Next-Generation NAC: Balance Security and Usability in Complex Environments
Network Access Control (NAC) has undergone significant advancements since the beginning, continuously adapting for cybersecurity threats and technological innovation. As organizations embrace BYOD (Bring Your Own Device) and IoT/OT (Internet of Things/Operational Technology), vendors have transformed traditional NAC solutions to meet these new demands while maintaining a balance between usability and security.
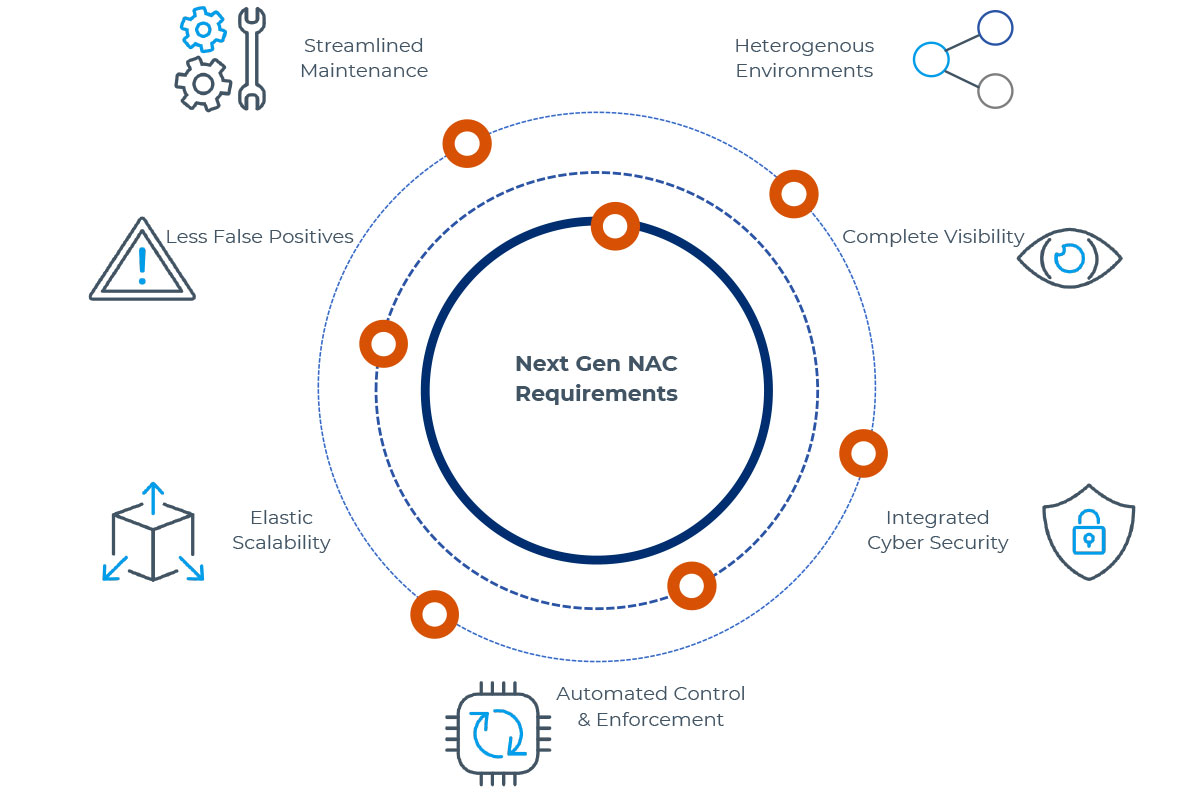
Modernized NAC has also seen a shift towards agentless solutions. These solutions offer flexible and non-disruptive network security that can be utilized without requiring software installations on individual devices. This approach significantly reduces the complexity of deployment and maintenance, making next-gen NAC more usable to a wider range of use cases.
Building the Next-Gen NAC
NAC began with authentication and authorization mechanisms. Early releases focused on device compliance and verifying user credentials before granting network access. Next generation NAC capabilities, such as those included in Forescout for Network Security solutions, have expanded far beyond that original scope. Forescout solutions offer comprehensive asset discovery and classification capabilities, giving enterprises total control over managed and unmanaged network assets. This progress has led to the development of more sophisticated features, including:
- Complete asset visibility and inventory
- Granular network access control
- Automated access policy enforcement
- Intelligent segmentation
These advancements have elevated NAC from a trusted and reliable toolset into a centralized cybersecurity system that delivers improved network security and usability. Network engineers and security teams can enforce access controls based on multiple risk factors and enable coordinated security monitoring and response, all of which provide a foundation for Zero Trust.
Network Security and Zero Trust
Zero Trust is dependent on complete visibility into every connected device. Forescout’s continuous discovery identifies and maintains accurate asset inventories, enabling classification and assessment that organizations can use to verify the identity and integrity of everything attempting network access. Then, apply the most granular, least-privilege access controls and security policies. This helps enforce Zero Trust principles by ensuring only authenticated, compliant assets access the network. And Forescout’s adaptive approach to Zero Trust gives your stakeholders and decision makers the foothold they need to implement Zero Trust from any starting point — with resources and budget that makes sense for your business.
Next-Gen NAC Is Network Security
By taking advantage of the synergies between NAC, Zero Trust and network security, organizations can implement a holistic, compliant, data-centric framework that reduces attack surfaces and aligns with cybersecurity best practices for even the most regulated businesses.
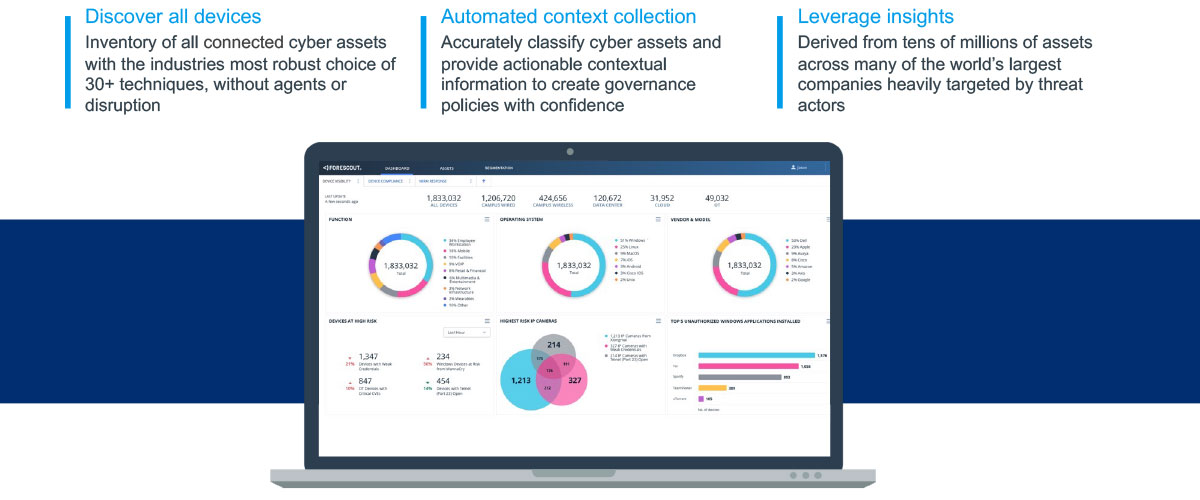
Delivering Comprehensive Device Visibility
Use Forescout for Network Security asset discovery and inventory to obtain and maintain complete asset visibility using active and passive discovery techniques for all managed and unmanaged IP-connected assets and IoT/OT devices. Continuous discovery maintains accurate inventory and enables classification and assessment of everything attempting to access the network.
Over twelve million device fingerprints in the Forescout Device Cloud give you high-fidelity, three-dimensional device classification capabilities to determine device function, OS, vendor and model, and more. That means you get complete coverage across all locations, networks and device types – without blind spots – with or without 802.1X authentication.
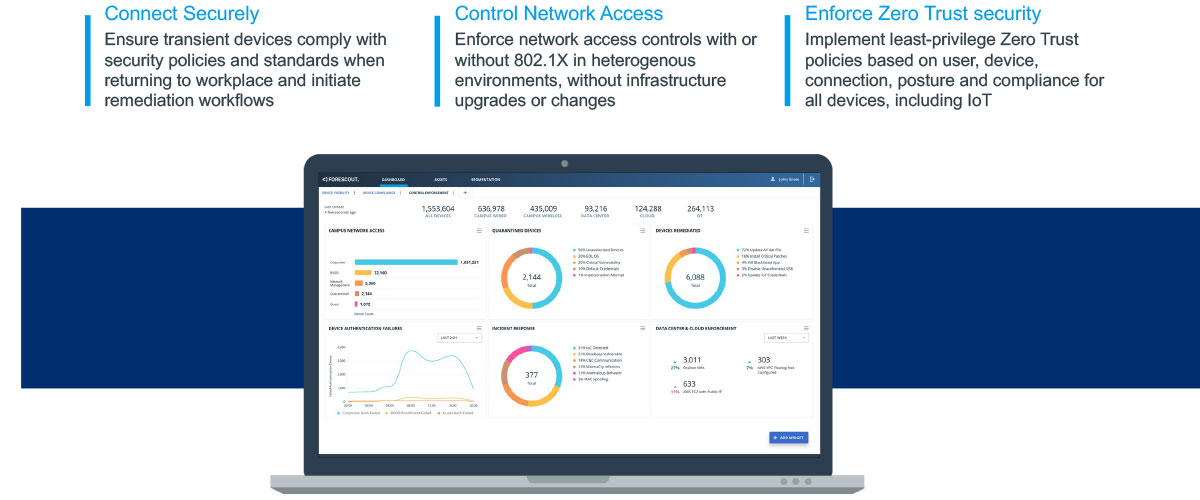
Providing Granular Access Control
Ensure the least privileged access by only granting access to network resources that match approved context or character of past access and usage; for example, Forescout for Network Security dynamically assigns devices to the appropriate VLANs or applies access control lists based on pre-defined policies. Agentless controls then enforce those access policies without requiring software installations on any devices.
Automating Policy-based Enforcement
Continuously monitoring, verifying, and validating all connected devices helps dynamically adapt access privileges and automates threat responses based on behavior, posture, or compliance deviations. If an asset falls out of compliance, the solution will automatically enforce the correct security policies.
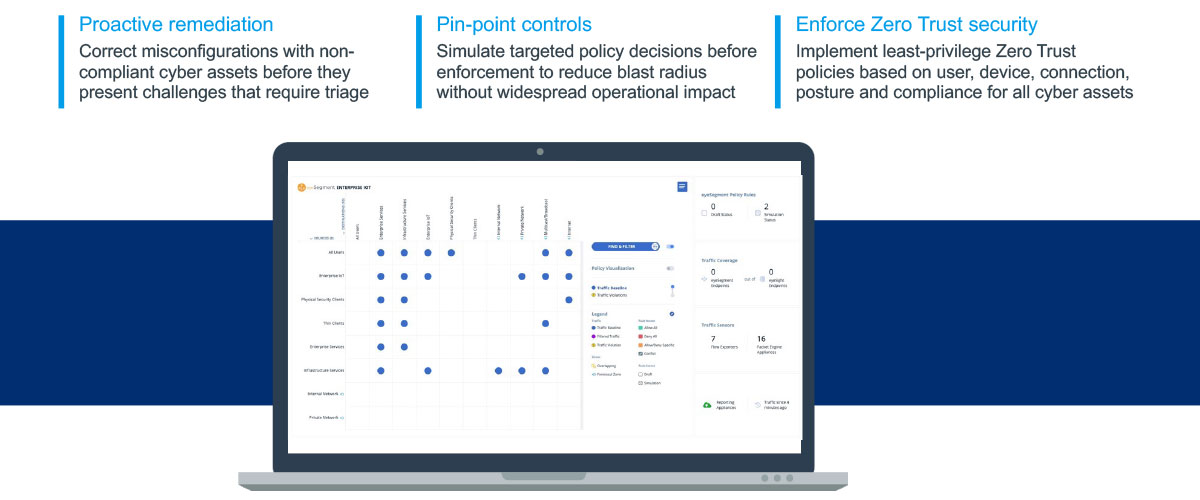
Providing Intelligent Segmentation
The Network Security solution’s segmentation function improves access control by managing who can access different parts of the network and when. Enforce the principle of least privilege with network segmentation to enhance the overall security of the network. You can use this capability to analyze network traffic from a dynamic zone perspective and gain an understanding of dependencies that inform planning, deployment, and automated policy enforcement. You can also use network segmentation to restrict traffic flows between assets, reducing the potential blast radius of threats.
Innovate Across the Technology Stack with a Unified Security Solution Powered by Forescout
The hybrid network needs comprehensive visibility and control over all network assets to ensure effective cybersecurity monitoring, threat detection, and incident response. It is also part of an evolving ecosystem that ingrates with IT tools, ticketing and SIEM, to deliver coordinated threat responses and automated remediation actions.
By leveraging ecosystems that enable content sharing, automated workflow orchestration, and comprehensive host and network-level response measures, Forescout for Network Security works seamlessly with existing infrastructure investments. This integration extends to popular platforms, such as Microsoft Azure, ServiceNow, CrowdStrike, Palo Alto, and many others.
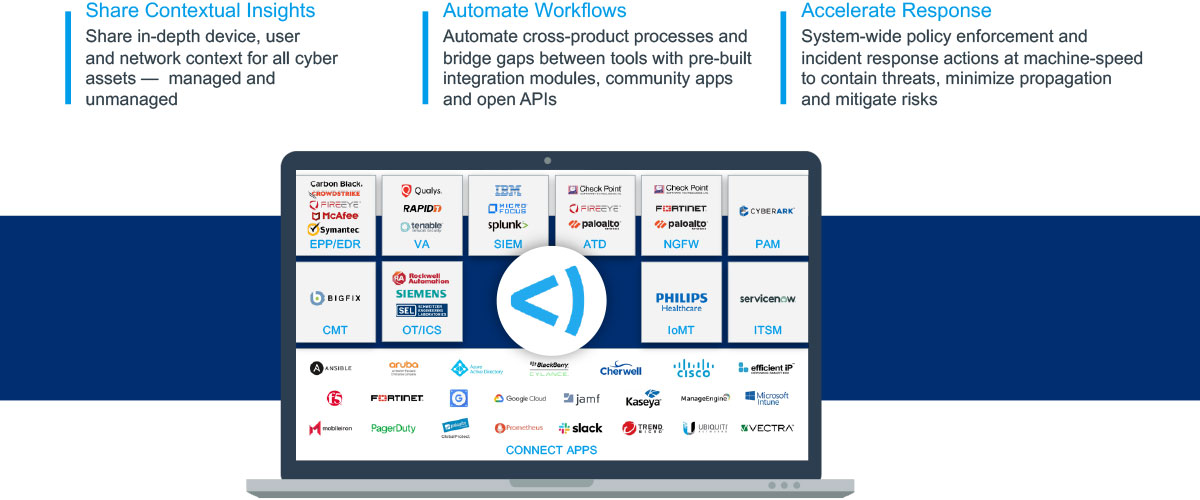
Next-generation NAC is part of a holistic, compliant, data-centric framework that reduces attack surfaces and aligns with cybersecurity best practices. By taking advantage of the synergies between NAC, network security, and zero trust principles, network engineers and security teams can apply comprehensive security strategies that are both effective and user-friendly. As threats continue to evolve, network security solutions will continue to adapt, providing tools that protect networks while maintaining operational efficiencies and usability.
Learn more about Forescout’s Network Access Control solution.