exfiltrated data to increase financial gains. Third, the leveraging of supply-chain components to compromise several organizations at the same time, which makes this attack reminiscent of the SolarWinds hack at the end of 2020.
Below, we discuss the attack and what Forescout customers should do.
REvil – ransomware-as-a-service and the most recent supply-chain attack
REvil, also known as Sodinokibi, is a Ransomware-as-a-Service group, which means that the same encryption malware can be used by many different affiliate malicious actors who only have to figure out how to compromise target networks and deploy the malware. The revenue is then divided between ransomware developers and affiliates.
Forescout first noticed REvil in September, 2019 and they have been very active ever since. The group was behind recent attacks on meat supplier JBS (which resulted in the company paying $11 million to recover their systems) and computer manufacturer Acer (when they demanded a $50 million ransom, the largest ever until now), to name a few.
The current attack leveraged Kaseya VSA, which is a remote monitoring and management solution used by several managed service providers (MSPs) – companies that use Kaseya software to manage smaller businesses. The tool provides a central dashboard to monitor and manage endpoints and deploy security patches, among other functions.
The main vulnerabilities used in the attack were CVE-2021-30116 (a credentials leak and business logic flaw), CVE-2021-30119 (a cross-site scripting) and CVE-2021-30120 (a two-factor authentication bypass). The vulnerabilities were discovered by the Dutch Institute for Vulnerability Disclosure (DIVD) and reported to Kaseya, who was working on the patches even before the REvil attack happened. Using these vulnerabilities, the actors delivered ransomware via an automated (fake) software update from compromised VSA servers to VSA agents running on managed Windows devices.
Kaseya reported that 50 customers were affected. Around 40 of those were MSPs, which means that their customers could also be affected. In the end, the company said that around 1500 organizations were affected, many of which are small and medium sized businesses.
What should Forescout customers do?
As recommended by Kaseya, any on-premise VSA server should be immediately patched.
We see 116 customers on Device Cloud with Kaseya installed on their devices (close to 7% of the total 1,688 customers uploading data to Device Cloud). On these customers, we see close to 30,000 devices with the agent and 9 with the server, divided by industry verticals as shown below.
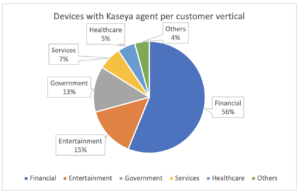
These customers can use eyeSight to locate devices running the VSA server or agent using the “Windows Applications Installed” attribute given by the HPS Inspection Engine plugin. The values to look for are “Kaseya Agent” and “Kaseya Server”.
Once devices running Kaseya are identified, users can procced with patching as described by Kaseya. CISA/FBI also recommend to download and run the IoC detection tool provided by Kaseya on both servers and managed endpoints to detect signs of intrusion.