Cyber threats do not always come from outside an organization. Insiders, including current and former employees, contractors and other business partners with authorized access to your network, systems or data can pose significant risk, damage your reputation or even cause financial losses and business disruption. Insider threat incidents are on the rise and organizations affected by them spend on average $15.4 million on mitigation efforts.
There are four types of insider threats, with the first two being the most common:
- Malicious insiders, who intentionally misuse their access
- Accidental insiders, who unintentionally harm the organization
- Negligent insiders, who cause harm through neglect or poor judgment
- Compromised insiders, who had their access used for malicious purposes without their knowledge or consent
Insider threat motivations vary, but common reasons include financial or personal gain, revenge, political or ideological beliefs, lack of job satisfaction or lack of awareness. The LAPSUS$ hacking group shows that even loose groups of hackers motivated by financial gain and without developing sophisticated tools or hacking techniques can cause serious damage to organizations. At the beginning of 2022, LAPSUS$ breached several high-profile companies using credentials obtained from their employees via social engineering or by directly paying for access.
DHS’s Cyber Safety Review Board (CSRB) just concluded a thorough review of LAPSUS$ attacks indicating that “the exploitation of insiders […] in the supply chain of many organizations, especially, added an extra level of complexity for mitigating the attacks across the broader ecosystem.”
These threats are difficult to identify because insiders have legitimate credentials and access permissions. Therefore, it is important to understand normal behavior and be able to detect suspicious activities. In this blog post, we focus on how to hunt for insider threats in your organization and how Forescout can help that process.
Insider threat indicators
Insider threat indicators are red flags that an insider may be carrying out an attack or planning to do so. Recognizing these indicators can help you prevent or respond to potential insider threats. Some common insider threat indicators include:
- Privileged user login outside normal working hours is suspicious if the user is accessing sensitive information or systems without a valid reason. This can lead to unauthorized changes, data theft or disruption of operations.
- Anomalous number of bytes out over social media or file-sharing sites can indicate that sensitive information is being exfiltrated, if that is unusual for the user or network.
- Use of steganography tools can indicate the user is attempting to hide or encode sensitive information within digital media, such as images or audio files, for exfiltration.
- Emails sent to private addresses may contain sensitive information shared outside of your approved channels.
- Removable media, such as a USB drive, CD or external devices, may be used to transfer sensitive information from your systems.
- Excessive screenshot activities may indicate the user is collecting sensitive information from your systems.
- Internal network scanning activity can indicate that a user is attempting to gain unauthorized access to sensitive information.
- Access to public VPN/proxy servers can indicate an insider threat, as they can bypass security controls and conceal the user’s identity and location.
- Logon attempts to disable accounts may suggest that an employee is trying to log in using a specific disabled user account to gain access to sensitive information or to disrupt your systems.
- Attempt to disable security controls can suggest that someone is trying to bypass security measures to gain unauthorized access to sensitive information or cause disruption.
- File operation over confidential files can suggest that the employee is accessing or attempting to access sensitive information that they are not authorized to view.
- Attempt to hide/delete digital records or files can suggest that the employee is trying to cover up or remove evidence of potentially malicious activity or sensitive information.
How to hunt for insider threats
Hunting for insider threats is challenging because insiders have legitimate access and may not exhibit obvious signs of malicious activity. However, there are warning signs that you can look for:
- Abnormal access patterns: Detect changes in user access patterns, such as accessing sensitive data outside of normal working hours or downloading large amounts of data.
- Suspicious communications: Monitor internal communications, such as emails and chat logs, for signs of intellectual property theft, attempts to solicit confidential information or other suspicious behavior.
- Security incident response: Investigate any unusual or suspicious incidents, such as data breaches or system failures, to determine if an insider may be involved.
- Data loss prevention: Detect and prevent attempts to transfer sensitive information outside of the organization, such as sending confidential data to a personal email address.
- Privileged account monitoring: Monitor privileged user accounts, such as system administrators, to detect unauthorized access or abuse of privileges.
- File and system activity: Monitor file and system activity, such as changes to system configuration or the creation of new files, to detect potential insider threats.
- Data access anomalies: Detect unusual data access patterns, such as accessing data outside of normal working hours or accessing large amounts of data in a short period.
- File type anomalies: Detect changes in file type usage, such as an increase in the number of executable files being created or downloaded.
- Data access by terminated employees: Detect and prevent access by terminated employees to sensitive data.
- Unusual network traffic: Monitor network traffic for unusual patterns, such as large amounts of data being transferred outside of the organization.
- Unusual user account changes: Detect changes to user accounts, such as changes to user permissions or changes to account settings, to detect potential insider threats.
- User login anomalies: Detect unusual login patterns such as multiple failed logins attempts or logins from unexpected locations.
How does Forescout help detect insider threats?
The Forescout Platform helps organizations detect and respond to all types of cybersecurity threats, including insider threats – continuously and automatically. Forescout Threat Detection & Response, the extended detection and response component of the platform, collects and analyzes large amounts of data from multiple sources, such as network logs, endpoint activity and cloud security events, to identify unusual behavior and potential security incidents. Features that help detect and respond to insider threats include:
- User and device behavioral analysis: Forescout Threat Detection & Response uses cross-product correlation, user and entity behavior analytics (UEBA) and baselining to analyze user and device behaviors. This helps you quickly detect and respond to unusual or suspicious activity, including potential insider threats.
- Automated response: Forescout Threat Detection & Response provides automated response capabilities that can be triggered based on specific security events or incidents. This helps you respond quickly to potential insider threats without the need for manual intervention.
- Integrations with security tools: Forescout Threat Detection & Response integrates with a wide range of security tools, such as firewalls, intrusion prevention systems (IPS) and security information and event management (SIEM) systems. This integration enhances your overall security posture and helps provide a more comprehensive view of potential insider threats.
- Cloud security: Forescout Threat Detection & Response provides cloud security capabilities that help you secure cloud-based resources and applications. This includes the ability to detect and respond to potential insider threats that occur within cloud environments.
Detect and respond more efficiently to all types of true threats – including insider threats.
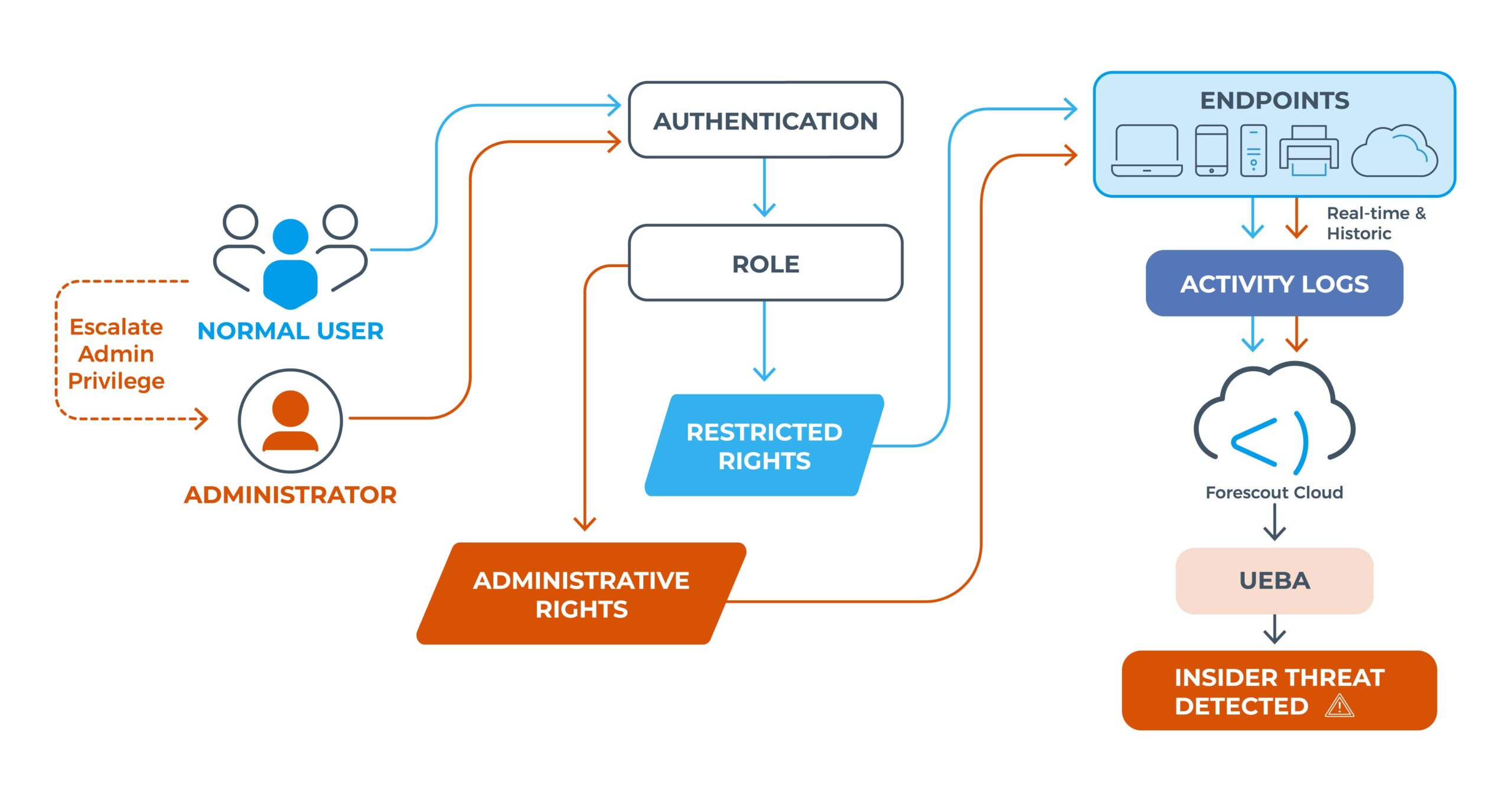
Insider threat detection model in Forescout Cloud
The best way to reduce negligent insider threats
Threat detection analytics and related capabilities grow more sophisticated every year. They must if organizations want to keep pace with – and outsmart – constantly evolving TTPs. For one type of insider threat, you have an even more powerful tool in your toolbox: cybersecurity awareness training.
One of the conclusions of the CSRB review of LAPSUS$ is that “employee awareness and insider risk management factored heavily into whether organizations defended well against this class of threat actors.”
As mentioned earlier, negligent insider threats aren’t always caused by malicious behavior, but they nonetheless open the door to malicious attacks. According to one study, 56% of insider incidents are caused by negligent employees or contractors – compared to 26% caused by malicious insiders.
Offering quarterly, interactive cybersecurity awareness training can go a long way to change employee behavior, perhaps not initially but definitely over time. It’s also one of the best ways to reinforce a security culture and foster healthy suspicion. As a bonus, a high-profile, proactive culture of security may discourage malicious insider threats.