In the last few weeks, there have been a few announcements made about a new malware threat known as FrostyGoop or BUSTLEBERM (as it was originally tracked by Mandiant). It is being recognized as the first custom malware to integrate Modbus for the purpose of causing physical damage. An associated incident has been reported where the malware was used to disrupt heating in Ukrainian homes in the context of a Russian cyberattack.
The news has rightfully garnered significant attention within the cybersecurity community, as attacks like the one where the malware was reportedly used are far reaching and could result in significant disruptions to business, financial loss, and in some cases a danger to human lives, depending on the critical nature of the targeted infrastructure.
Reports by Dragos and other industry leaders emphasize the uniqueness of this threat as something new. Yet, upon further investigation, the underlying techniques used are far from unique. In fact, FrostyGoop/BUSTLEBERM is a variation or continuation of well-documented tactics, techniques and procedures (TTPs) that we and other researchers have observed in previous cyber incidents.
Examining the ICS Malware FrostyGoop/BUSTLEBERM News: Should You Care?
The potential for widespread disruption and the real risk to human lives make it imperative for businesses and organizations to stay ahead of OT-specific malware and threats, but also to ensure that they are not caught off guard by what may appear to be new but is, in fact, a well-established method of attack that could be detected or prevented.
Although FrostyGoop/BUSTLEBERM is a real threat, well-known researchers have raised some questions about the malware and reported incident. Here’s why:
- The impact of the attack was probably different than what has been widely stated in the media.
While there were reports of 600 households with no hot water and heating for a couple of days, the actual incident in Ukraine – based on public information shared by Marina Krotofil – may have affected fewer homes for a shorter period of time.
- There is a discrepancy between the technical capabilities of the actual malware and what happened in the stated incident.
The incident report mentions things like firmware downgrade and exploiting routers for initial access that are not part of the malware capability and that are not detailed at all. Overall, it is challenging to connect the publicly available piece of malware – found on VirusTotal as described below – to the described incident.
Organizations should be aware of and take action to mitigate attacks abusing OT protocols, but understanding real impacts and capabilities is important to take appropriate decisions on which controls to prioritize and which risks to mitigate.
FrostyGoop/BUSTLEBERM: Under the Hood
While FrostyGoop/BUSTLEBERM is reported as the first malware intentionally crafted to exploit the Modbus protocol for destructive purposes, this is not the whole story. The use of Modbus in cyber-attacks is far from new. Historically, hacktivist groups including GhostSec have leveraged tools, such as Metasploit and custom scripts (KillBus and theComposer.py) to target OT environments, including in Russia as early as 2022.
Additionally, Forescout Research – Vedere Labs research has consistently highlighted Modbus as the most scanned and attacked OT protocol we observe. In 2023, 33% of OT protocol interactions observed on our Adversary Engagement Environment targeted Modbus, underscoring its appeal to threat actors. This makes the Modbus-related capabilities of FrostyGoop/BUSTLEBERM less groundbreaking and more a natural evolution of existing threats.
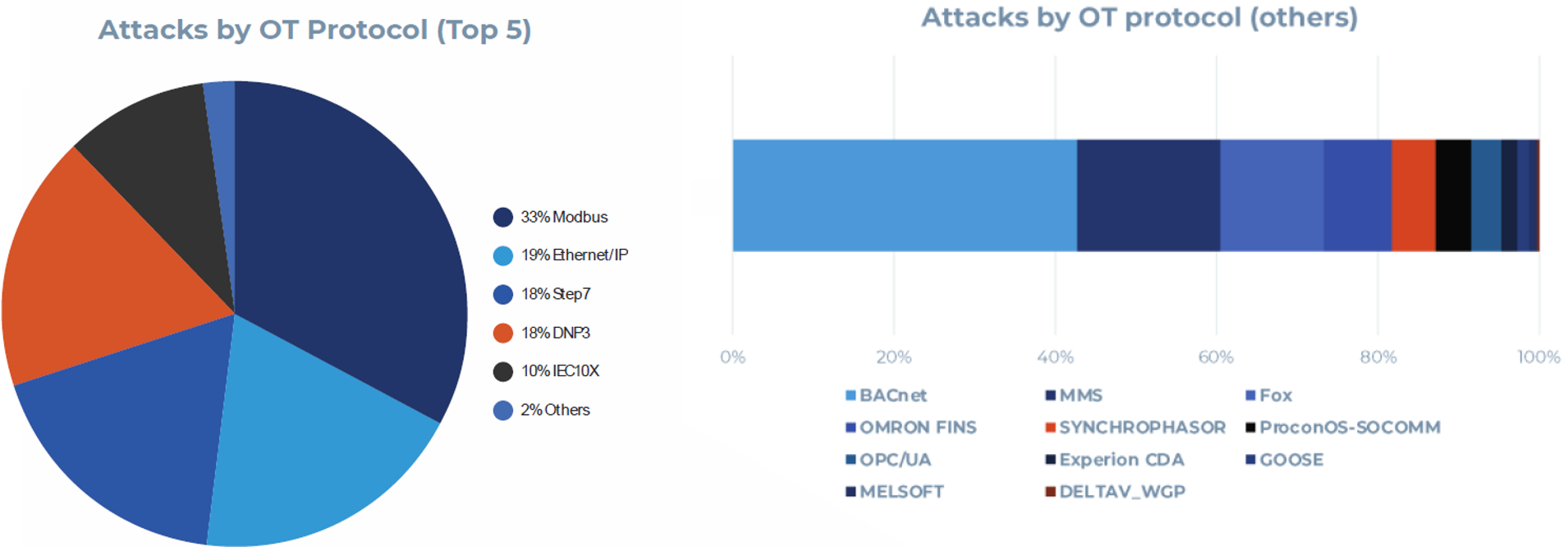
Figure 1 – Attacks to OT protocols on Forescout’s Adversary Engagement Environment (AEE). From our Threat Roundup 2023.
Soon after the publication of the FrostyGoop report, Florian Roth shared with the community a YARA rule used to find the sample on VirusTotal. That rule currently matches two executable files:
- This file was first uploaded from Russia on October 30, 2023 with the filename “mb.exe”:
https://www.virustotal.com/gui/file/5d2e4fd08f81e3b2eb2f3eaae16eb32ae02e760afc36fa17f4649322f6da53fb
- This file was first uploaded from the United States on October 30, 2023 with the filename “read-all-mb.exe”:
https://www.virustotal.com/gui/file/a63ba88ad869085f1625729708ba65e87f5b37d7be9153b3db1a1b0e3fed309c
The two samples seem identical in behavior. The difference? The second one included junk sections. The first sample was built with Golang 1.19 (released in 2022) while the second was built with Golang 1.20 (released in 2023). The malware does not implement obfuscation or static or dynamic analysis evasion techniques.
The core functionality of the malware is to interact with machines using Modbus/TCP over port 502. It can read holding registers (Modbus function code 0x03), write to a single register (Modbus function code 0x06) and write to multiple registers (Modbus function code 0x10). In essence, the malware can be used to directly interact with and potentially disrupt processes that incorporate Modbus, since the protocol does not require authentication. It can also read instructions from a JSON file. However, it has no capability to exploit vulnerabilities or modify firmware of any targets.
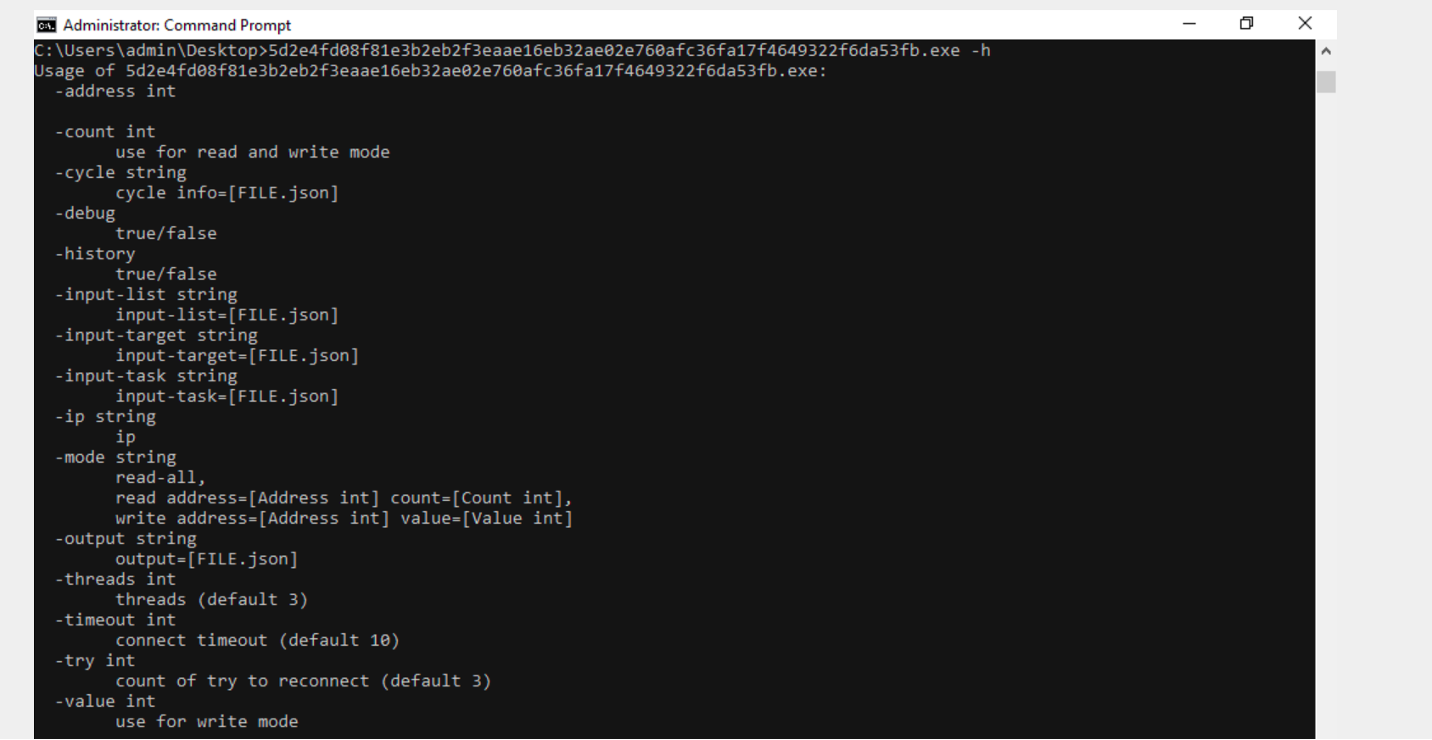
Figure 2 – Screenshot of the malware functionality list
The State of OT Security: A Broader Perspective
The emphasis on FrostyGoop/BUSTLEBERM as a unique threat overlooks the broader context of OT security. The use of open-source components like the Go library for Modbus in FrostyGoop/BUSTLEBERM mirrors earlier malware. Industroyer2, for example, is a C++ library for IEC-104 communication that has been utilized. This pattern of relying on open-source tools is a recurring theme in many OT-targeted attacks. The true innovation lies not in the exploitation of Modbus itself but in the ongoing refinement and application of these tools by cybercriminals and state-sponsored actors.
Furthermore, the discovery of FrostyGoop/BUSTLEBERM in a public repository is similar to the finding of COSMICENERGY in 2023, which was identified more than a year after it was first uploaded. This recurring pattern hints that other, as-yet-undiscovered malware strains may be lurking in public repositories waiting to be exploited by malicious actors.
Looking Ahead: ICS Malware and OT Security
Raising awareness is always beneficial. FrostyGoop/BUSTLEBERM is a noteworthy threat within the world of OT security. However, it is not as unprecedented as some reports might suggest. The TTPs employed by FrostyGoop/BUSTLEBERM are familiar, rooted in numerous Modbus-related attacks and the use of open-source tools for OT protocol interactions.
As the cybersecurity community works to mitigate the risks posed by FrostyGoop/BUSTLEBERM, it’s crucial to recognize that this malware is just one piece of a broader, evolving threat landscape. Rather than viewing FrostyGoop/BUSTLEBERM as an isolated incident, we should consider it further proof of the need for increasingly resilient OT security measures in the future.
Mitigation Recommendations : How Forescout Helps
To mitigate the risks of attacks targeting operational technology, including those abusing Modbus, organizations should:
- Identify every device on the network and their communications to understand what protocols are used and who those devices communicate with, which allows to assess the risk a specific device and protocol brings to the organization.
- Segment the network to isolate IT, IoT and OT devices, limiting network connections to only specifically allowed management and engineering workstations or among unmanaged devices that need to communicate.
- Monitor the network using an OT-aware, DPI-capable solution to alert on malicious indicators and behaviors, watching internal systems and communications for known hostile actions such as vulnerability exploitation and unauthorized use of OT protocols.
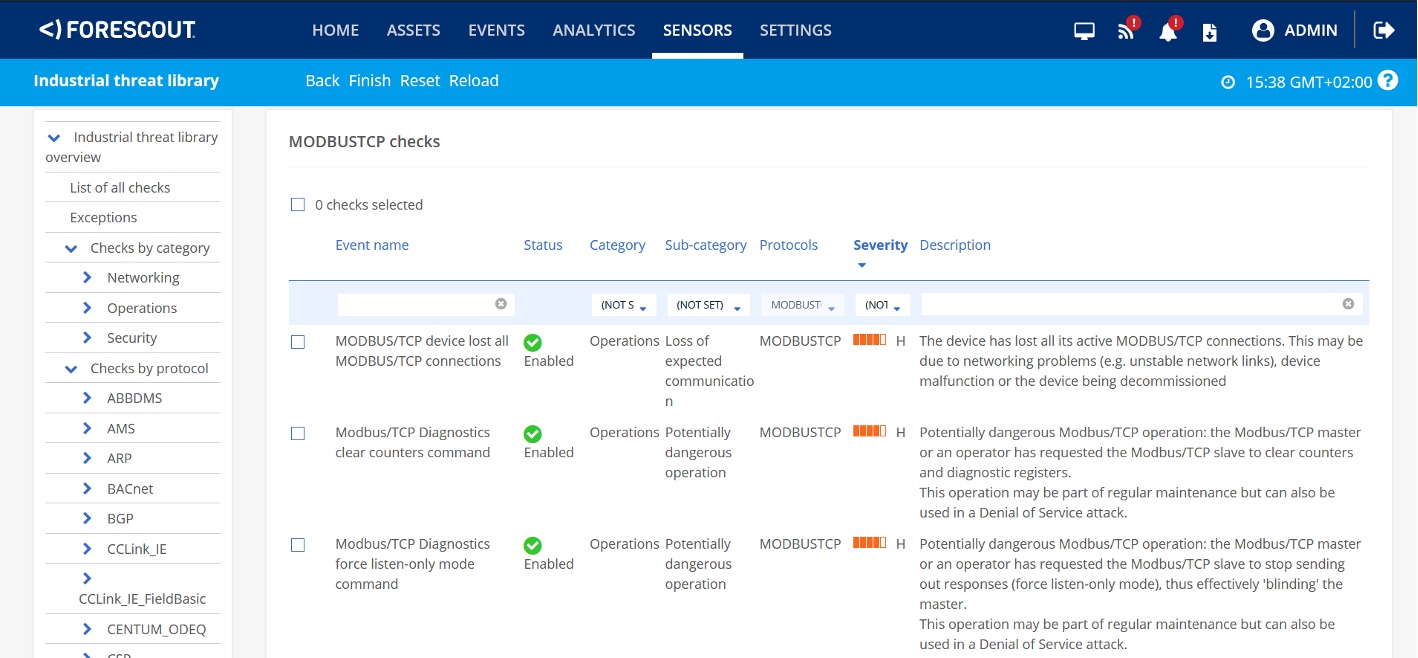
Forescout eyeInspect includes more than 50 different checks for Modbus/TCP communication that may be anomalous or potentially dangerous, including commands to restart communications, new connections from engineering stations and firmware replacement.
A YARA rule used to detect FrostyGoop/BUSTLEBERM was also added to the monthly release of eyeInspect’s IoC database.
Go deeper: See how Forescout stacks up against other OT security providers.