For security professionals and CISOs, reading about operational technology (OT) security risk feels like nothing new. We know a lot of OT is insecure by design.
Despite advisory warnings and perceptions around operational security air gaps, industrial control systems (ICS) and Supervisory Control and Data Acquisition (SCADA) are being targeted more frequently via digital assets on the network. Vulnerabilities in OT systems are not brand new. Yet, the intensity of attacks and the ‘prepositioning’ within operational technology is expanding.
Key OT security data and recent events:
- More observable attacks: Critical infrastructure experiences 13 attacks every second
- Bigger, real world attacks: Denmark and the Ukraine
- More digital connections, more problems: IoT vulnerabilities expand 136% year over year
- Hard to track assets and components: Banned Chinese devices in the US increase +40% year over year
- More oversight, compliance and standards for OT and critical infrastructure: NIST, ISA 99/IEC 62443, NERC CIP, NIS2, and more
- More frameworks, approaches and architectures: Secure By Design, MITRE EMB3D, Zero Trust
- More individual scrutiny of CISOs: Solar Winds CISO charged, Uber CISO charged
At the same time, attacking OT is getting easier for adversaries. Threat actors have ransomware and other services at their fingertips. Attack kits are easy to deploy as vulnerabilities in IT, IoT and within OT itself have exploitable entry points. Managing OT security risk on shoestring budgets and a shortage of OT security skills isn’t helping. Frankly, it’s hard for your security operations’ teams to keep up.
They aren’t alone: A 2024 US Government Accountability Office report finds CISA, “America’s Cyber Defense Agency,” is challenged to keep up with OT vulnerabilities and may need more individuals with OT-specific experience:
“CISA officials stated that its four federal employees and five contractor staff on the threat hunting and incident response service are not enough staff to respond to significant attacks impacting OT systems in multiple locations at the same time.”
The report also finds there has been plenty of positive collaboration and working arrangements between many different Federal agencies and CISA. Though one agency points out the process for making some vulnerabilities public can take over a year to be disclosed.
Our recent analysis on the official vulnerability process showed gaps in reporting can be dangerous. There are many exploited vulnerabilities not captured in CISA KEV. In addition, we showed that no single database includes every exploited vulnerability, so organizations should rely on multiple sources. What’s more, these vulnerabilities exist within OT security areas too.
‘VL-KEV’ is named for Vedere Labs KEV which is shared with CISA and other governing bodies.
Why OT Security Risk Requires Better Asset Intelligence in ICS, IoT and More
There are gaps across the OT security landscape – and it isn’t enough to rely on one source of vulnerability and threat information. And it’s not enough to use security products that cannot discover the full depth of threats on the network.
AES, a major turbine operator with 70 global plants across 15 countries, talked to us about the value of asset intelligence data. Asset intelligence informs its vulnerability management practice, gives visibility of all the systems that bridge to OT, helps detection and response, and influences segmentation.
“The foundation of any cybersecurity program is to know the assets,” says Kyle Oetken, Director of Cyber Defense at AES. “You’re kind of shooting in the dark without a tool to do this for you. OT devices typically lag behind the IT network as far as cybersecurity is concerned. Having well-defined network segmentation to isolate one from the other is incredibly important.”
Oetken and his colleague Andrew Plunket, a Sr. Cybersecurity Engineer for OT, also detailed the most important aspect for managing cybersecurity – bridging IT and OT with people working across security and functional operators.
“Many times, the operators will think that the number of systems and ways to bridge from IT to OT is much less than it actually is,” Oetken says. “So, it is essential to be ready to partner with plant operators because cybersecurity is new to them and, in most cases, not a high priority. Developing a partnership of collaboration is key.”
Read our entire interview with AES and its journey to securing OT.
Know Your OT Security Risk: By Device Category and Vertical
Forescout Research – Vedere Labs has been tracking OT/ICS risk for seven years. Since 2017, OT security risk has not declined very much at all. Executive Orders banning devices from specific countries may be strong declarations of intent, but they are proving to be harder to follow. Procurement processes and white labelling of hardware with banned componentry may be to blame.
Our 2024 research shows a year over year increase of 41% in the number of banned devices from China in US critical infrastructure and within government networks.
“All your base are belong to us” – A probe into Chinese-connected devices in US networks – Forescout
Vedere Labs has also been tracking OT vulnerabilities and risk across verticals. Our OT:ICEFALL research discovered a set of 61 vulnerabilities affecting devices from 13 operational technology (OT) vendors caused by insecure practices in OT. The affected products are prevalent in many industries, including oil and gas, chemical, nuclear, power generation and distribution, manufacturing, water treatment and distribution, mining, and building automation. Many of these products are sold as ‘secure by design’ or have been certified with OT security standards.
This is where asset intelligence begins: With deep threat intelligence from OT-centric research. Then, you need to know all of your assets – what it is, where it is and how it connects.
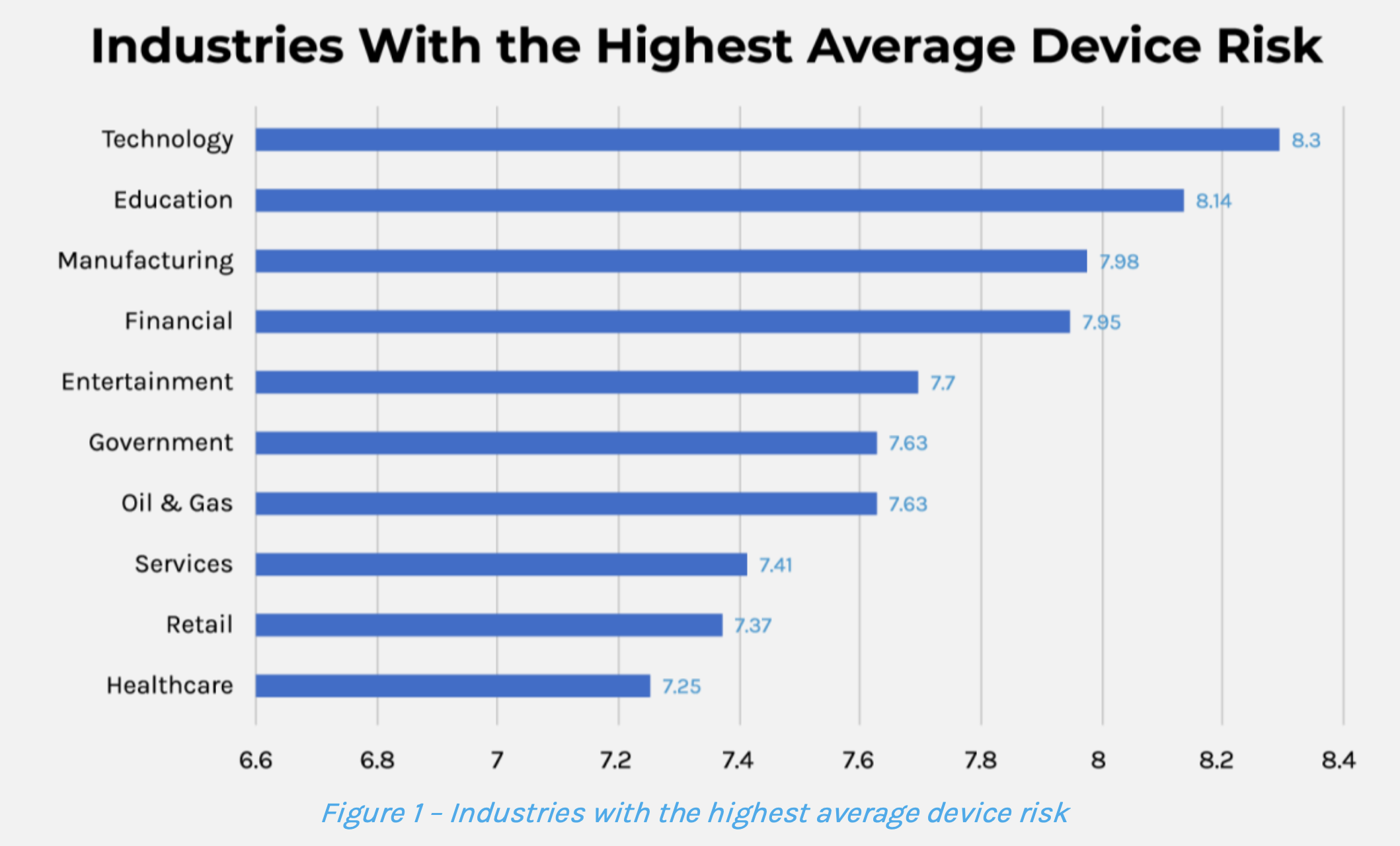
Our latest research, Riskiest Connected Devices in 2024, captures OT, IT, IoT and IOMT risk across 10 industry verticals from 19 million devices in our anonymized customer data lake. Here is a snapshot of the the risk in the report and a vertical breakdown of average risk by industry.
OT Devices
The riskiest OT devices include the critical and insecure-by-design PLCs and DCSs. It also includes the UPSs present in many data centers with default credentials — and the ubiquitous, often invisible building automation systems.
UPSs play a critical role in power monitoring and data center power management. CISA has alerted about threat actors targeting UPSs with default credentials. Attacks on these devices can have physical effects, such as switching off the power in a critical location or tampering with voltage to damage sensitive equipment.
PLCs and DCSs are risky because they are very critical, allowing for full control of industrial processes, and are known to be insecure by design, often allowing attackers to interact with them and even reconfigure them without the need for authentication.
Building management systems, also known as building automation systems, are critical for facilities management. There are several examples of smart buildings exploited by threat actors to render controllers unusable, recruit vulnerable physical access control devices for botnets, or leverage management workstations for initial access. These devices dangerously mix the insecure-by-design nature of OT with the internet connectivity of IoT and are often found exposed online even in critical locations.
Robotics: The use of robots is quickly increasing in industries, such as electronics and automotive manufacturing, where factories are becoming ‘smarter’ and more connected. There were close to 4 million industrial robots worldwide in 2023 with around 80% in just five countries: China, Japan, US, South Korea and Germany.
There are also service robots deployed in a variety of other industries, such as logistics and the military. Despite popular use, many robots have the same security issues as other OT equipment, including: outdated software, default credentials and lax security postures. Attacks on robots include production sabotage to physical damage of property and people.
Additional Research & Related Content
Threat Briefings and Reports
Original Cybersecurity Vulnerability Research
Visibility Helps Global Energy Company AES Assess Risk and Secure its OT Networks
Why OT Companies Should Follow NIS2: Safeguarding Critical Infrastructure in a Digitally Connected Era
New CIP Standards: Why Utilities Shouldn’t Wait to Deploy
Securing the Unseen: MITRE’s EMB3D Framework for Embedded Devices
Clearing the Fog of War: A Critical Analysis of Energy Attacks in Denmark and Ukraine