Ransomware risk is top of mind for citizens and CISOs alike. From the board room to the room known as the ‘SOC’, everyone is feeling the pain of disruption. Being locked out of a system and forced back to pen and paper is shocking to our working lives. Too often, it is delaying a much-needed surgery or forcing manual intervention where a digital avenue was easy and efficient.
But the effects of ransomware don’t appear to be going anywhere soon.
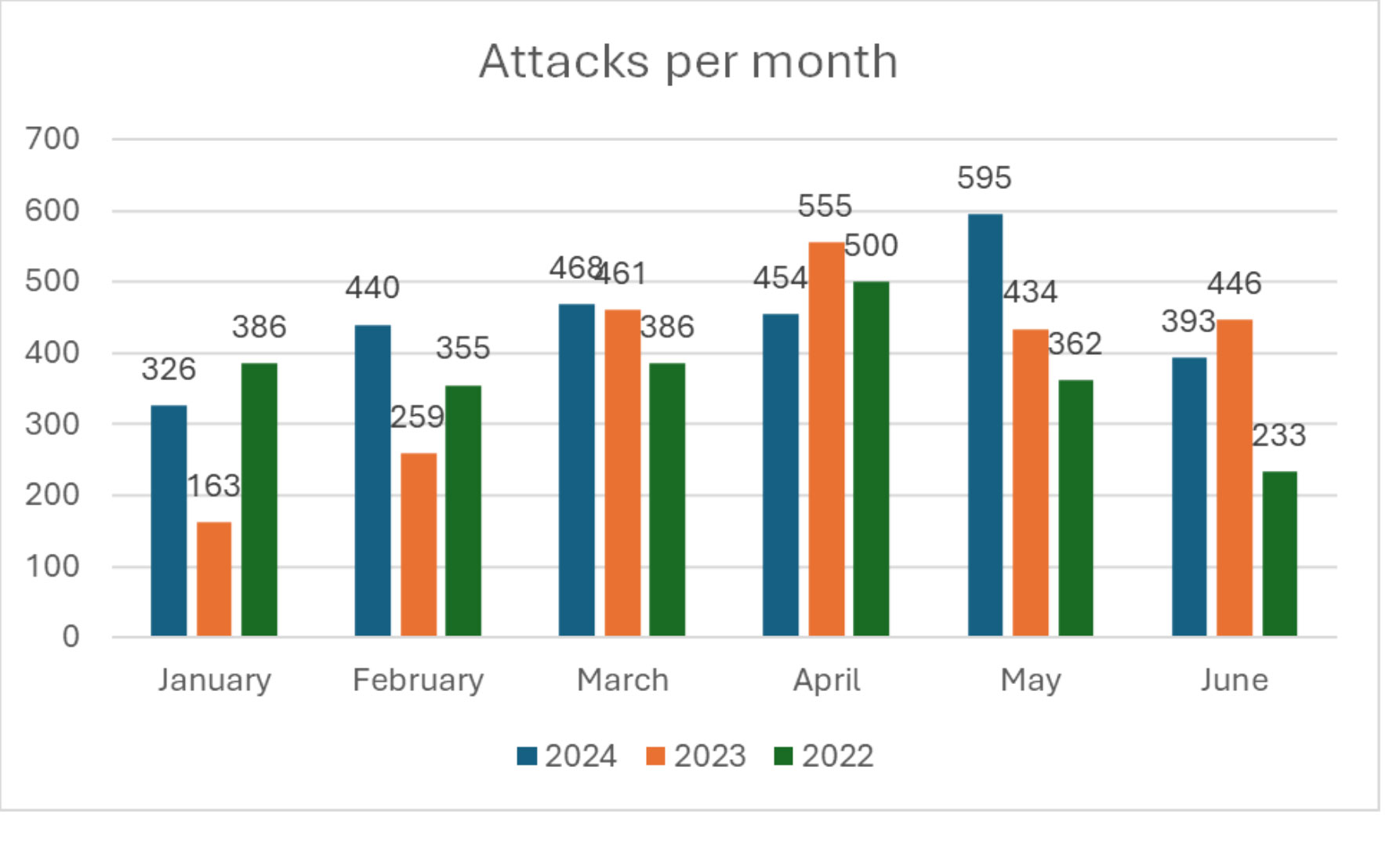
Digital extortion-based attacks are on a steady rise and its impact is being felt across every industry, including those in critical infrastructure. Forescout Research – Vedere Labs has observed 2,676 attacks through June of this year. The data is compiled via open-source tracking of ransomware leak sites. This is an increase of 15% from last year and is equal to 446 attacks per month or 15 per day.
Every day, it seems, there are new reports of extortionists being paid off by large enterprises or municipal government systems being shut down by attackers. Claims of the largest ransom ever paid – $75 million – have been published by researchers at Zscaler. This amount is nearly double the highest known payment of $40 million made by US insurer CNA in 2021.
CDK Global, a software company that serves the automotive dealership industry, recently paid $25 million in equivalent Bitcoin after a ransomware incident in June, according to Spiceworks. But not every organization will pay up.
The Florida Department of Health was hit by the ransomware group RansomHub recently with a threat of revealing 100 gigabytes of citizen information. The state has only confirmed the state’s online Vital Statistics system, used to issue birth and death certificates, was inaccessible. Though Florida has a standing policy of not paying digital extortion, data on over 10 million Floridians has been obtained by hackers in the last three years, per The Tampa Bay Times.
Cities and municipalities across the US are experiencing this rash of ransomware: Columbus, Ohio. The Los Angeles County Superior Court system. And smaller towns and cities, including Forest Park, Georgia, and Newcastle, Washington have all been recently attacked, according to Recorded Future News.
We follow it closely in our research – and have been for many years. In 2022, we published proof of concept research which explored the role of ransomware within IoT devices.
Ransomware Risk in 2024: The Spotlight Is on Healthcare
Some of the largest attacks using ransomware in 2024 have been in healthcare where medical device hardware and digital systems are intertwined. Between devices and software, healthcare is highly dependent on networked systems and the Internet of Things (IoT). In 2024, many large hospitals and healthcare networks – including Change Healthcare in February and Ascension in May – were attacked by ransomware.
“The tools that are available now can make amateur bad actors into pretty good, bad actors,” states Lee Schwamm, chief digital health officer at Yale New Haven Health System in an interview with MedCity News. “You can literally use LLM products and have them help you build ransomware code.”
Last year, we wrote about the topic in our blog “You’re Not Hallucinating: AI-Assisted Cyberattacks Are Coming to Healthcare, Too”. Here, we showed examples with technical detail about point-of-care testing and laboratory devices – and a proprietary protocol used in medication dispensing systems.
The recovery from the Change Healthcare attack is now being predicted to cost in the range of $2.4 billion – which is more than $1 billion more than previously expected by United Health Care – which owns Change, according to The HIPPA Journal.
What’s critical to understand is the sheer number of devices and technology vendors in healthcare. The volume of third-party risk is large and being managed as a ‘normalized’ part of operations.
“We have 4,800 different apps in our environment — with 1,700 attached to the EHR [Electronic Health Records],” relays Leah Miller, chief clinical application and data officer, at CommonSpirit Health, which is a large non-profit hospital chain in the US. “That’s 4,800 vendors that can fail every day, so that’s why we have two or three events every week.”
Go deeper. Learn how to master healthcare segmentation with the Director of Cybersecurity at ECU Health and experts from Forescout.
The real challenge occurs when attackers and criminals are able to find a vulnerability to gain control of data and systems. Sometimes, it is as easy as not having multifactor authentication turned on a server – which is what happened to Change Healthcare.
In other cases, an employee is phished or attackers use vulnerabilities in unpatched software or hardware devices as entry points into a network. Once inside, attackers move laterally to avoid detection and snoop around organizational data – and then lock it up and lock you out – until the ransom is paid.
“Hospitals are installing a lot of IoT devices — everything’s hooking into the network,” says Ashis Barad, chief digital and information officer, to MedCity News. “Every MRI machine is now connected to a network, but it wasn’t this way before.”
To better understand hardware risk, we compile an annual report dubbed “The Riskiest Devices”. This year, we discovered IoT devices had a 136% increase in vulnerabilities. For healthcare and medical fields, specifically, we detailed the five riskiest areas:
- Medical information systems
- Electrocardiographs
- DICOM workstations
- Picture Archiving and Communication Systems (PACS)
- Medication Dispensing Systems
A Closer Look at Ransomware Risk: The Criminal Groups and OT Risk
Overall, the ransomware landscape has continued to fragment and expand. We documented some of this fragmentation between ransomware groups in our post about the splinter between RansomHub from ALPH.
Last year, the top 10 groups accounted for three-quarters of attacks, they now only represent 60%. Concurrently, the number of active groups increased from 53 to 85, marking a 60% rise.
LockBit remains the most active group, despite a significant law enforcement operation in February this year. Other groups remaining in the top 10 are Play, BlackBasta, 8Base, Akira and BianLian. Among the new groups in the top 10, RansomHub has experienced rapid growth and was recently analyzed by our team.
While ransomware perpetrators are increasing and fragmenting, the list of countries where ransomware victims are located is decreasing and consolidating. Through June, the top 10 targeted countries suffered 80% of all attacks, up from 77% last year. The US accounted for half of all attacks, an increase from 48% from 2023.
Overall, there were ransomware victims in 100 countries, a 12% decrease from the 114 countries last year. All the countries that were in the top 10 last year remained on the list this year.
Cyber attacks involving OT and IoT are part of an alarming trend: Ransomware gangs, often operating a ransomware-as-a-service (RaaS) model, cripple the operations of several types of organizations, often at the same time. Attacks have moved from purely encrypting data (2019) to exfiltrating data before encryption (2020) to large extortion campaigns with several phases (2021). Sophisticated ransomware families (ALPHV, Conti) have been active, sometimes taking a political position after the Russian invasion of Ukraine. This evolution in attacker methods means that ransomware gangs can cripple the operations of virtually any organization.
Organizations need strong cybersecurity risk management practices to help realize effective cyber resilience.
See how healthcare company FDM efficiently transformed its cybersecurity.