Securing the unseen: MITRE’s EMB3D framework for embedded devices
The security of embedded devices is in the news over the last few years, especially IoT assets and OT systems. From connected medical devices to industrial control systems to smartwatches and building automation, connected IoT devices will expand to over 25 billion by 2028.
Critical infrastructure is under siege at 13 attacks per every second. The Executive Branch’s Executive Order 13636 and the more recent CISA Secure By Design initiatives all point to the need to protect against sophisticated attacks using embedded devices.
Here is the good news: Manufacturers and security teams in every industry now have a new model to help organize and better manage what often goes unmanaged.
The MITRE Corporation has officially launched its new threat-modeling framework, EMB3D, for manufacturers of embedded devices in industries, such as critical infrastructure, IoT, manufacturing, healthcare and others. To increase the security posture of embedded assets, MITRE aims to be a central repository of information on known threats to embedded devices and their unique features and properties.
End users can map associated threats to unique features and properties of embedded devices — and then build comprehensive mitigation strategies to secure unmanaged devices.
Breaking down MITRE’s new EMB3D framework for embedded devices
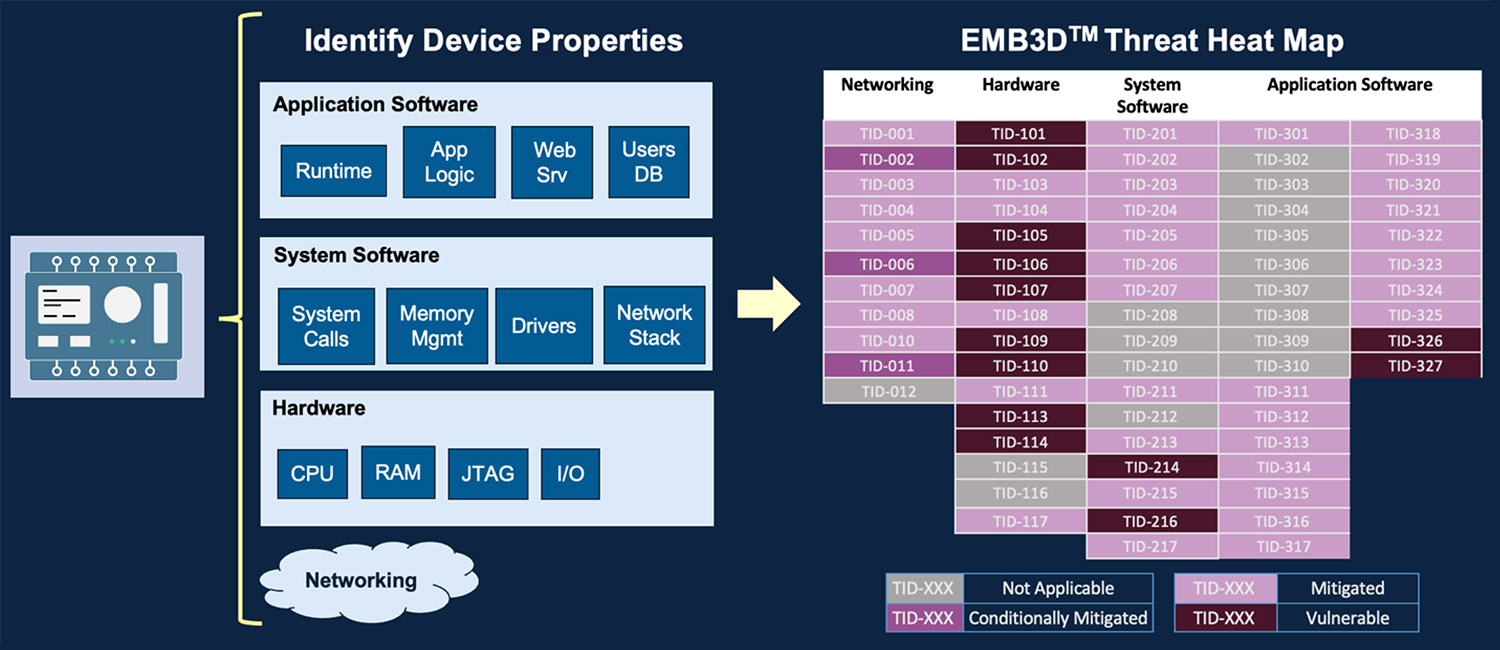
EMB3D expands on existing models including MITRE’s ATT&CK framework and Common Weakness Enumeration. It is designed to be a ‘living framework’ that can be updated with new TTPs, threat actors, mitigations and campaigns discovered with a focus on embedded devices. EMB3D breaks it down into three steps:
- Enumerate device properties and map to threats
MITRE aims to provide a detailed list of a device’s hardware, software, and capabilities. These include physical hardware, network services and protocols, software, and firmware. These categories are broken into subcategories and mapped to a set of threats that users can identify based on sets of properties. - Enumerate threats and evaluate their relevance/risk
Each threat will identify how a threat actor can expose a system or device to the required technical features and the impact or effects the threat will have on the device. - Identify required mitigations
Each threat will have a mitigation strategy that allows manufacturers and users to validate that the devices are properly protected against each threat. When the framework is updated later this summer, EMB3D will provide foundational, intermediate and leading mitigations to provide guidance on the technical mechanisms to best prevent or reduce the risk of the threat.
Examples of using MITRE’s EMB3D framework for embedded devices
Here is how the framework can be used today. See the device properties mapper with the following categories:
- Hardware
- System software
- Application software
- Networking
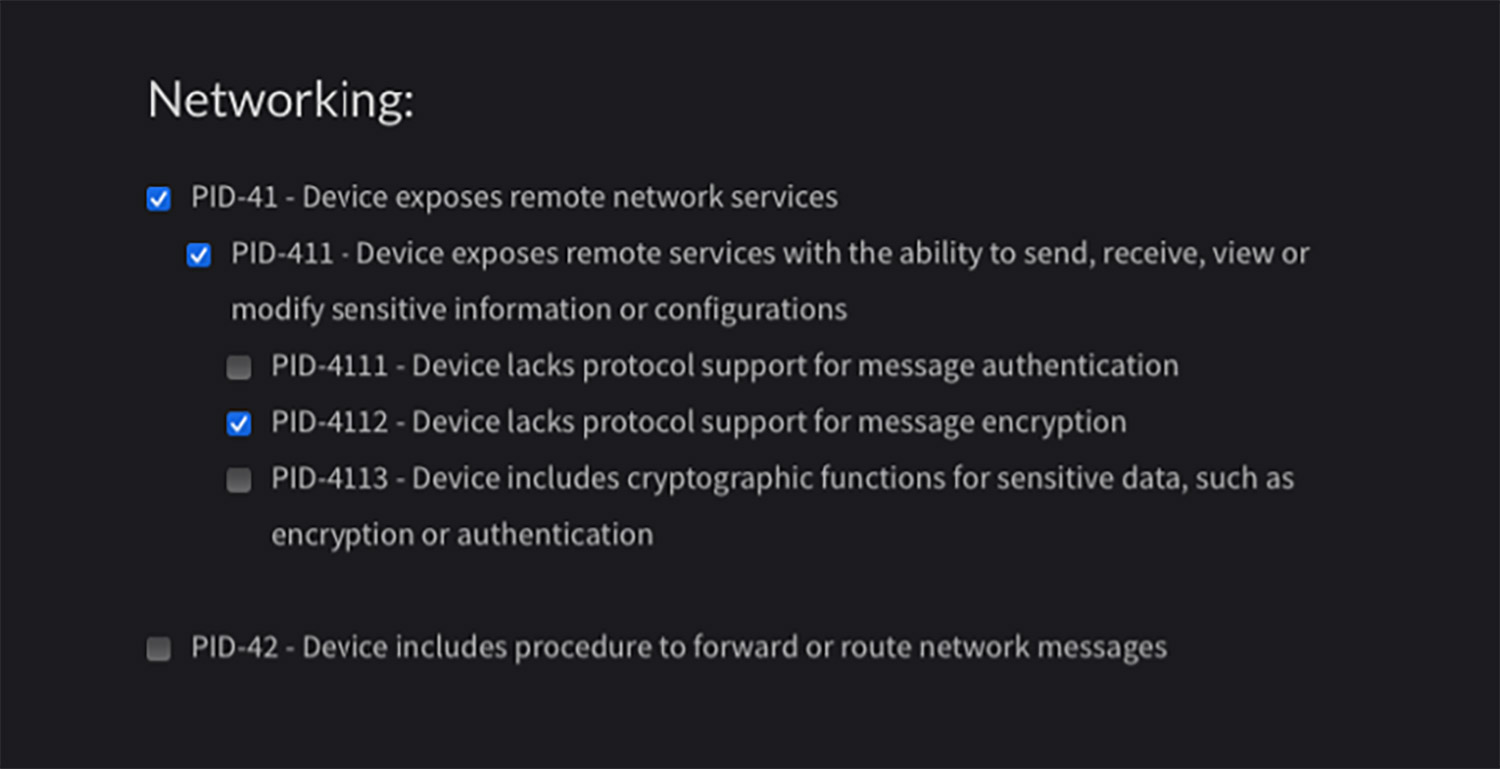
If you choose networking, EMB3D allows you to choose device properties that correlate to the types of devices you have within your network. Those properties can then be further broken down into sub-properties.
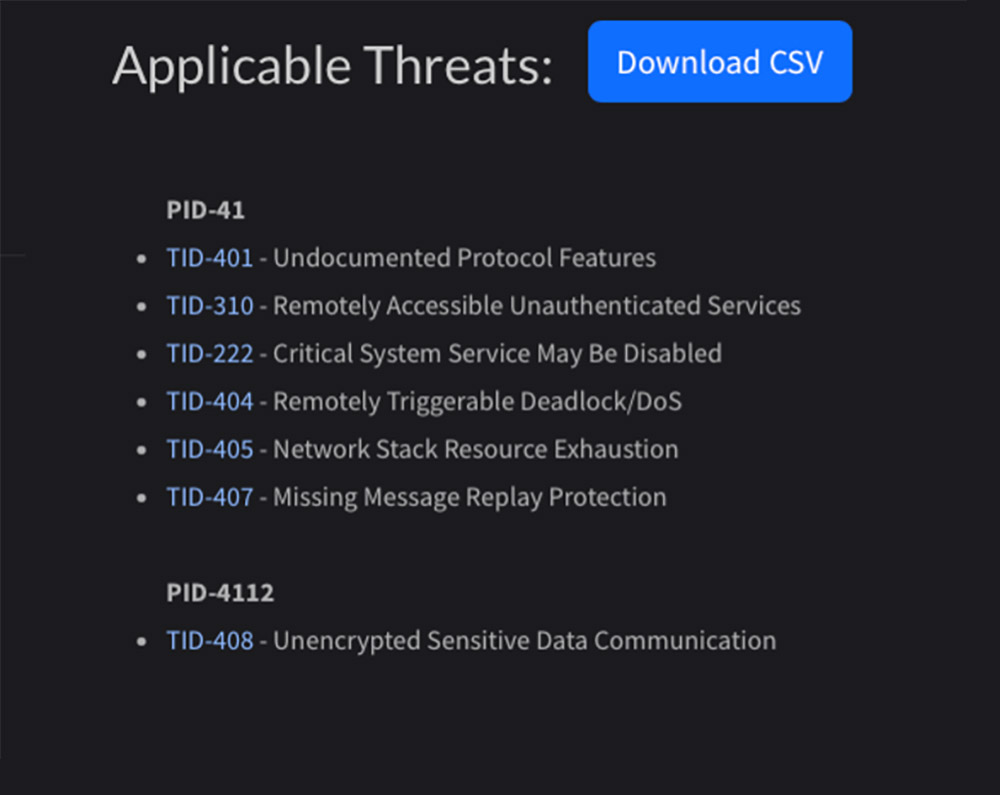
EMB3D will map these properties directly to known threats.
For example, clicking on TID-408 will give a detailed overview of the threats and potential exploit mechanisms.
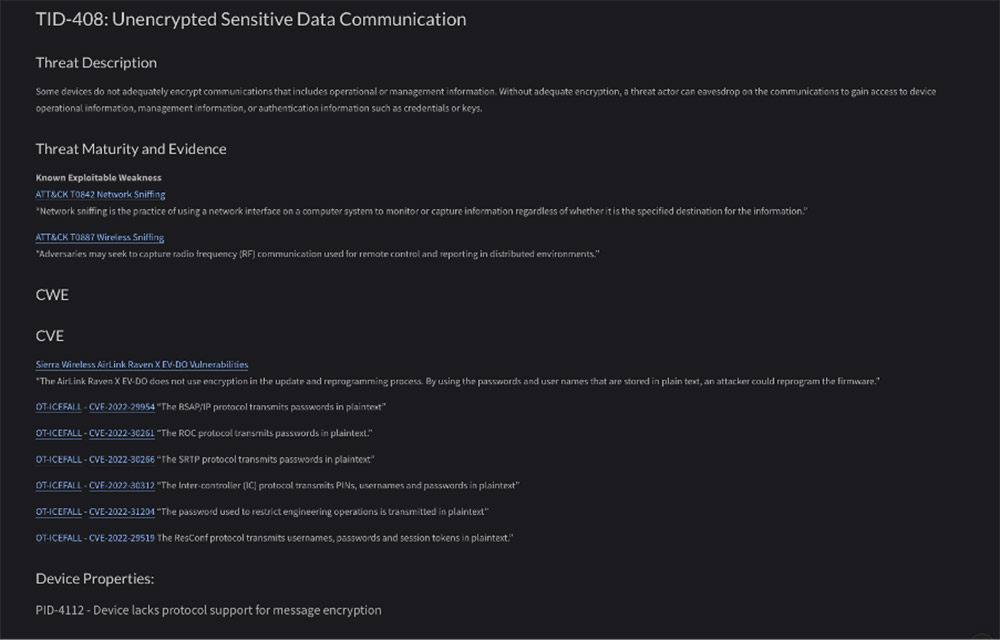
Here you can see these device properties are directly linked to threats that correlate to the OT:ICEFALL vulnerabilities published by Forescout Research – Vedere Labs.
Embedded devices in MITRE’s EMB3D framework: What is in and out of scope?
MITRE defines the scope of embedded devices in a detailed white paper. Also included in this paper are details on device properties, threat properties, technical mitigations and maturity tiers:
“Embedded devices include a broad set of unique technologies used within embedded applications, along with dependencies on more diverse technologies used across general computing platforms/environments. Therefore, the scope will include both categories, as defined”:
Properties of Defined Technologies and Platforms
In Scope
- Unique to critical infrastructure embedded equipment and environments, such as the execution of custom logic/programs (e.g., IEC 61131).
- Frequently observed in embedded device environments due to foundational use across computing/networking, including protocols (e.g., HTTP, TCP/IP, HTTP, SQL).
- Hardware (e.g., USB, JTAG, FPGA).
- Software (e.g., operating systems functions, firmware, memory management) .
Out of Scope
- Minimal/no documented use in embedded platforms, such as cloud or mobile platforms.
- Specific to vendors or product lines, including specific design technologies by Microsoft or specific embedded device vendors.
This framework shines a light on an area in organizations that will help mature their security posture and provide mitigation strategies for unmanaged assets that power their business.
You can give the full framework a read at the MITRE website.
See how the MITRE ATT&CK framework integrates within Threat Detection & Response.