How to Detect and Mitigate the 3CXDesktopApp Supply Chain Attack
On March 29, researchers from two security companies identified an active campaign originating from a modified version of a legitimate, signed application: 3CXDesktopApp, a popular voice and video conferencing software.
3CXDesktopApp is developed by 3CX, a business communications software company. According to its website, 3CX has 600,000 client organizations and 12 million daily users. 3CX software supports several platforms, but only the Windows and macOS desktop clients have been confirmed to be compromised as of this writing.
The trojanized version of 3CXDesktopApp was observed as the first stage in a multi-step attack, which indicates that the threat is sophisticated. The threat actors behind the attack have also acquired a code signing certificate from 3CX that they have used to sign the malicious binaries. This further complicates the situation by making victims trust the malicious executable and by making it harder for security tools to detect the threat.
Based on the malicious code being used, the current campaign has been linked to North Korean APT Lazarus Group. Lazarus Group has been active since 2009 and was responsible for attacks such as the 2009 Sony breach and WannaCry. The group is also known as Labyrinth Chollima, Hidden Cobra, Guardians of Peace, ZINC and Nickel Academy.
Technical analysis
The trojanized version of 3CXDesktopApp is the first stage in a multi-stage attack depicted below, which contains also-malicious DLLs, ICO files downloaded from GitHub and a C2 server.
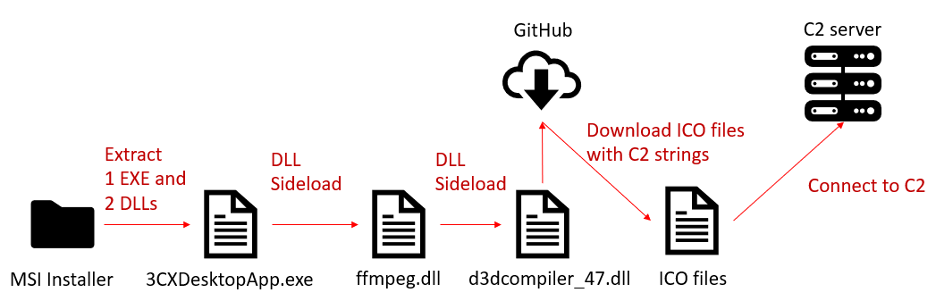
Forescout Vedere Labs analyzed an MSI installer obtained directly from the vendor’s website that includes both the malicious DLLs and the 3CXDesktopApp executable. The initial attack is a DLL sideloading with multiple components involved. The 3CXDesktopApp package contains the following files of interest:
- exe – 3CXDesktopApp application, which serves as a shellcode loader
- dll – A malicious loader DLL used to load and execute malicious shellcode from d3dcompiler_47.dll
- dll – A DLL with an appended payload
As in a regular update, the MSI installer launches the executable Update.exe, which in turn launches 3CXDesktopApp.exe. 3CXDesktopApp.exe loads ffmpeg.dll and then hollows out a portion of the 3CXDeskttopApp.exe binary to inject code from d3dcompiler_47.dll.
After the contents of d3dcompiler_47.dll have been read into the heap space, the code decrypts the malicious shellcode appended in the file, using RC4 and the key 3jB(2bsG#@c7 – as shown below.
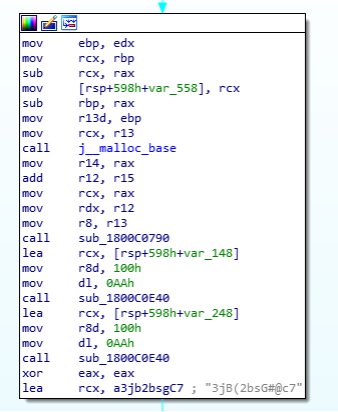
After the shellcode is decrypted, the newly allocated memory section is given a PAGE_EXECUTE_READWRITE permission using the VirtualProtect API. This allows for the memory section to be executed.
The malicious shellcode then accesses a GitHub repository that houses ICO files containing encrypted strings. These strings are C2 domains that the shellcode accesses to download other possible payloads. We were unable to confirm the exact nature of these payloads since the GitHub repository had already been taken down at the time of writing.
Mitigation and how Forescout can help
Although the 3CX software is widespread and important to an organization’s communication system, the campaign has only been seen targeting newer versions of the desktop app. There are reports that many customers still rely on older versions (“3CX Phone for Windows”) and those are unaffected.
3CX advises users to uninstall the desktop application and use the Progressive Web App client instead, while the company works on an update.
Forescout Threat Detection & Response can detect the installation of the trojanized software by closely monitoring both EDR and network security logs. The following two rules have been added to Forescout Threat Detection & Response to provide holistic detection of this evolving threat:
- CY-IR-1818 Emerging Threats: Potential Compromised 3CX Desktop Application Beaconing Activity – DNS
- CY-IR-1819 Emerging Threats: Potential Compromised Installation Of 3CX Desktop Application Detected
Forescout TDR’s out-of-the-box IOC detection rule can also alert on IOCs associated with the ongoing campaign. The screenshots below show this detection for the file with SHA256 hash 92005051ae314d61074ed94a52e76b1c3e21e7f0e8c1d1fdd497a006ce45fa61 (the macOS version of the trojanized 3CXDesktopApp installer) and how the IOC is presented in Forescout TDR’s Threat Intelligence view.
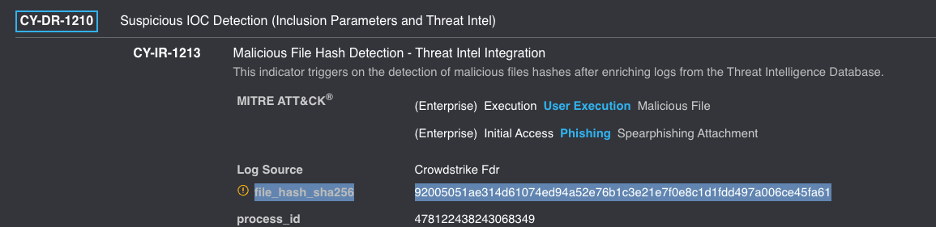
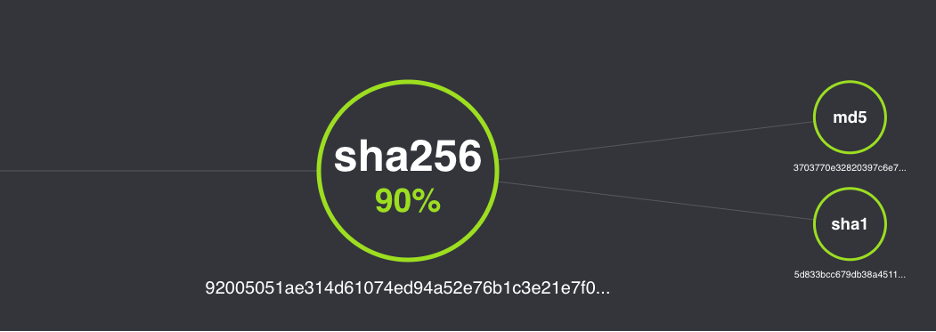
IOCs associated with 3CXDesktopApp intrusion campaign
SHA 256:
- dde03348075512796241389dfea5560c20a3d2a2eac95c894e7bbed5e85a0acc – Windows executable
- aa124a4b4df12b34e74ee7f6c683b2ebec4ce9a8edcf9be345823b4fdcf5d868 – Windows executable
- fad482ded2e25ce9e1dd3d3ecc3227af714bdfbbde04347dbc1b21d6a3670405 – Windows executable
- 59e1edf4d82fae4978e97512b0331b7eb21dd4b838b850ba46794d9c7a2c098 – Windows executable
- 92005051ae314d61074ed94a52e76b1c3e21e7f0e8c1d1fdd497a006ce45fa61 – macOS executable
- 5407cda7d3a75e7b1e030b1f33337a56f293578ffa8b3ae19c671051ed314290 – macOS executable
- b86c695822013483fa4e2dfdf712c5ee777d7b99cbad8c2fa2274b133481eadb – macOS executable
- e6bbc33815b9f20b0cf832d7401dd893fbc467c800728b5891336706da0dbcec – macOS executable
- c485674ee63ec8d4e8fde9800788175a8b02d3f9416d0e763360fff7f8eb4e02 – ffmpeg.dll
- 7986bbaee8940da11ce089383521ab420c443ab7b15ed42aed91fd31ce833896 – ffmpeg.dll
- 11be1803e2e307b647a8a7e02d128335c448ff741bf06bf52b332e0bbf423b03 – d3dcompiler_47.dll
- 4e08e4ffc699e0a1de4a5225a0b4920933fbb9cf123cde33e1674fde6d61444f – icon13.ico
Domains:
- akamaicontainer[.]com
- akamaitechcloudservices[.]com
- azuredeploystore[.]com
- azureonlinecloud[.]com
- azureonlinestorage[.]com
- dunamistrd[.]com
- glcloudservice[.]com
- journalide[.]org
- msedgepackageinfo[.]com
- msstorageazure[.]com
- msstorageboxes[.]com
- officeaddons[.]com
- officestoragebox[.]com
- pbxcloudeservices[.]com
- pbxphonenetwork[.]com
- pbxsources[.]com
- qwepoi123098[.]com
- sbmsa[.]wiki
- sourceslabs[.]com
- visualstudiofactory[.]com
- zacharryblogs[.]com