The current state of OT/IOT security is being repainted with a new coat of risk. The shade of color? Cellular routers and the vulnerabilities within firmware.
In our new report with Finite State, our joint research explores the risks organizations face within the software supply chains of OT/IoT routers.
Hardware has firmware – operational software – within its memory components.
Router vulnerabilities are hard to eliminate because firmware images frequently depend on outdated components for compatibility. The danger? Threat actors who can target many devices – and router locations – with a single exploit. When connected, these routers can be remotely monitored and controlled.
A large hospital network may procure hundreds of these hardware assets connected between mobile, real-time monitoring and information sharing applications. A fleet management or logistics enterprise may have thousands of LTE 4G routers.
As Forescout Research Vedere Labs has discovered, the depth of the firmware vulnerability problem is real. Last year, we examined a single hardware vendor with 21 new software component vulnerabilities.

With this awareness, Vedere Labs has expanded its research with Finite State to answer these questions:
- How severe are these firmware vulnerabilities across router vendors?
- Can we help develop a method to help expose vulnerabilities?
Instead of adding to the noise of threats and attack surfaces, we decided to shift focus towards existing vulnerabilities that are known and matter today.
Today, we offer the results of the findings.
Included in this new research are:
- The number of vulnerabilities discovered
- The number of Critical and High CVSS scores
- The number of ‘n-day’ vulnerabilities
- The average component age of firmware vs. the maximum age of the component
- The number of security findings by vendor component
Firmware Vulnerabilities: Why Would Attackers Target Cellular Routers?
The scope of cellular router use is deep within critical infrastructure and in industrial operations environments. There are more use cases than you might realize. State-sponsored hacktivists or financially motivated attackers will leverage any opening they find to disrupt or extort after taking control.
These routers are essential to having reliable business operations. But when it comes to keeping these devices secure and up to date with the latest patches, things are amiss.
See how and why — with all the data.
Cellular routers are used widely in edge computing – especially in remote locations where internet performance needs to be robust. They provide internet access and network connectivity in scenarios where traditional wired connections may be impractical or unavailable. Some of these routers, such as LTE 4G routers, allow high-speed, high throughput data transfer with precision.
Picture a remote, rural electrical substation where an operator needs to test or fix equipment – and needs to report findings directly into a software system.
They can also be used in incredibly busy environments – like a hospital or a transportation hub – where dependencies on having and relaying information are time sensitive and being on-the-go is essential. They provide fast operational processing for the user at their location.
“The coverage and reliability afforded by cellular networks means that networked devices, industrial components, and appliances can send and receive data in volume for precision monitoring and control,” explains George Hardesty, founder and president of Data Alliance in a “LTE / 4G Routers Guide”.
Common cellular router use cases
Industrial and infrastructure-intense settings
- Utility and grid intelligence with IoT devices for renewable and non-renewable environments – and smart metering
- Generators
- Lighting including critical, ‘always on’ airport runways and cell towers
- Industrial refrigeration
- Irrigation systems
- Sewage systems
Fleet management
- Emergency police and fire departments
- School buses
- Vehicle telemetry
- Haulage and heavy goods vehicles
Physical security
- Alarm-based property monitoring
- Sensor data from doors and windows
Why SBOMs Are Critical to the Security of Routers
It’s time-consuming work to understand all the elements inside these routers and how they behave. Finding all the intricate components used in common models of a specific class of assets is difficult at scale. Hence, the need for a Software Bill of Materials (SBOM) and the work of Finite State.
Here is how we conducted this research:
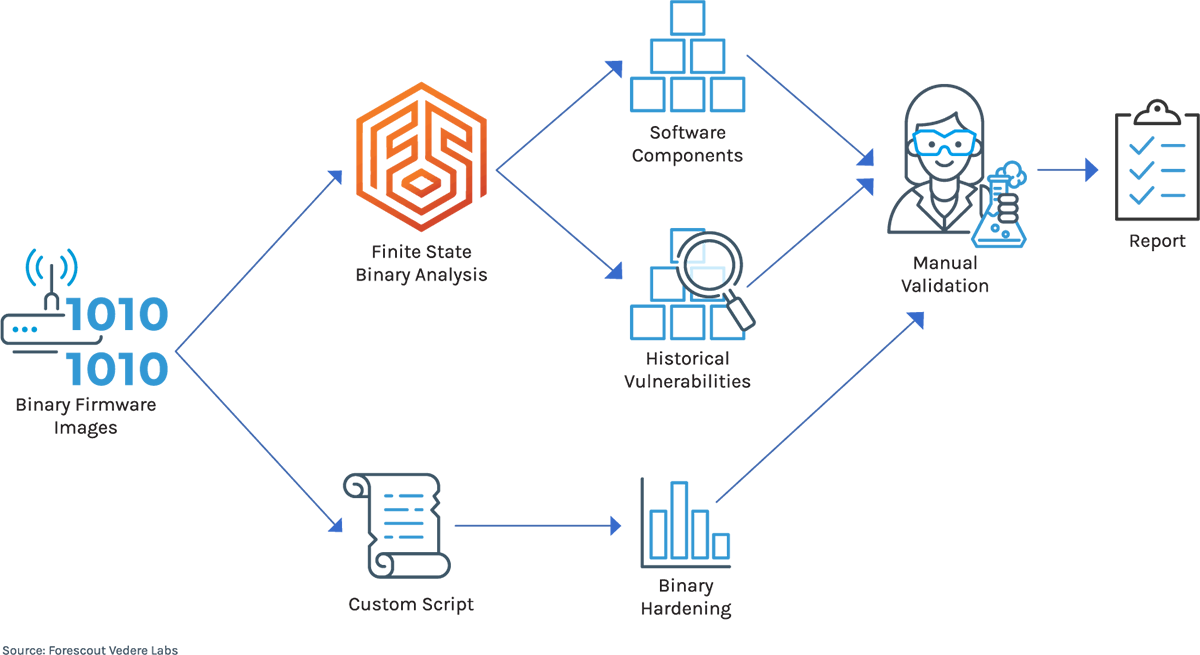
We applied this methodology to five popular OT/IoT router vendors: Acksys, Digi, MDEX, Teltonika, and Unitronics. These vendors all produce firmware that hosts the vulnerabilities.
What We Discovered When Researching Firmware Vulnerabilities
OpenWrt Is Everywhere
OpenWrt is a software that is used earlier on in the process of connecting critical devices to the network for remote control and monitoring. OpenWrt is used in the majority of router vendors, including four out of the five. However, this popular choice does not go without its faults. Our research found that the component CVE-2023-1389 in OpenWrt is frequently abused to deploy cyberattacks through a Mirai botnet variant.
Firmware Software Is Outdated
Between the five vendors, Vedere Labs found an average of 662 components and 2154 findings per firmware image including vulnerabilities, weak security postures and potential new vulnerabilities.
- The average update is four years behind OpenWrt’s latest release
- The average open-source component is over five years behind
- All firmware images, except for Digi’s, rely on an unsupported version of OpenSSL
Custom Patches Are Incorrect or Insufficient
Vedere Labs found that vendors applying their own patches to known vulnerabilities sometimes introduced new issues or were incorrect patches altogether. Additionally, companies rarely produce public records or security advisories mentioning these patches, leading to additional vulnerabilities under the guise of newfound security.
The full report includes a vulnerability ranking that summarizes Forescout’s research by placing each company’s firmware on a scale of low-medium-high-critical.
Webinar: Learn more with Daniel dos Santos, VP of Research, Vedere Labs and Larry Pesce, Product Security Research and Analysis Director, Finite State.
How to Help Resolve Router Firmware Insecurity
This is a call to action. Router vendors and device manufacturers need to improve the information they provide to customers. This solution starts with SBOMs. Customers need support regarding device risk, detection and threat responses – and they need to be able to patch insecure firmware quickly.
Risk mitigation in OT/IoT requires a network-based, granular and dynamic asset inventory.
SBOMs can be generated and provided by the device manufacturers or reconstructed from a firmware image, as we did with Finite State. However, most manufacturers still decline to provide SBOMs.
The process for fortifying the routers in OT/IoT is laborious. To help better secure these firmware vulnerabilities, router manufacturers should provide detailed SBOMs to customers. SBOMs would give customers a platform of better information to better support vulnerability management.
Major governing bodies, including CISA, published important guidance on SBOMs last November. Be sure to read: “Securing the Software of Supply Chain: Recommended Practices for Software Bill of Materials Consumption.”
As discussed in our recent Riskiest Connected Devices report, asset risk should include information about the configuration, behavior and function of a device. It’s not enough to know that a vulnerability exists. It is important to understand whether those vulnerabilities can be exploited based on the device’s configuration and behavior is essential for assessing and mitigating risk.
Thank you to Finite State for your excellent help and your accurate and detailed SBOM data. We are proud to have worked with you on this report.
Finite State is a leading vendor of Software Bill of Materials (SBOM). These SBOMs provide ingredient lists of the components in a software, allowing security teams and researchers to understand and analyze software components.