Summary
The dataset of our IoMT devices research includes:
- 45 HDOs in our customer network
- Over 2 million IoMT, IoT, OT, and IT devices analyzed
- 300+ unique vendors
- 110+ unique OS versions
The DICOM medical imaging standard ranks high on risk:
- This popular service is one of the most exposed online
- Since 2017, DICOM exposure has grown by 286%
- Top exposed countries: US, India, Germany, Brazil, Iran, China
- The US far exceeds the rest of world’s exposure
Guidance
- Identify and classify every asset on the network
- Understand the software and operating systems they run
- Identify risks and vulnerabilities
- Limit external communications and exposure to prevent use as entry points
- Implement effective segmentation so breaches cannot reach medical devices and patient data
- Monitor all network traffic for signs of intrusion and respond timely
In 2024, healthcare delivery organizations (HDO) – hospitals, medical clinics, billing and payer systems – have received a lot of attention from ransomware attacks. The attack surface is rife with opportunities for criminal organizations to steal patient data or take control of parts of hospital networks.
Healthcare is highly dependent on networked systems and the Internet of Things (IoT) – and more specifically, the Internet of Medical Things (IoMT). Most attackers are after financial gain, but the possibility to take more life-threatening action and cause harm does exist.
When networks at HDOs are overtaken, the effects can be life-threatening. Life-saving surgeries can be delayed causing patient harm. Patient monitoring becomes a more manual experience of using pen and paper – slowing down care and eliminating the efficiencies and immediacy of shared data. Insurance approvals and billing systems often become unusable, so care can be stalled.
In the US, there were several major attacks including Change Healthcare in February that were so damaging they received government attention and required at least one CEO to publicly testify in front of Congress.
Learn more: Watch United Healthcare’s CEO speak with the US Committee on Energy and Commerce about the attack:
The recovery from the Change Healthcare attack is now predicted to cost in the range of $2.87 billion, according to The HIPPA Journal. This estimate comes from United Healthcare – which owns Change –and it has continued to rise with each corresponding quarterly report.
Our Riskiest Device Research Spotlights IoMT Devices
Our latest research “Unveiling the Persistent Risks of Connected Medical Devices” examines the full scope of today’s healthcare risk using a dataset from 45 HDOs in our customer network – and over 2 million assets.
Asset Breakdown
- ~50% of assets are traditional managed IT
- ~50% are IoMT, IoT, OT and unmanaged network devices
- 50% of IoMT are communication systems and healthcare workstations
- 25% are patient monitors and infusion pumps
- 25% are divided into 84 other functions
- Our sample isolated roughly 115,000 IoMT devices
- Works out to over 2,500 IoMT devices per HDO on average
That sample size of IoMT devices for a large HDO is not uncommon.
The sheer number of devices and technology vendors in healthcare is astounding. The volume of third-party risk is deep and wide. Today, it is being managed as a ‘normalized’ part of operations.
“We have 4,800 different apps in our environment — with 1,700 attached to the EHR [Electronic Health Records],” relays Leah Miller, chief clinical application and data officer, at CommonSpirit Health, a large non-profit hospital chain in the US. “That’s 4,800 vendors that can fail every day, so that’s why we have two or three events every week.”
Analyzing the Proliferation and Vendor Fragmentation of IoMT Devices
To understand what kind of IoMT devices are most often seen on these networks, we broke down this sample by device function and vendor. We observed 88 distinct IoMT device functions and 306 distinct medical device vendors. The top 10 functions are shown in the chart.
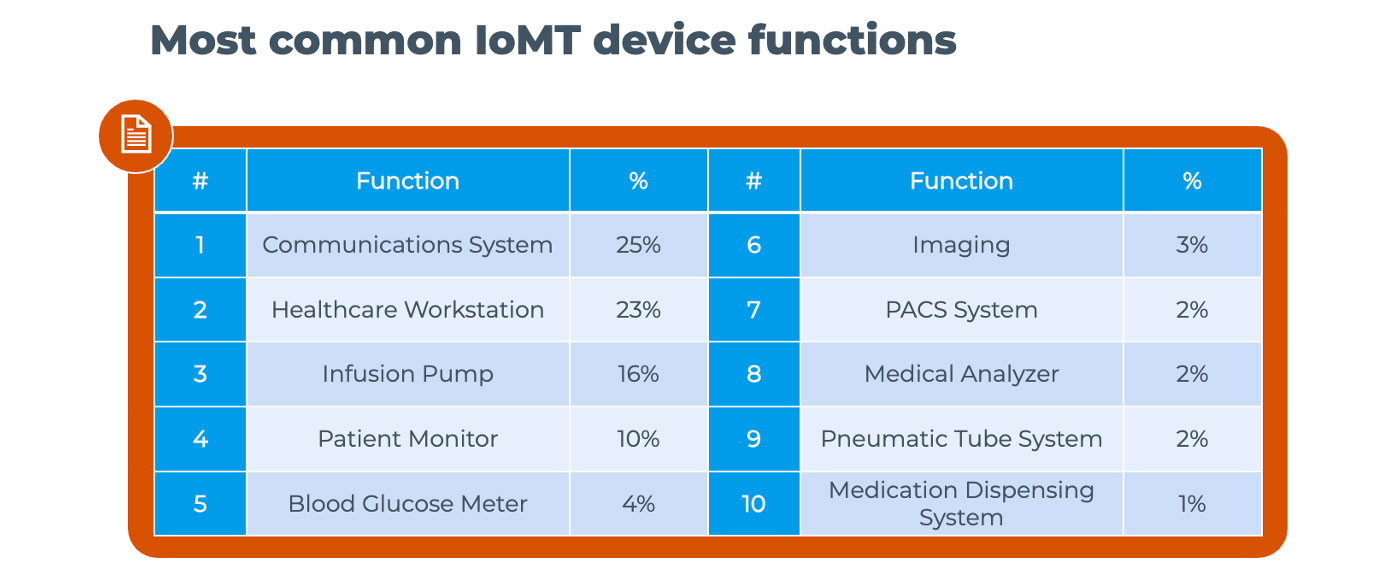
Two of the most popular device functions – communication systems and healthcare workstations – are not directly connected to patients, but they still provide critical healthcare functions, such as emergency alerts and communication. These technologies are also involved in the processing and storing of patient data. These functions together account for almost 50% of IoMT in healthcare organizations.
Patient monitors and infusion pumps – which are connected directly to patients – represent 25% of devices. The remaining 25% is divided into the 84 other functions identified, including a wide range of imaging systems, lab equipment and other specific equipment, such as pneumatic tube systems.
The vendor landscape is even more fragmented. Although well-known names, such as Philips, GE, Roche and Baxter are among the top 10 most popular, the ‘others’ category comprises an incredible 60% of vendors.
It’s an enormous amount of third-party risk to manage.
To understand the full context of today’s IoMT risks in healthcare, attend this webinar:
DICOM Is Widely Used with IoMT Devices and Widely Exposed
Our honeypot simulated a medical imaging device for over a year:
- Observed 1.6M interactions
- 1 attack occurred every 20 seconds on average
- ~23,000 interactions attempted a DICOM connection or search for patient data
Digital Imaging and Communications in Medicine (DICOM) defines both the format for storing medical images and the communication protocols used to exchange them. As a de facto standard, DICOM is implemented by all major vendors of IoMT devices involved in medical imaging processes, such as diagnostic workstations, storage servers and medical printers.
In the recent Riskiest Devices report, we showed that the IoMT devices most exposed to the internet are Picture Archiving and Communication Systems (PACS) running DICOM. We also published a dedicated study about internet exposure of medical devices in 2022 that reached the same conclusion.
Since 2017, there has been a growth of 246% in exposed DICOM servers. And in less than two years since we last examined DICOM exposure, it has expanded by 27.5%.
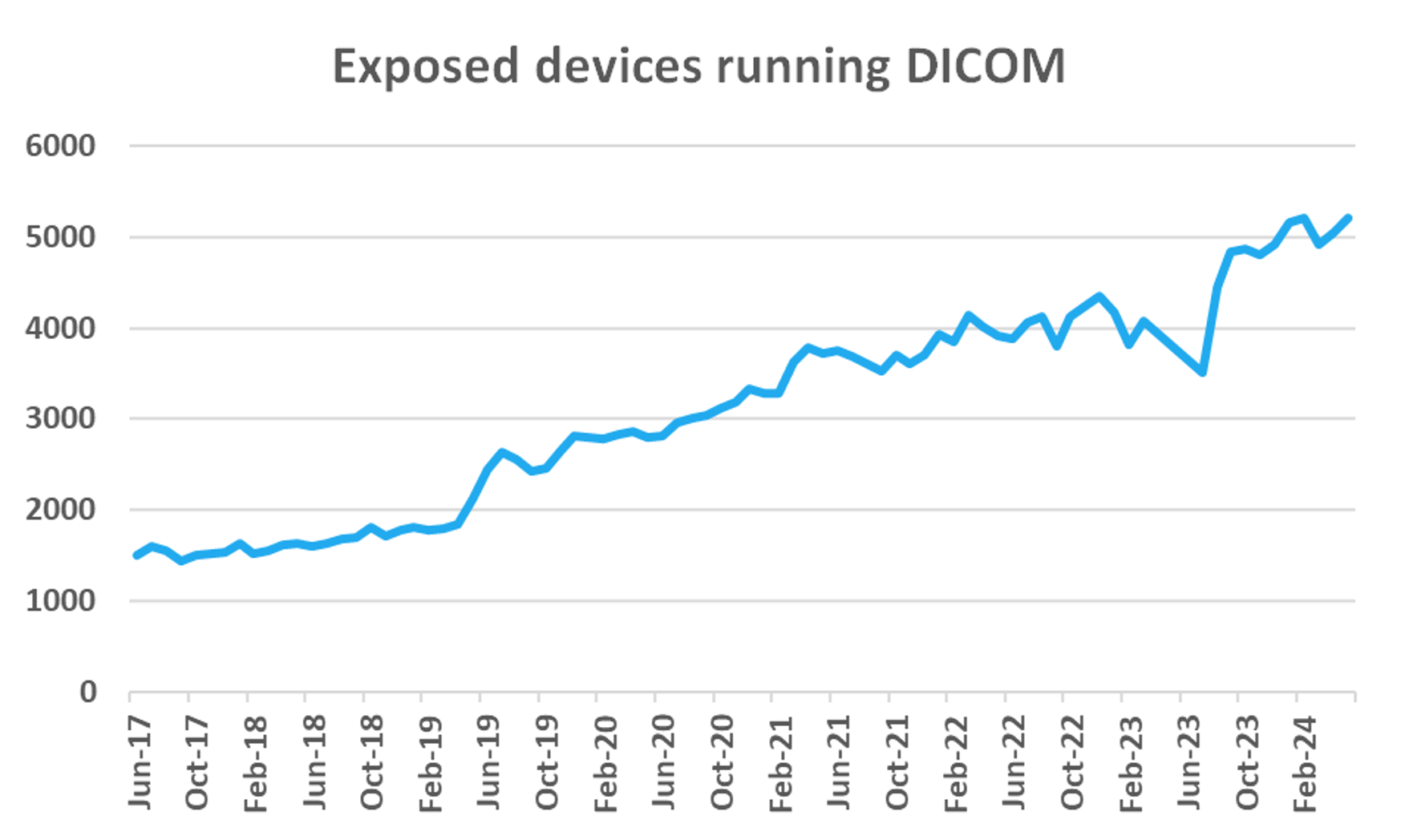
In August 2022, we reported 4,114 exposed DICOM servers with 825 of those being honeypot simulations, for a total of 3,289 real devices. In May 2024, we observe 5,207 servers with 1,013 honeypots, for a total of 4,194 real devices. This is almost twice the rate of growth (15.4%) we observed for medical systems in general – such as EMR, integration systems and others – during the same period.
For a complete breakdown of:
- The most common IoMT vulnerabilities, including legacy Microsoft Windows, Philips PageWriter, Baxter Sigma Spectrum, Siemens Biograph, etc.
- The most common open ports and internet exposure
- Attacks on DICOM – both observed and potential
- Analysis of the 6,215 data breaches reported by the US Department of Health and Human Services
- Complete mitigation guidance