Cyberthreat Trends in 2022H1: Threat Actors Observed, New Malware and Active Hacking Groups
In our companion blog post, Vedere Labs analyzed the main ransomware trends we observed in the first half of 2022, including state-sponsored ransomware, new mainstream targets and evolving extortion techniques. Ransomware is the main threat targeting most organizations nowadays. However, three other notable cyberthreat trends also evolved during this period:
- Threat actors – We saw an almost equal split between cybercriminals and state-sponsored actor activity, with the vast majority of malicious activity perpetrated by Russian or Eastern European actors. The main targeted sectors were government and financial services.
- New malware – Significant malware families such as wipers, OT/ICS malware and botnets targeted not only IT systems but also many types of IoT devices.
- Active hacking groups – Because of the ongoing conflict in Ukraine, hundreds of hacktivists perpetrated DDoS and other types of attacks. Alongside the politically motivated activity, other large groups focusing on data exfiltration for financial gains have been active.
Below we analyze each of these trends in more detail. This is not an exhaustive discussion of the current threat landscape, but rather a series of observations about the most relevant activity we have seen. As in the related ransomware post, at the end we discuss how you can bolster your current defensive strategies to account for these developments.
Cybercriminals and state-sponsored threat actors
The figures in this section are based on data from the Forescout Device Cloud, one of the world’s largest repositories of connected enterprise device data — including IT, OT and IoT device data — whose number of devices grows daily. The anonymous data comes from Forescout customer deployments and contains information about almost 19 million devices. More specifically, we look at requests to known malicious domains originating from our customer networks between January 1 and April 20, then match them to known advanced persistent threats (APTs).
Figure 1 shows the percentage of malicious requests based on the threat actor’s country of origin. Russia and Eastern Europe host an overwhelming majority (83%) of the threat actors we observed, followed by China (9%) and Pakistan (5%).
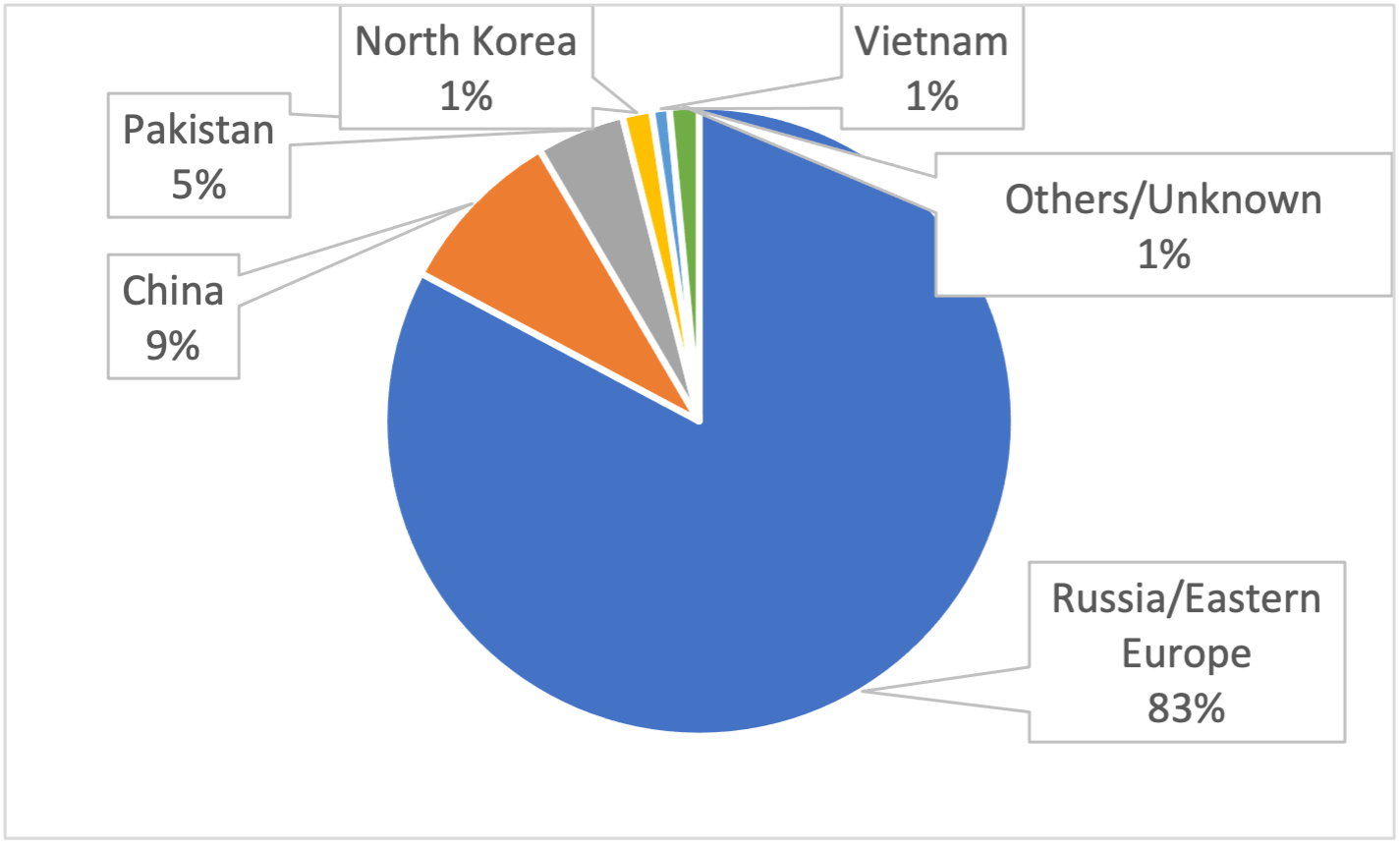
Figure 1 Malicious requests based by threat actor country of origin
We have observed in total 19 threat actors active on monitored networks in the first half of 2022. Known state-sponsored actors accounted for 53% of the activity we observed, and the remaining 47% was due to cybercriminal groups.
The top observed actors were APT29/Cozy Bear, IcedID/Lunar Spider, Evil Corp/Indrik Spider, FIN7/Carbon Spider and Temper Panda. The first four are based in Russia while the last is based in China. The first and last are state-sponsored actors, while the three in the middle are cybercriminals.
The observed actors targeted many different sectors, as shown in Figure 2. Government networks were targeted most often (41%), followed by financial services (28%). Both sectors have long been preferred targets for cyber activities.
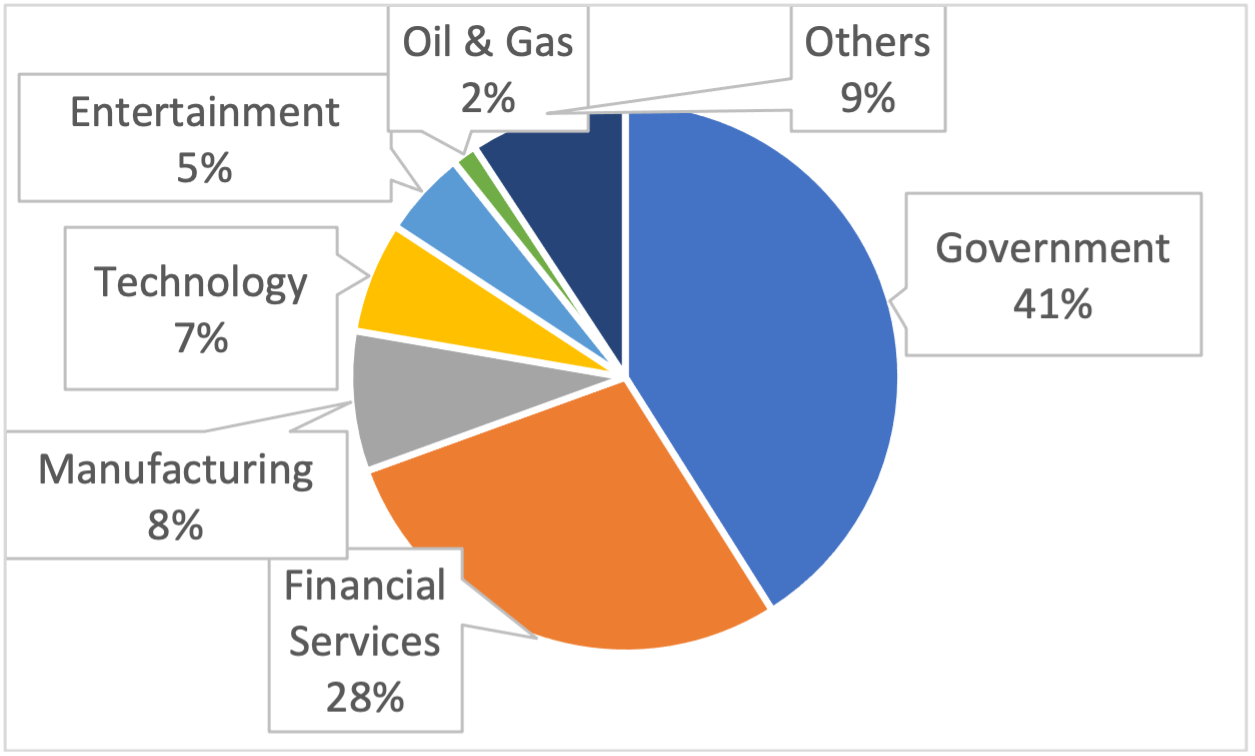
Figure 2 – Malicious requests by targeted sector
New malware – wipers, OT/ICS malware and botnets
Vedere Labs observes thousands of new exploit and malware samples every day, either from public sources or from attacks on our Adversary Engagement Environment, a set of publicly accessible honeypots. Most of these artifacts are variations of known malicious tools, including WannaCry samples – which is still very much active even five years after the initial infections – and exploit attempts on Log4j vulnerabilities – which have recently been declared endemic by a new DHS Cyber Safety Review Board.
The most interesting malware developments typically garner attention because of new malicious capabilities, who is deploying the malware or whom it is targeting – and often because of a combination of the three aspects. Beyond several previously covered ransomware families, the first half of 2022 saw many new relevant malware instances.
Destructive wipers
Several wipers were used for sabotage or to destroy evidence as part of the ongoing conflict in Ukraine. This type of malware typically overwrites or encrypts either files or the master boot record (MBR)/master file table (MFT) of a system. Since their impact is similar to ransomware, often attackers disguise the malware as ransomware by adding fake ransom notes to mislead incident responders or to hide their motivations. The most interesting wiper detected so far this year was AcidRain, which was used against VIASAT KA-SAT modems on February 24, rendering more than 5,000 wind turbines in Germany unable to communicate.
OT/ICS-specific malware
OT/ICS malware continues to abuse insecure-by-design native capabilities of OT equipment. Industroyer2 and INCONTROLLER, two new samples of OT/ICS-specific malware, were disclosed to the public almost simultaneously in mid-April. Industroyer2 leverages OS-specific wipers and a dedicated module to communicate over the IEC-104 protocol for electrical substations, while the INCONTROLLER toolkit contains modules to read/write from/to ICS devices using industrial network protocols, such as OPC UA, Modbus, CODESYS and Omron FINS.
Persistent and emerging botnets
Many botnets either appeared, reappeared or became known for the first time in 2022. Emotet, one of largest botnets ever until its shutdown in 2021, returned with hundreds of thousands of new infections and was distributed in new campaigns using malicious emails. The Cyclops Blink botnet, developed by the Sandworm APT as a possible successor to VPNfilter, was active since 2019 but discovered at the beginning of this year and taken down soon after discovery. Keksec, a criminal group known for operating several botnets, such as Gafgyt and Simps, developed and open-sourced a new botnet called EnemyBot reusing code from Mirai and other botnets with several exploits for IoT devices as well as enterprise IT applications.
Remote Access Trojan (RAT)
ZuoRAT is a recent Remote Access Trojan (RAT) that leverages exposed and vulnerable routers for initial infection, enumerates IT devices connected to the network, then uses DNS and HTTP hijacking to install other malware on the identified devices. Disturbingly, this malware can automatically jump from IoT to IT assets. Researchers have speculated that it is operated by a state-sponsored group because of its complexity.
Hacking groups
Two types of hacking groups were active in the first half of 2022: hacktivists and data extortion groups. Hacktivists are mainly politically motivated, especially because of the war in Ukraine. Data extortion groups are very similar to ransomware gangs in that they focus on exfiltrating data and demanding a ransom to not release it publicly. However, they employ different malware and do not operate a ransomware-as-a-service model.
Hacktivists
More than 100 groups have conducted cyberattacks since the beginning of the Russian invasion of Ukraine. The attacks were mostly DDoS, but also included data breaches, the use of wipers and distribution of propaganda. Some groups claimed attacks on critical infrastructure, such as disabling electric vehicle chargers in Moscow and railways in Belarus.
Most of these groups are located in Russia or Ukraine but others are in Belarus, Turkey, Romania, Poland, Portugal and Italy. They usually communicate and coordinate their actions via Twitter or Telegram. Killnet became the most notorious group, using simple DDoS tools to take down websites of critical infrastructure companies in the U.S. and Europe such as airports, banks and government agencies. They also spread propaganda to more than 100,000 members of their Telegram channel.
Data extortion groups
LAPSUS$ is a hacking group that has been active since 2021 and has breached several high-profile organizations, starting with major Brazilian governmental agencies and companies. In 2022 it moved on to global businesses such as Microsoft, Nvidia and Okta. Following a series of arrests in the UK in March, the group has been mostly silent. Of particular interest were the intensive use of stolen credentials and cooperating insiders for their hacks, as well as their strong social media presence. Other groups focusing on data extortion include RansomHouse and Karakurt. The latter is connected to the Conti ransomware gang.
Mitigation recommendations
The proliferation of IoT devices continues to expand the digital terrains of organizations, without commensurate attention to securing them. Both cybercriminals and state-sponsored actors are well aware of this. Therefore, we recommend that mitigation strategies prioritize securing the increased attack surface based on up-to-date threat intelligence.
The mitigations suggested for ransomware also apply to the threats analyzed here. Additional recommendations include:
- Segment the network to isolate IT and OT, limiting network connections to only specifically allowed management and engineering workstations – thus decreasing the probability of OT/ICS malware reaching its target. Use an OT-aware DPI-capable monitoring solution to alert on malicious indicators and behaviors, watching internal systems and communications for known hostile actions.
- Monitor insider threats, large data transfers and activity in dark nets to prevent or mitigate data leakage by hacktivists and data extortion groups. Monitor especially known data leaks for exposed credentials.
- Use strong and unique passwords and employ multifactor authentication whenever possible to ensure that stolen credentials cannot easily be used against your organization.
- Follow the NCSC-UK’s guide on Denial-of-Service attacks, which includes understanding weak points in your service, ensuring that service providers can handle resource exhaustion, scaling the service to handle concurrent sessions, preparing a response plan and stress testing systems regularly.
- Identify and patch vulnerable IoT devices to prevent them from being used as part of DDoS botnets. Also change defaults or easily guessable passwords on these IoT devices.
- Monitor the traffic of IoT devices to identify those being used as part of distributed attacks.
Besides relying on protection of assets and identification of attacks via intrusion detection, hunt for threats in your network using specific IoCs and known TTPs, such as the use of valid credentials from unknown endpoints followed by large data transfers for hacking groups.
Threat hunting and incident response
Forescout Frontline is a threat hunting, risk identification and incident response service for organizations that lack the internal resources and visibility to defend themselves from or respond to cybersecurity attacks. Forescout Frontline works in close collaboration with Vedere Labs, leveraging the intelligence we provide to identify ongoing attacks in real organizations.