Ransomware in Healthcare: The NHS Example and What the Future Holds
On August 4, 2022, Advanced – a major software provider for the UK’s National Health System (NHS) and other healthcare customers – suffered a ransomware attack from a group that is still unknown to the public. The attack disrupted NHS services including ambulance dispatch, appointment bookings, patient referrals and emergency prescriptions. As of August 19, more than two weeks after the incident, most systems have only been partially recovered, and full recovery is expected to take up to four weeks in some cases.
This attack impacted the NHS via a service provider, similar to what happened when REvil leveraged Kaseya VSA to spread ransomware in 2021. However, this time the ransomware doesn’t appear to have spread outside of Advanced’s systems, at least in part because the software vendor disconnected some of their networks so customers could not connect to compromised servers.
In this blog post, we explore the impact of this ransomware incident on the NHS, show how future ransomware attacks may exploit exposed Internet of Things (IoT) devices on healthcare providers and discuss what healthcare organizations should do to avoid being the next victim.
The impact of ransomware on the NHS
This is not the first time that health services in the region have been severely impacted by ransomware. In May 2017, the WannaCry attack on the NHS, launched by North Korea, led to thousands of canceled appointments and a cost of nearly 100 million pounds. In May 2021, the Conti ransomware attack on Ireland’s health service led to weeks of disruption and a projected cost of $100 million.
The impact on the NHS of the current attack has not yet been calculated, but it can begin to be understood by analyzing the Advanced software systems that were attacked, their function and their current status, as shown in the table below.
| Software | Function | Status as of Aug. 19 |
|---|---|---|
| Adastra | Clinical patient management, which helps emergency call handlers dispatch ambulances and doctors access patient records | Forensic investigation advanced but 111 customers not reconnected |
| Caresys | Care home management | Forensic investigation ongoing but recovery not started (expected in 3 to 4 weeks) |
| Odyssey | Clinical decision support | Forensic investigation ongoing but recovery not started (expected in 3 to 4 weeks) |
| Carenotes | Electronic patient record software, used by mental health trusts for patient records | Customers had access to partial data, forensic investigation ongoing (expected for 3 to 4 weeks) |
| Crosscare | Clinical management for hospices and private practices | Forensic investigation ongoing but recovery not started (expected in 3 to 4 weeks) |
| Staffplan | Care management software | Customers had access to partial data, forensic investigation ongoing (expected for 3 to 4 weeks) |
| eFinancials | Public sector financial management | Systems back online and customers could reconnect |
One point stands out from the response to this incident: regardless of paying a ransom to recover data or not, healthcare systems cannot simply be brought back online after an attack. They need to go through a thorough forensic investigation to ensure there is no further compromise.
Advanced employed two external organizations to perform the forensic and recovery actions. For one service alone, eFinancials, those firms had to scan nearly 150 servers. In the healthcare sector, the time it takes to recover impacted systems typically leads to delayed or canceled patient care, as was the case for WannaCry in 2017 and Conti in 2021.
Although the response to this incident is still ongoing, it is safe to assume that there will be a very high financial impact for Advanced, and once again several NHS patients will have appointments and treatment delayed or canceled.
What the future holds for ransomware in healthcare
As the CIO of the UK’s health and social care system said in a review of the WannaCry attack in 2018: “It is not a question of ‘if’ but ‘when’ the next cyberattack strikes the health and social care system.”
In 2017, the impact happened because of computers running unpatched or legacy Windows operating systems at NHS trusts. In 2022, it was because of a managed service provider (MSP). MSPs are currently a great entry point for ransomware gangs because they may allow for access into many customer organizations at the same time. Even if the ransomware does not spread from the MSP to its customers, these customers are impacted by the MSP’s downtime.
In the future, Vedere Labs believes the impact will likely occur because of insecure IoT devices, since IoT as an entry point is gaining relevance with ransomware gangs. That belief is echoed by the UK’s National Cyber Security Centre (NCSC), which recently published a report that concludes there is a high likelihood that enterprise IoT will be used as an “attack vector or pivot point to enable cyber actors to gain access to an enterprise’s corporate network for espionage purposes, disruption, or financial gain.”
To show this threat vector in action, we recently developed R4IoT, a proof-of-concept ransomware that gains access to an organization via exposed IoT devices and moves laterally to exfiltrate and encrypt data on IT systems. This type of attack exploits an increased IoT attack surface and is applicable in almost every organization nowadays, but especially in healthcare.
A simple Shodan search for devices exposed to the internet in UK organizations with “NHS” in their name returned 1,585 results on August 22. We can also see an increasing trend of devices exposed online by NHS trusts in the past few years:
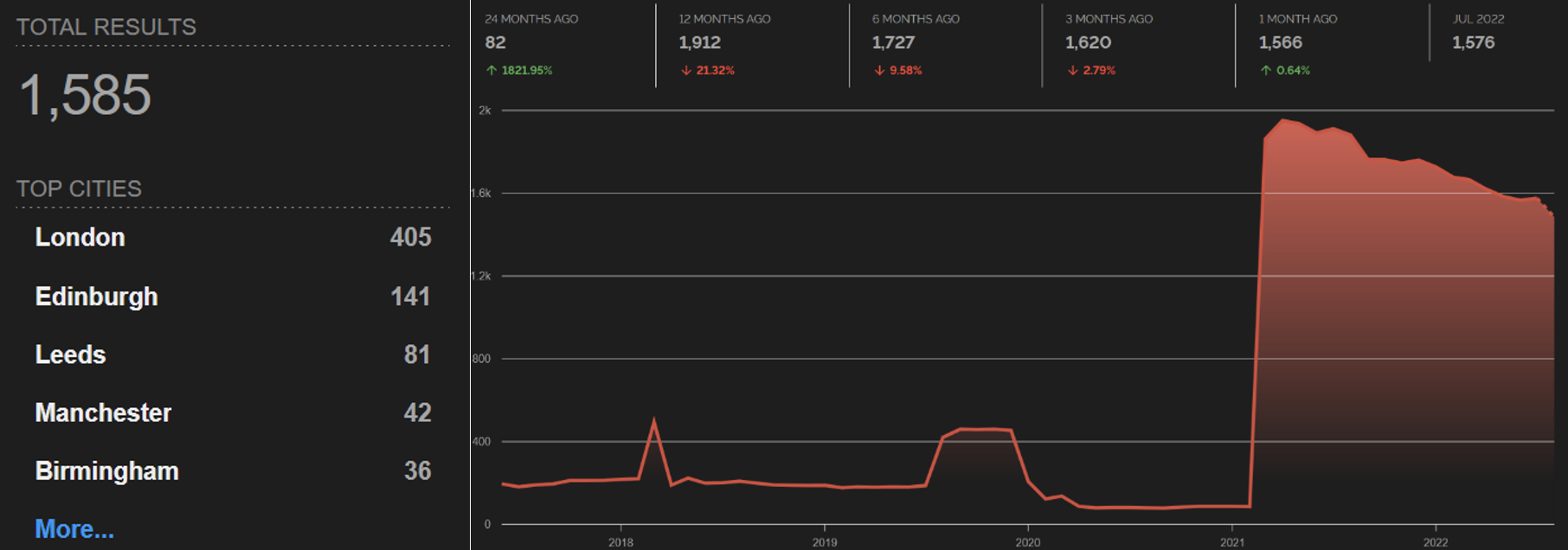
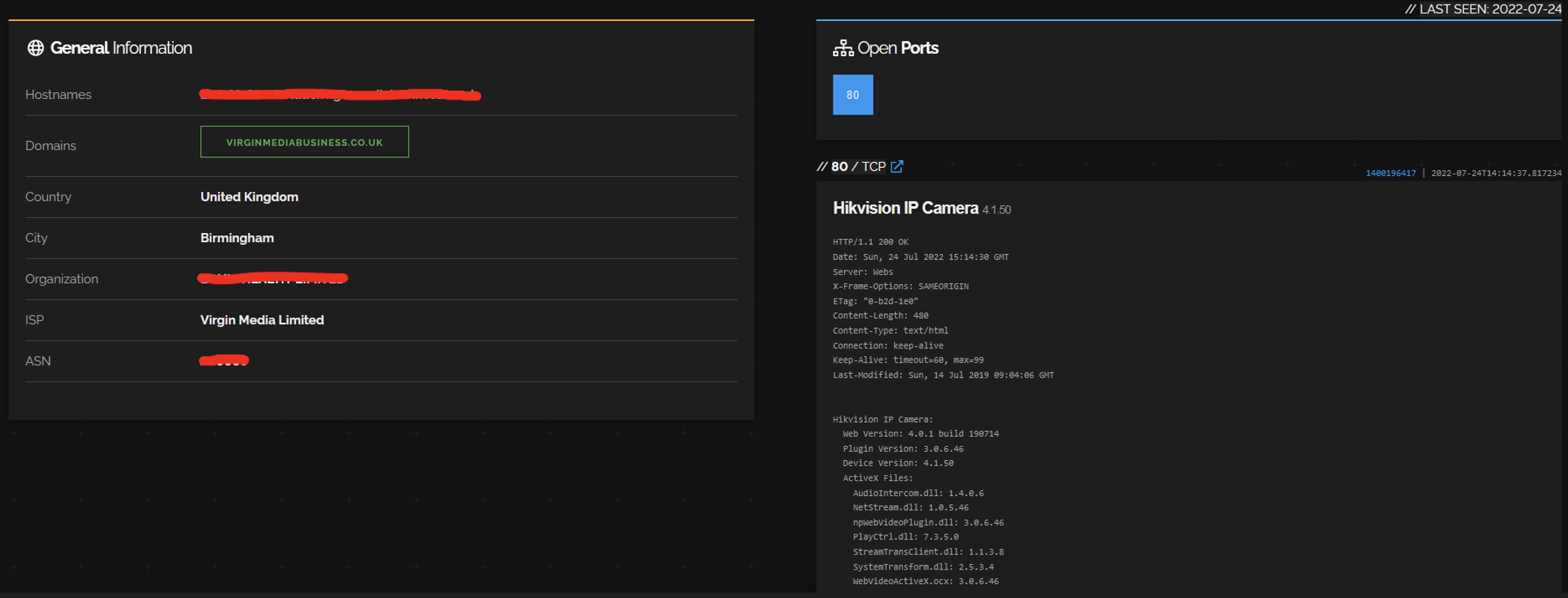
Most of these devices are still either web servers or network infrastructure, such as VPN concentrators, firewalls and routers. However, we see a lot of interesting IoT, such as eight VoIP phones, five Zyxel WiFi routers, five Crestron conference room systems, one Honeywell NVR, one Hikvision IP camera, seven devices with exposed Telnet and 28 devices with exposed embedded SSH and FTP servers. For instance, below is a screenshot showing the Hikvision camera, which may be vulnerable to remote code execution via CVE-2021-36260.
Defending healthcare networks from future attacks
In 2018, after WannaCry, the NHS’s review of the incident included this finding:
…most NHS trusts also need capital investment in areas such as addressing weaknesses in their infrastructure to secure networks by upgrading firewalls, improving network resilience and segmentation to minimise the risk to medical, improving device security through device replacement and automation of patch management, and improving anti-virus protection.
The themes of patching, segmenting and automating that were relevant in 2018 are even more important today with the increased attack surface brought by IoT.
The widespread use of IoT devices, the fact that they are often exposed online and the difficulty in patching them means that every organization, particularly in the healthcare sector, needs a proactive and holistic approach to cybersecurity that prioritizes:
- Discovering and inventorying every device on their digital terrain
- Continuously assessing the compliance and risk posture of these devices
- Automatically enforcing segmentation controls and proper network hygiene to mitigate the risk from vulnerable devices
Healthcare cybersecurity considerations checklist
The process for selecting a cybersecurity solution to protect your patients’ and your hospital’s critical infrastructure can be overwhelming. Download this checklist for IT security and clinical teams to ensure you don’t overlook the essentials.