Forescout Research Labs, with support from Medigate Labs, have discovered a set of 13 new vulnerabilities affecting the Nucleus TCP/IP stack, which we are collectively calling NUCLEUS:13. The new vulnerabilities allow for remote code execution, denial of service, and information leak.
Nucleus is used in safety-critical devices, such as anesthesia machines, patient monitors and others in healthcare. Forescout Research Labs is committed to supporting vendors in identifying affected products (our open-source TCP/IP stack detector can be helpful in this respect) and to sharing our findings with the cybersecurity community.
The table below shows the newly discovered vulnerabilities. Rows are colored according to the CVSS score: yellow for medium or high and red for critical.
| CVE ID | Description | Affected component | Potential Impact | CVSSv3.1 Score |
|---|---|---|---|---|
| 2021-31344 | ICMP echo packets with fake IP options allow sending ICMP echo reply messages to arbitrary hosts on the network. | ICMP | Confused deputy | 5.3 |
| 2021-31345 | The total length of an UDP payload (set in the IP header) is unchecked. This may lead to various side effects, including Information Leak and Denial-of-Service conditions, depending on a user-defined applications that runs on top of the UDP protocol. | UDP | Application- dependent |
7.5 |
| 2021-31346 | The total length of an ICMP payload (set in the IP header) is unchecked. This may lead to various side effects, including Information Leak and Denial-of-Service conditions, depending on the network buffer organization in memory. | IP / ICMP | Information leak / DoS | 8.2 |
| 2021-31881 | When processing a DHCP OFFER message, the DHCP client application does not validate the length of the Vendor option(s), leading to Denial-of-Service conditions. | DHCP client | DoS | 7.1 |
| 2021-31882 | The DHCP client application does not validate the length of the Domain Name Server IP option(s) (0x06) when processing DHCP ACK packets. This may lead to Denial-of-Service conditions. | DHCP client | DoS | 6.5 |
| 2021-31883 | When processing a DHCP ACK message, the DHCP client application does not validate the length of the Vendor option(s), leading to Denial-of-Service conditions. | DHCP client | DoS | 7.1 |
| 2021-31884 | The DHCP client application assumes that the data supplied with the “Hostname” DHCP option is NULL terminated. In cases when global hostname variable is not defined, this may lead to Out-of-bound reads, writes, and Denial-of-service conditions. | DHCP client | Application-dependent | 8.8 |
| 2021-31885 | TFTP server application allows for reading the contents of the TFTP memory buffer via sending malformed TFTP commands. | TFTP server | Information leak | 7.5 |
| 2021-31886 | FTP server does not properly validate the length of the “USER” command, leading to stack-based buffer overflows. This may result in Denial-of-Service conditions and Remote Code Execution. | FTP server | RCE | 9.8 |
| 2021-31887 | FTP server does not properly validate the length of the “PWD/XPWD” command, leading to stack-based buffer overflows. This may result in Denial-of-Service conditions and Remote Code Execution. | FTP server | RCE | 8.8 |
| 2021-31888 | FTP server does not properly validate the length of the “MKD/XMKD” command, leading to stack-based buffer overflows. This may result in Denial-of-Service conditions and Remote Code Execution. | FTP server | RCE | 8.8 |
| 2021-31889 | Malformed TCP packets with a corrupted SACK option leads to Information Leaks and Denial-of-Service conditions. | TCP server | DoS | 7.5 |
| 2021-31890 | The total length of an TCP payload (set in the IP header) is unchecked. This may lead to various side effects, including Information Leak and Denial-of-Service conditions, depending on the network buffer organization in memory. | TCP server | DoS | 7.5 |
Siemens has released patches for all the vulnerabilities. Some of those had already been patched in existing versions of the stack but never issued CVE IDs.
As we have seen in NAME:WRECK with CVE-2016-20009 (which we independently found on IPnet and which had never been publicly reported with a CVE ID), vulnerabilities in TCP/IP stacks that have been silently patched may still affect several devices. In the case of CVE-2016-20009 (which as the ID indicates was originally found in 2016) there were several advisories released in 2021 (after the NAME:WRECK disclosure) listing critical vulnerable devices, such as Siemens gas turbines, BD Alaris infusion pumps and GE healthcare devices.
A video showing the effects of exploiting CVE-2021-31886 on Forescout Cyber Lab is available here. More details about some of the vulnerabilities and their exploitation are available on our technical report.
Impact
Nucleus NET is the TCP/IP stack of the Nucleus Real-time Operating System (RTOS). The stack and the RTOS were originally developed by Accelerated Technology, Inc. (ATI) in 1993, then acquired by Mentor Graphics in 2002 and finally by Siemens in 2017. Since its original release, 28 years ago, Nucleus has been deployed in many industry verticals with safety and security requirements such as medical devices, automotive, and industrial systems.
Understanding where the vulnerable code is present is notoriously challenging. We try to estimate the impact of NUCLEUS:13 based on the evidence collected during our research, using three main sources:
- The official Nucleus website, according to which the RTOS is deployed in more than 3 billion devices. A quick look at the page listing customer success stories reveals its use in scenarios such as healthcare (ZOLL defibrillators and ZONARE ultrasound machines), IT (BDT AG storage systems) and critical systems. But we believe that most of those 3 billion are actually device components such as baseband processors used in smartphones and other wireless devices. We also found technical documentation detailing the use of Nucleus for medical devices, such as the GE S/5 Avance Anesthesia Machine and the Nihon Kohden Bedside Monitor.
- Shodan Queries. Shodan is a search engine that allows users to look for devices connected to the Internet. We queried Shodan, looking for devices showing some evidence (e.g., application-layer banners) indicating the use of Nucleus. As shown in Figure 1 and Figure 2, with a query executed on 05/Aug/2021, we found more than 2,200 instances of devices running the Nucleus FTP server (“220 Nucleus FTP”) or the RTOS (“Operating System: Nucleus PLUS”). Interestingly, these are the same queries we used during the NAME:WRECK research and they show a decrease of 13% of FTP servers and 25% of exposed devices running the RTOS. We believe this is a direct positive effect of NAME:WRECK, which most likely brought increased attention to securing publicly exposed embedded devices.
- Forescout Device Cloud. Forescout Device Cloud is a repository of information of 13+ million devices monitored by Forescout appliances. We queried it for similar banners as Shodan, as well as other information, based on DHCP signatures, for instance. We found close to 5500 devices from 16 vendors in 127 customers. 13 of these customers had more than 100 vulnerable devices with healthcare being the most impacted sector.
 Device functions running Nucleus (source: Forescout Device Cloud)
Device functions running Nucleus (source: Forescout Device Cloud)
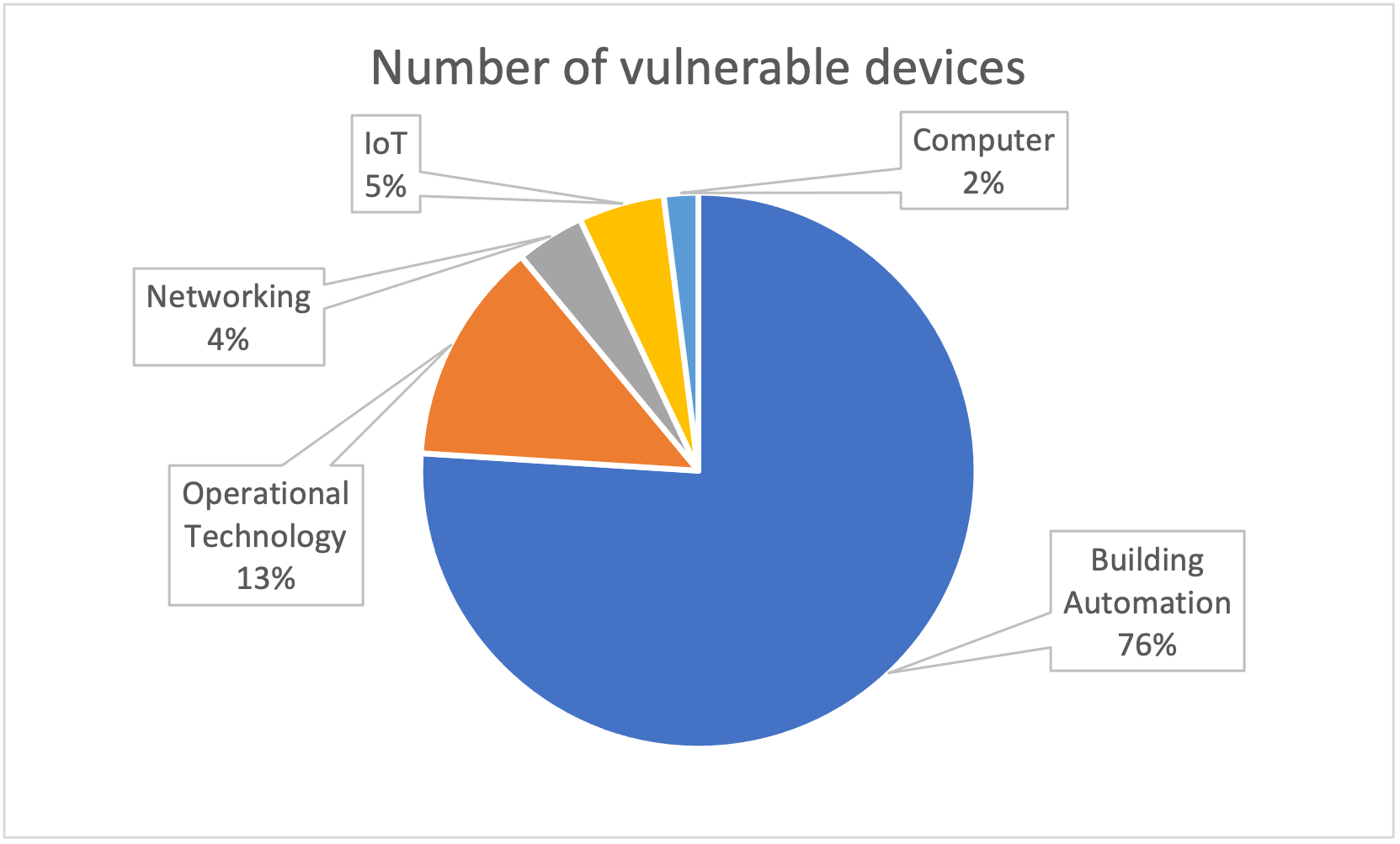
 Devices running Nucleus in each vertical (source: Forescout Device Cloud)
Devices running Nucleus in each vertical (source: Forescout Device Cloud)
As we have done for the previous research, we will maintain a list of advisories related to vendors impacted by NUCLEUS:13 on our GitHub page.
Mitigation Recommendations
Complete protection against NUCLEUS:13 requires patching devices running the vulnerable versions of Nucleus. Siemens has released its official patches and device vendors using this software should provide their own updates to customers. Below, we discuss mitigation strategies for network operators.
Given that patching embedded devices is notoriously difficult due to their mission-critical nature, we recommend the following mitigation strategy:
- Discover and inventory devices running Nucleus. Forescout Research Labs has released an open-source script that uses active fingerprinting to detect devices running Nucleus. The script is updated constantly with new signatures to follow the latest development of our research.
- Enforce segmentation controls and proper network hygiene to mitigate the risk from vulnerable devices. Restrict external communication paths and isolate or contain vulnerable devices in zones as a mitigating control if they cannot be patched or until they can be patched.
- Monitor progressive patches released by affected device vendors and devise a remediation plan for your vulnerable asset inventory, balancing business risk and business continuity requirements.
- Monitor all network traffic for malicious packets that try to exploit known vulnerabilities or possible 0-days. Anomalous and malformed traffic should be blocked, or at least alert its presence to network operators.
The table below provides recommended mitigations for each vulnerability.
| CVE | Affected component | Mitigation Recommendation |
| 2021-31885 2021-31886 2021-31887 2021-31888 |
FTP / TFTP server | Disable FTP/TFTP if not needed, or whitelist connections. |
| 2021-31881 2021-31882 2021-31883 2021-31884 |
DHCP client | Use switch-based DHCP control mechanisms: protocol-aware network switches may be configured to block DHCP responses from rogue servers (“DHCP snooping”). Alternatively, firewalls can be configured in a similar fashion. As a last resort, use static IP addresses. |
| 2021-31344 2021-31345 2021-31346 2021-31889 2021-31890 |
TCP / UDP / IP / ICMP | Monitor traffic for malformed packets and block them. Having a vulnerable device behind a properly configured firewall should be sufficient. |
Forescout Research Labs is available to speak with vendors and asset owners that are affected by these vulnerabilities. If you would like to speak with us, please contact your account manager or send an email to [email protected]
How Forescout can help?
eyeSight uses the Security Policy Templates (SPTs) module to identify and group vulnerable/potentially vulnerable devices. A new version of the SPT package, which can identify devices vulnerable to NUCLEUS:13 can be downloaded here.
Devices in scope for the policy are scanned using active and passive techniques for four protocols (FTP, Telnet, ICMP, and TCP) and can match the policy in three categories: high certainty for FTP or Telnet fingerprint matches, medium certainty for ICMP fingerprint matches, and low certainty for TCP fingerprint matches. Known vulnerable vendor/models that are classified by Forescout also give high certainty matches.
eyeInspect can detect exploitation attempts against devices running Nucleus using the new “NUCLEUS:13 Monitor” script. The figure below shows the alert raised by eyeInspect when it detects an exploitation attempt against CVE-2021-31886.
The results of an example scan are shown in the figure below.

eyeInspect detecting the exploitation of CVE-2021-31886
Security Advisories
You can get up-to-date information about impacted vendors and devices on the following links:
- Project Memoria advisories, maintained by Forescout Research Labs
- ICS-CERT advisory

