Here are the major cybersecurity challenges facing the manufacturing industry today – with guidance on what to do.
Executing cybersecurity in manufacturing environments can feel like an uphill battle. With ransomware lurking in the shadows and supply chain risk constantly evolving, it’s easy to feel overwhelmed. Compliance regulations only add more pressure, leaving many wondering where to even begin.
The real challenge? Shifting your cybersecurity program from reactive to proactive.
Your operation is either building resilience or increasing its risk exposure, there’s no middle ground.
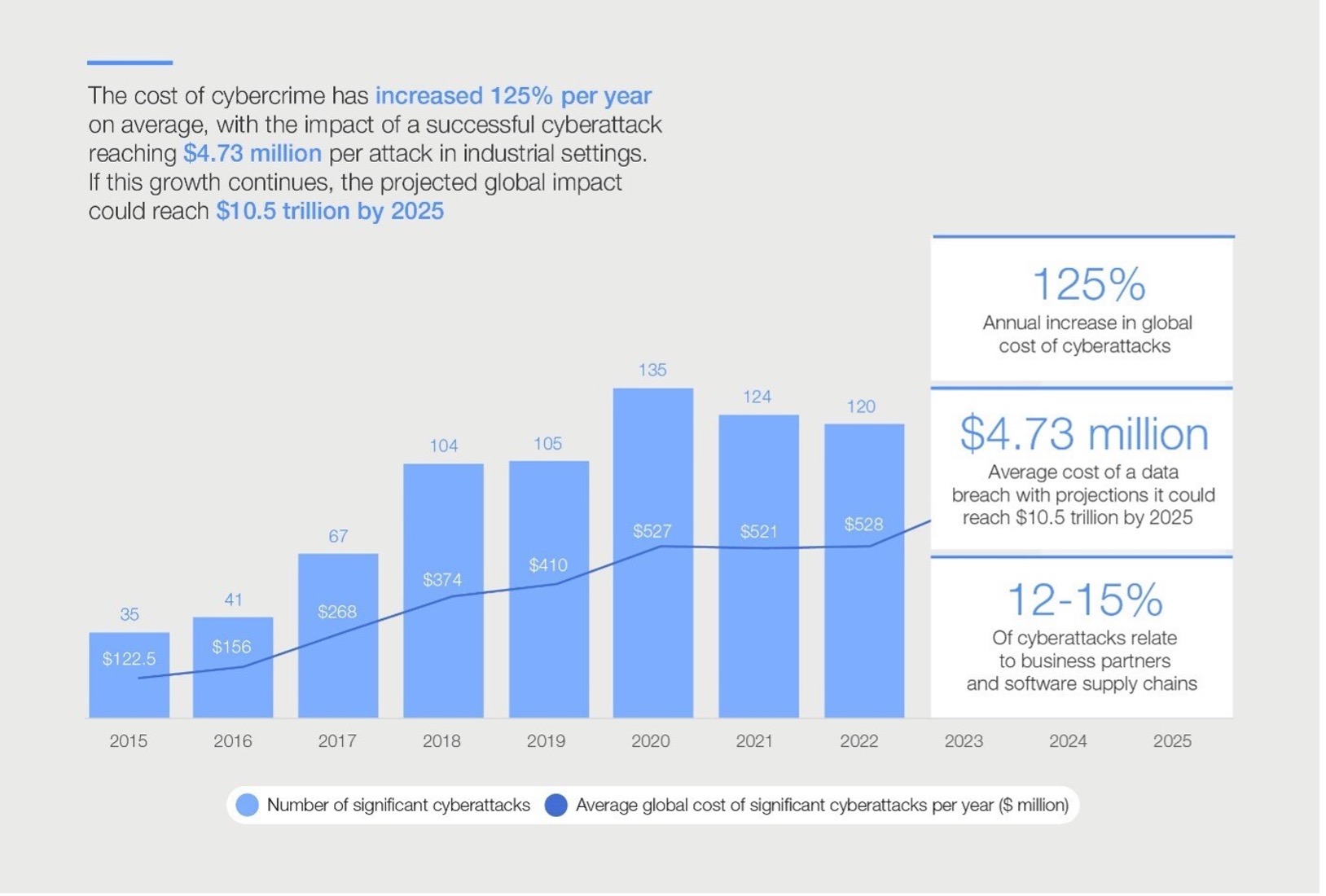
[Source: World Economic Forum]
It’s time to confront these challenges head-on and take charge of your future with cybersecurity.
#1: ICS Vulnerabilities: Moving Beyond Design Flaws
Industrial Control Systems (ICS) are the backbone of manufacturing, yet many remain outdated and vulnerable. Legacy devices and shadow IoT expose operations to serious risks.
- ICS systems are often outdated, running on legacy software lacking modern security features
- Attacks on ICS can lead to production stoppages, damaged equipment and physical safety hazards
Is Manufacturing Still Relying on Security by Obscurity?
Advanced manufacturing is moving away from legacy systems, but insecure by-design equipment is still hanging around. On top of that, many vulnerable IoT devices pose the same risk as old, unpatched logic controllers. We explored this topic in our recent study, “What are the Riskiest Connected Devices Right Now?”:
“Some of these devices are likely hiding in your infrastructure, beyond the visibility of your IT department, providing fertile ground for cybercriminals looking for entry points.”
Manufacturing is also characterized by proprietary protocols and automation systems — which present a double-edged sword. Their obscurity, largely unknown to most, can make them harder to compromise, but when breaches do occur, the consequences can be devastating. These attacks are generally difficult to detect and nearly impossible to stop without disrupting production.
Go deeper: Watch this webinar with our research leaders.
“The Emergence of Exposed ICS: Trends, Threats and Best Practices”
Close the Gaps and Target Critical Vulnerabilities
Most OT security solutions today can detect vulnerabilities though the accuracy may vary between vendors. Did you know that even by combining three of the most comprehensive vulnerability databases, you only cover 80% of what could be exposing your business?
This is exactly what our Vedere Labs uncovered in their latest research: “Exposing the Exploited”. Beyond coverage, what truly differentiates vulnerability management is how effectively those vulnerabilities are managed and prioritized. It’s not just about finding gaps, it’s about addressing the right ones, quickly.
Avoid the common pitfalls of fragmented solutions that require integrating multiple tools for full visibility. The ability to minimize blind spots and streamline the slow, complex vulnerability management process in manufacturing is critical to reduce risk and ensure operational efficiency.
#2: Securing the Supply Chain: Managing the Weakest Link
A single weak link in your supply chain can expose your entire operation to third-party risks. Trust may be your first line of defence, but a well-structured strategy is what truly secures your system.
- Manufacturing often involves a complex supply chain with numerous suppliers and partners
- A breach in any part of the supply chain can compromise the security of the entire organization
Do You Still Want to Do Business with Those Who Can’t Be Trusted?
Supply chain vulnerabilities have become a ticking time bomb for manufacturers. We’ve seen it in major supply chain attacks where a single overlooked weakness in a supplier has sent ripples throughout the industry, resulting in significant financial and reputational damage.
The goal of your strategy should not only be to prevent incidents, but also to ensure resilient operations in the face of disruption.
Effective planning is crucial for cyber event recovery. Your organization must have robust procedures in place not only to select and monitor partners and vendor but also for system backups, safe updates and rollback plans to ensure the rapid restoration of critical industrial systems or assets affected by supply chain attacks.
Building Industrial Resilience in Modern Manufacturing: 6 Actionable Steps
| Gain an integrated IT/IoT/ICS view of your manufacturing environment, ensuring access to actionable insights. | Fortify your supply chain by partnering with trusted vendors and enforcing strict security policies and controls. | Leverage compliance standards to build a cybersecurity strategy tailored to your organization specific needs. |
| Empower your workforce by automating routine tasks and simplifying core processes to address everyday operational and security issues. | Embrace for Impact by securing entry points, segmenting networks, and staying informed about the latest ransomware trends and attack methods. | Bridge the expertise gap by giving your team the right tools and strategies to mitigate cybersecurity risks effectively. |
Trust Is Good, Zero Trust Is Better
Do not trust anyone blindly, establish strict policies and security controls to monitor your risk exposure and only work with partners who can demonstrate their commitment to cyber security best practices. You must be able to detect and address security policy issues while managing asset lifecycle events such as configurations, changes, risks, and compliance, across your entire manufacturing environment. This is critical for monitoring supply chain risks and ensuring your operations remain secure and efficient.
#3: Knowing How to Use Compliance to Build a Resilient Cybersecurity in Manufacturing Strategy
Complying with legal regulations while securing your operations requires a customized approach tailored to your company’s individual needs.
- Manufacturing organizations manage essential services and handle sensitive customer data, intellectual property and operational information.
- Compliance with regulations, such as NIST, IEC, GDPR and CCPA, is crucial, but adapting them to specific contexts can be complex and challenging.
One Size Doesn’t Fit All: Tailoring Compliance to Your Unique Context
Regulations and compliance frameworks serve as essential tools for establishing guidelines and identifying gaps, but they are often presented as one-size-fits-all solutions. The real challenge for manufacturers is adapting these guidelines to their specific needs to consider factors, including company size, industry and operational complexity.
While compliance can feel burdensome, it is, in fact, the foundation of a solid cybersecurity strategy.
Standards, such as the NIST Cybersecurity Framework, IEC 62443, and ISO 27001, offer crucial guidance to help manufacturers tackle evolving security risks by fostering stronger defenses, operational integrity and proactive strategies. These frameworks support the resilience of critical manufacturing environments and enable scalable implementation across various sectors.
We also must consider local and industry-specific regulations that have a direct impact on manufacturing security:
- NIS2 Directive: Updates EU critical infrastructure regulations, extending its coverage to manufacturing and other vital sectors.
- German RAMI 4.0 (Reference Architectural Model Industrie 4.0): Focuses on the crucial elements of Industrie 4.0, providing a clear model for integrating technology and security.
- Singapore’s Cybersecurity Act (CCoP 2.0): A key standard for Critical Information Infrastructure (CII) owners, focusing on robust security practices.
- Australia’s Security of Critical Infrastructure Act 2018 (SOCI Act 2018): Part of Australia’s broader strategy to protect essential services, including manufacturing.
#4: Dealing with a Lack of Expertise in Cybersecurity in Manufacturing
Many manufacturing companies face a shortage of specialized cybersecurity expertise, leaving them without the necessary resources to effectively execute their plans.
- The absence of in-house cybersecurity experts makes it difficult to protect critical systems effectively.
- These skills gap often results in delayed responses to threats and heightened risk across critical infrastructures.
Everyone Wants an MVP Cybersecurity Player on Their Team
Everyone dreams of having top-tier security experts on their team, but is that really what you need? While a highly skilled analyst is crucial for handling zero-day exploits and complex malware, most manufacturers face routine operational and security challenges: Unstable devices, misconfigurations, weak passwords, and poor network access control or segmentation. These aren’t rare issues, they’re part of the daily routine.
Yes, expertise is valuable, but what you need is to empower your team to handle these smaller, yet critical, issues with ease. Rather than relying solely on specialists, simplify or automate tasks like enforcing strong passwords, setting up access controls and implementing segmentation policies. Streamlining these processes helps eliminate time-consuming, error-prone manual tasks, freeing up your top players to focus on more complex threats.
From Data Overload to Actionability: Streamline Your Security Operation
The key isn’t just having experts—it’s about equipping them with the right tools to work smarter. Your security team needs the ability to share context seamlessly across solutions, use persona-based views to tailor tasks to each role — and implement workflow automation to streamline routine processes. This way, they can concentrate on addressing the most critical security challenges.
#5: Preventing the Ever-Growing Threat of Ransomware Attacks
Ransomware attacks are a serious and growing threat to manufacturing companies. They can easily bring operations to a standstill, damage equipment and cause significant financial losses.
- Ransomware evolves rapidly, constantly finding new access points and spreading uncontrollably once inside.
- With an increasing number of ransomware actors and scalable operations, the threat is more persistent than ever.
Why Is Ransomware Such a Problem?
Ransomware is a fascinating yet complex topic. You may spend some time analyzing what makes these attacks so effective, only to realize that it’s not just about the code itself, but other factors that make them a real threat:
- The number of ransomware actors is on the rise with new adversaries emerging on the scene and established groups expanding their operations into this domain.
- Ransomware operations are becoming increasingly scalable, allowing attackers to target more victims with minimal effort.
- The barriers to entry for ransomware are falling rapidly as technology becomes easier to access and use, enabling less-skilled criminals to execute large-scale campaigns.
Go deeper with “The Current State of Ransomware Risk”.
Governments are working to reduce the impact of ransomware by pushing for tighter security practices, especially in public sector agencies and critical infrastructure. Sounds promising, right? But for private companies and mid-sized manufacturers, the reality is often quite different. Limited resources, lack of incentives and a dearth of professional cybersecurity services make it hard to keep up.
Ransomware Attacks Main Entry Points (in random order)
|
If you don’t have a comprehensive strategy to block entry points, limit lateral movement through network segmentation and enforce strict access controls, it’s time to familiarize yourself with terms like RaaS (Ransomware-as-a-Service), IABs (Initial Access Broker) and Double Extortion (where attackers not only encrypt your data, but also threaten to release it if the ransom isn’t paid).
Sooner or later, you may find yourself in the awkward position of having to explain to your boss why production has come to a standstill due to a ransomware attack. It’s better to prepare for that conversation now.
Securing Manufacturing Against Today’s Cyber Threats
The cybersecurity challenges in manufacturing are complex, but not impossible to overcome. Success comes from being proactive, developing a solid strategy and consistently testing your readiness. Remember, it’s not just about detecting threats, it’s about building resilience into your operations.