See how OT compliance frameworks and the right solution could have helped improve resiliency in three real industrial cybersecurity attacks
Here are three examples that are worth your attention. Oh, what could have been avoided.
Attack #1: Ransomware at a Pharmaceutical Company in India
What Happened: In March 2023, an Indian pharmaceutical company fell victim to a ransomware attack by a notorious cyber-criminal group who infiltrated and encrypted critical data and systems. The company’s refusal to pay the ransom resulted in halted production, delays in the distribution of medicines, and substantial financial losses.
How: Initial access came via a phishing email, then exploited unpatched vulnerabilities to move laterally within the network. The company’s lack of strict security policies and segmentation allowed the attackers to encrypt critical data and operational systems and maintain control remotely, paralyzing production and distribution.
Why the NIST CSF Is So Important to OT Compliance
NIST CSF 2.0 provides an important template helping organizations of all sizes systematically understand, manage and mitigate cybersecurity risks to ensure comprehensive. By taking a structured approach, companies can ensure that no critical aspect of security is overlooked. Here’s how the NIST Cybersecurity Framework 2.0 can help:
Risk Assessment (ID.RA): This section guides the CISO through the identification and prioritization of risks by leveraging cyber threat intelligence, early signs of campaigns, group activities, and exploitability metrics.
Detect (DE): This section focuses on continuous monitoring and Indicators of Compromise (IoCs) to detect potentially adverse events. The company failed to detect the incident multiple times and missed signs from initial access to lateral movement, highlighting the need for enhanced monitoring.
Protect (PR): This section addresses end-user training and emphasizes that an effective awareness campaign could have prevented the phishing attack. Comprehensive training ensures that employees have the knowledge to recognize phishing emails and minimize cybersecurity risks.
How the Right Solution Could Have Helped
In today’s ever-changing threat landscape, you need to be able to adapt and update quickly to new threats. With a solid solution, you can ensure that threats and risks are prioritized and remediated immediately to close gaps before they can be exploited.
Actionable threat intelligence: Top-tier OT data feeds from a research organization, such as Vedere Labs, can helo you contextualize risks, prioritize remediation efforts and stay on top of attacker trends and campaigns.
Contextualized incident analysis: Improve decision making and accelerate incident investigation with clear classification, detailed descriptions and MITRE ICS mapping for alerts.
Efficient incident response: Accelerate your threat response and reduce fatigue by consolidating alerts from multiple detection sources into a comprehensive view of the incident, ensuring fast and effective remediation.
Go deeper: Get our NIST CSF 2.0 eBook.
Plus learn all about the latest NIST guidance: New NIST Zero Trust Guidance Reinforces Agent Hygiene Value
Attack #2: Ransomware at German Steel Manufacturing Plant
What happened: In December 2022, a leading European steel manufacturer fell victim to a large-scale cyberattack that targeted its production facilities in two factories, severely disrupting production processes. To contain the threat, the company had to shut down parts of its IT infrastructure, resulting in several days of business disruption and six weeks of thorough investigation and threat hunting to ensure the threat was fully eradicated.
How: The adversaries exploited two moderately classified, well-known vulnerabilities in the company’s network to gain initial access, escalate privileges, and deploy ransomware. The IT security team detected the intrusion early, but due to the lack of segmentation between the IT and OT networks, critical industrial systems had to be taken offline to prevent further damage.
CISO Takeaway
Despite the company’s previous encounters with cyber incidents, the security teams failed to recognize the early signals, detecting the attack only after adversaries had escalated privileges and maintained persistent access to systems.
- Weak Access Control (RBAC): The lack of robust role-based access control allowed attackers to escalate privileges too easily, underscoring the need for stronger access management policies to limit unauthorized actions.
- Ineffective Vulnerability Management: Because known vulnerabilities were not immediately identified and prioritized, the network was susceptible to attack, pointing to the need for stricter and proactive vulnerability management.
- Lack of Network Segmentation: Insufficient segmentation between IT and OT networks allowed attackers to move laterally and compromise both administrative and industrial systems. This gap required a more comprehensive shutdown to contain the threat and protect critical infrastructure.
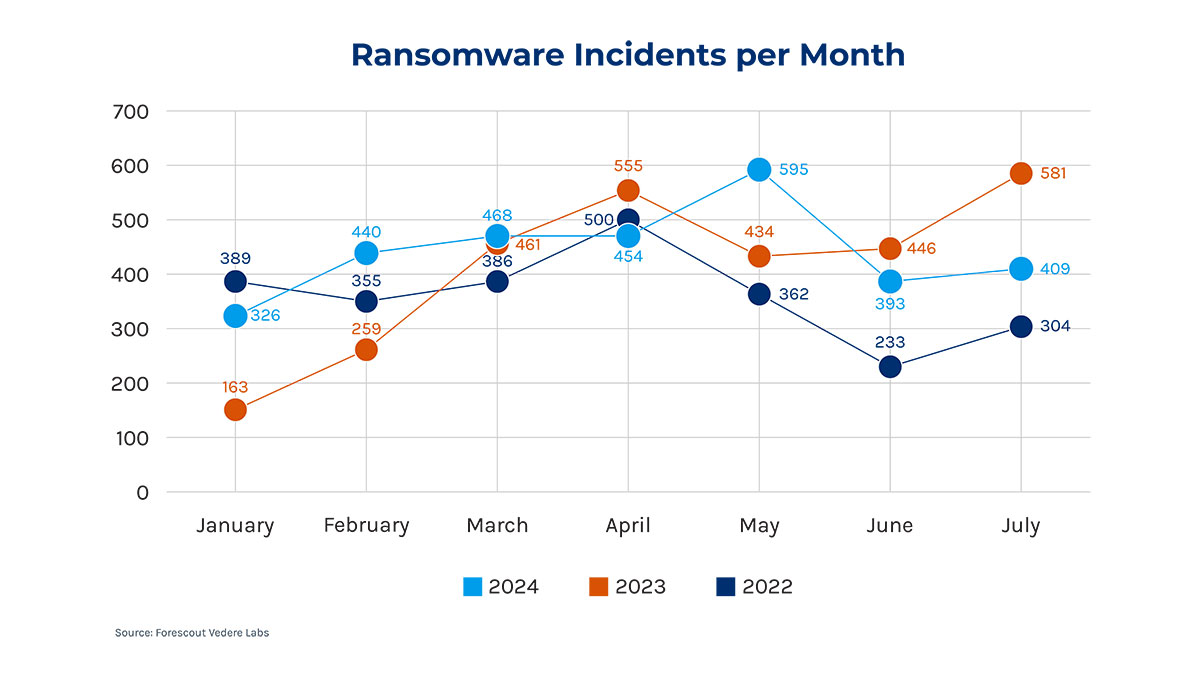
Today, ransomware averages 441 attacks per month or 15 per day, according to Forescout research.
OT Compliance: IEC 62443 Is Powerful Architecture
Manufacturers can protect critical infrastructure by adopting key cybersecurity frameworks and standards, including NIST CSF, IEC 62443, ISO 27001, or NIS2 in Europe. These guidelines, driven by legal and industry requirements, are essential for safeguarding sensitive information and ensuring uninterrupted operations. Let’s see what could have been addressed using the IEC 62443 series as a reference.
Detailed risk assessment: Conducting risk assessments as described in IEC 62443-3-2 could have highlighted high-risk areas, vulnerabilities and threat vectors, enabling a proactive approach to identifying risks within the system.
Access and use control: The implementation of IEC 62443-3-3 standards for identification, authentication and access control supports segregation of duties and least privilege to ensure that only authenticated and authorized users, processes and devices can access the system, protecting against unauthorized actions.
Zones and Conduits: IEC 62443 proposes an industrial control system architecture that utilizes the Purdue reference model and divides functional levels into zones and conduits. This segmentation is a result of the security risk assessment specified in IEC 62443-3-2 and increases security by restricting data flow and minimizing attack paths.
Go deeper: Get our ebook on IEC 62443.
How the Right Solution Could Have Helped
This company did recognize and contain the threat, but only after damage had been done. They failed to prioritize and respond quickly enough. With a proactive strategy, the attack could have been thwarted early. Effective security relies on timely execution, not just planning. They needed:
Risk exposure management: Gain a unified view of risk, vulnerabilities and compliance to improve business continuity and resilience by gaining real-time visibility into the attack surface. This allows you to identify and prioritize vulnerabilities more effectively.
Essential compliance and reporting: Detect non-compliant assets, review policies, streamline audits and simplify compliance with AI-powered reporting and real-time compliance analytics. Continuous compliance can prevent attacks that exploit poor security hygiene.
State-of-the-art network security: Create a solid foundation for a zero-trust environment with flexible access policies and dynamic segmentation that effectively minimize attack surfaces and close security gaps. This would prevent lateral movement within the network and protect both IT and OT systems.
With automated remediation, this steel manufacturer could have implemented security measures exactly when needed and without any delay.
Attack #3: Water Treatment Plant: Human Error or External Actors?
What happened: In February 2021, a water treatment plant in Florida appeared to show unauthorized individuals gained access to the plant’s control systems. The attackers attempted to change the chemical composition of the water and increase the sodium hydroxide content to dangerous concentrations.
How: Allegedly the attackers exploited inadequately secured remote access software. They used this software to gain access to the system and attempted to increase the concentration of lye in the water. The attack was discovered when an operator noticed the change in real time and reversed it to prevent damage. To this day, it is unclear whether remote access software was really the original access point, as other theories point to an inside job or a mistake by an employee.
CISO Takeaway
While some details of the incident are still unclear, the investigation has revealed critical weaknesses that reflect sector-wide problems affecting many water utilities. The glaring lack of effective monitoring and vulnerability management systems underscores the urgent need for improved security measures, especially in smaller organizations.
- Inadequate monitoring: There was no continuous network monitoring or anomaly detection systems in place, relying instead on human observation.
- Poor vulnerability management: The lack of visibility led to undetected vulnerabilities and potential entry points for attackers.
- No incident response plan: Incident response plan was disorganized, resulting in delayed identification and response to unauthorized access.
OT Compliance Specific to Water Treatment
This attack was part of a series of similar incidents, including drinking water system hacks in the Bay Area and Baltimore, as well as wastewater facility cyberattacks in Maine and California.
In response, the White House has stepped up efforts to increase cybersecurity in the nation’s drinking water and wastewater systems. The Department of Homeland Security’s Cybersecurity and Infrastructure Security Agency (CISA) provides measures to mitigate risk and improve defences against cyberattacks. In addition, the Environmental Protection Agency (EPA) offers guidance, tools, training, resources and technical assistance to help water systems implement the recommended protective measures including:
Minimize internet exposure: Restrict public-facing access to critical systems to prevent unauthorized intrusions. CISA advises limiting internet exposure as a fundamental step in securing critical infrastructure.
Conduct comprehensive cybersecurity evaluations: Perform thorough assessments to identify risks and remediate vulnerabilities. EPA recommends regular evaluations to maintain a robust cybersecurity posture.
Enhance vulnerability management: Implement robust patch management and regular vulnerability scans to minimize potential exploits. Both CISA and EPA stress the importance of timely updates and patches to protect against known vulnerabilities.
How the Right Solution Could Have Helped
This incident is a prime example of a mid-sized utility struggling with the typical challenges of the sector: limited budget, unqualified staff, and an ever-evolving threat landscape. Here’s how a complete solution could have made a difference with a few simple, cost-effective steps:
Device visibility: Complete visibility across your entire infrastructure, from legacy OT systems to IT and IoT devices. Knowing what you need to protect is a key point in any security framework.
Risk and posture management: Identifying vulnerabilities is table stakes. A good solution helps prioritize risks and remediation efforts by highlighting the most vulnerable devices exposed to the internet or external services.
Threat and anomaly detection: Threats are not only found in cyberspace; operational issues can also be disruptive. The right solution detects undesirable behaviors and process values that deviate from the baseline, ensuring comprehensive security and operational integrity.
OT Compliance Is a Key Part of the Answer
In high-stakes industrial cybersecurity, having a solid plan is only the beginning—you need the power to execute it without hesitation. Compliance frameworks and strategic vendor partnerships are the backbone of effective cybersecurity management. Leveraging standards such as NERC, NIST CSF 2.0 and IEC 62443 with robust solution support ensures that your organization can achieve business resilience and compliance.