Cyber Skills Shortage? The Time for Security Automation Is Now
Many industries are affected by skills gaps, but according to Cybersecurity Ventures, the shortage within the IT/cybersecurity sector is nearly unmatched: Over an eight-year period, the number of unfilled cybersecurity jobs increased from one million positions in 2013 to 3.5 million in 2021. The researchers predict this skills gap will hold steady through 2025, but that’s cold comfort for strapped security operations center (SOC) teams who must keep up with mounting workloads – and CISOs who are under immense pressure from their corporate boards.
Fortunately, many of the routine tasks traditionally handled by SOC teams can be translated into automated policies that drive orchestrated actions among these products.
Challenges driving the need for security automation.
In addition to the cyber skills shortage, a confluence of internal and external challenges has accelerated organizational timelines to automate whatever can safely be automated. They include:
- Exponential growth of connected devices. The number and types of cyber assets that organizations must deal with has exploded in recent years, creating an ever-expanding attack surface. The vast majority are IoT and OT, which aren’t designed to be supported using traditional IT methods, such as patching. This creates a seriousvisibility gap that leads to an inaccurate assessment of risk.
- Rapidly evolving threat landscape. Cyberattacks have evolved to include large extortion campaigns by sophisticated ransomware gangs, often operating a ransomware-as-a-service (RaaS) model that can cripple the operations of several types of organizations at once.
- IT/OT convergence. Industrial digitalization requires IT/OT convergence. But without proper segmentation and other controls, communication links go unchecked and vulnerabilities hide in plain sight, based on the assumption that OT and IT are separated when they are not.
- Siloed point security products. The typical organization has dozens of IT and security products operating independently. Each one lacks sufficient device context or the ability to carry out a coordinated response to security risks and threats.
- Alert fatigue. Security teams are overwhelmed with alerts from point security products. They must manually sort through a cacophony of uncategorized, unaggregated and unranked alerts to suss out policy violations and vulnerabilities that pose true risk and prioritize response.
- Unactionable alerts. Alerts are just that: alerts. At Forescout, we hear all the time from SOC managers, “Our tools send alerts but don’t fix the incidents automatically,” and, “Our systems can detect risk but can’t mitigate it.” Battling alert fatigue only to perform rote, menial tasks can wear down even the most dedicated staff.
- No single source of truth. Troubleshooting an issue typically requires a cross-functional team (network, server and security) to consult multiple consoles and dig into disparate logs for additional contextual information. (What wireless controller is affected? Which RADIUS server? What type of authentication?) The logs typically don’t show compliance status of the endpoint, and none of the tools provide information about mobile, BYOD and other non-managed devices.
Together, these challenges prolong that all-important metric: mean time to response (MTTR).
Security automation in action
Security automation helps SOC teams enforce device compliance, reduce the attack surface and rapidly respond to incidents. It arms not just the team but the applications and networks themselves with the ability to respond immediately when risks and threats are identified.
The Forescout Continuum Platform takes serially performed tasks and automates them to occur continuously. A task that takes multiple people hours to perform for each asset can be converted into a policy that can be executed in bulk, in real time or on an interval.
Manual vs. Automated Security
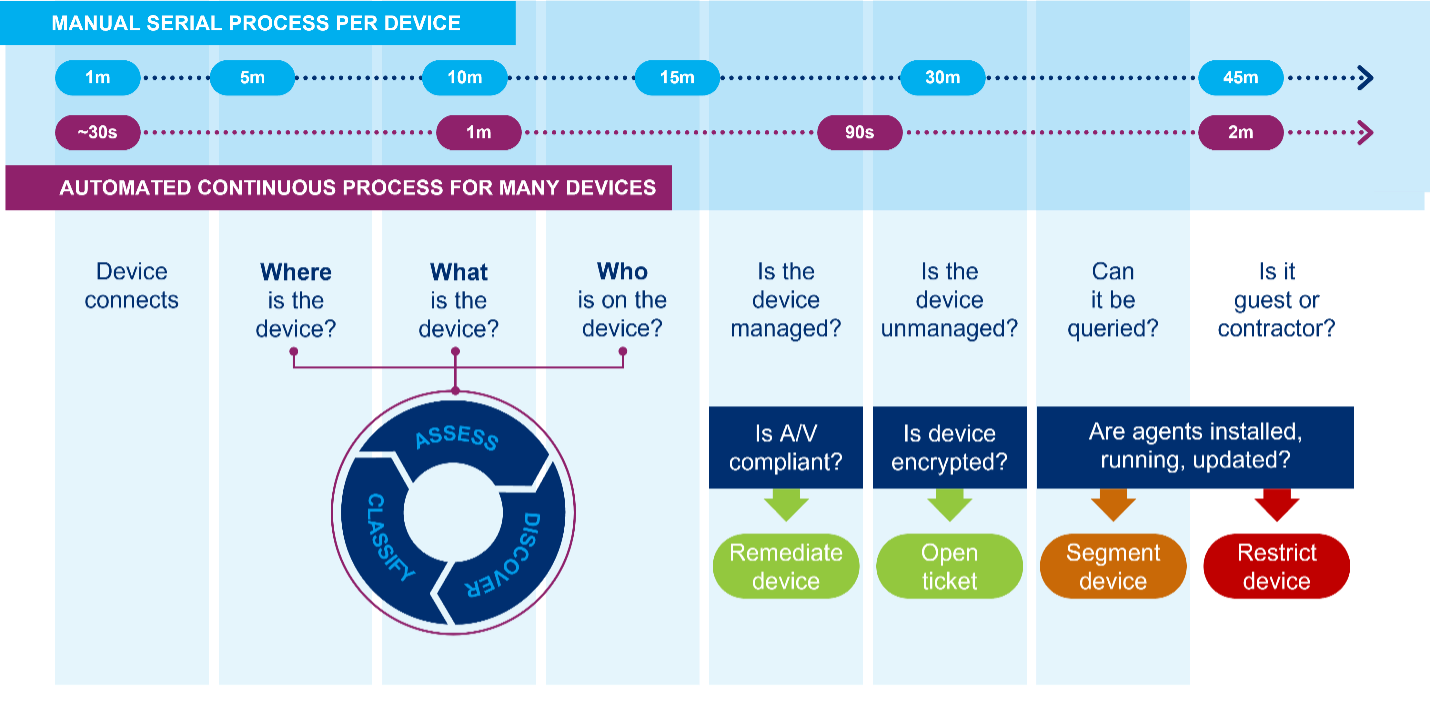
Figure 1
Figure 1 compares a manual, serial process to discover, assess and govern a device vs. an automated process that does the same thing for many devices, continuously. Manually, it takes up to a minute to discover that a device has even connected to your environment – assuming you know what you’re looking for and have a rough idea of where it is. It takes up to 15 minutes to understand where it’s connecting, what it is and who is using it. Depending on whether the device is managed or unmanaged, add another 10-15 minutes to determine whether it’s compliant and, if not, take steps to remediate it or manually open a ticket. Based on our experience, it may take as long as 45 minutes to determine if and how a single device needs to be mitigated or remediated.
In contrast, an automated security process can continuously:
- Detect new assets the instant they connect to the network
- Auto-classify them
- Assess their posture against security policies
- Share their context across security tools
- Automate workflows among them to apply controls and enforce compliance
All in less than two minutes.
The 3 components of optimal security automation
The Forescout Continuum Platform can continuously share device context, automate workflows and accelerate response actions, leaving SOC teams to focus on what requires human intervention.
Share device context
Complete visibility is the foundation of any cybersecurity strategy – to automatically share device context with other security tools you must first gather that context. For example, your configuration management database (CMDB) can only serve as a single source of truth if it is continuously refreshed as new assets join and leave the network or configurations change. The Continuum Platform gathers and shares real-time device context with more than 70 other IT and security products, including CMDB, EPP/EDR, VA, SIEM, ATD, NGFW, PAM, CMT and ITSM.
Automate workflows
When all security products share the same device context, their actions can be orchestrated to automate system-wide policy enforcement and accelerate response. Automated workflows can be designed to:
- Trigger real-time vulnerability scans for transient devices upon connect
- Execute labor-intensive tasks such as scanning and patching
- Verify endpoint agents are installed, up-to-date and functioning properly
- Detect stale or illegitimate privileged accounts on connecting devices
Accelerate response actions among existing tools
That sea of unactionable alerts? Cutting through the noise to prioritize true alerts is the first step to accelerating response. Forescout Continuum prioritizes alerts based on both risks and threats:
- Multifactor risk scoring. Upon assessing and classifying each asset, Forescout Continuum calculates a multifactor risk score based on configuration (compliance, vulnerabilities, open ports) and behavior (internet exposure, malicious traffic) and function (criticality, proximity to other devices). For OT assets, we calculate dual, impact-based scores: one for SOC teams (cybersecurity risk) and one for OT operators (operational risk).
- Advanced threat detection. The Continuum Platform collects large amounts of data about the assets and network communications in your digital terrain. Our advanced threat detection engine then combs through that data and analyzes it to detect and raise only material threats.
These prioritized risk scores enable you to make informed decisions, select the right actions and automate response across tools. They include insights and recommendations for initiating policy-based mitigation and remediation workflows in real time, such as containing, quarantining or blocking vulnerable, compromised and high-risk devices.
Hours instead of minutes
The cybersecurity skills gap, exploding number and type of connected assets and evolving threat landscape have compelled SOC teams to embrace security automation so they can focus instead on what can’t be automated.
Read how New Jersey Transit saves time with automated asset inventory and device compliance, plus accelerated remediation and incident response.