The Rhysida ransomware as a service (RaaS) group was first revealed in May 2023. Since then, the group has claimed 41 victims, including some high-profile ones such as the Chilean army and five educational institutions in the U.S. The group is also suspected to be behind the attack against Prospect Medical Holdings, which affected 17 hospitals and 166 clinics in the U.S., although Prospect is not listed as a victim on Rhysida’s website.
On August 4, the U.S. Department of Health and Human Services (HHS) issued an alert classifying Rhysida as “a significant threat to the healthcare sector” due to their strong encryption, double extortion technique and multi-sector targets.
The alert also suggested that Rhysida shares significant similarities with the tactics, techniques and procedures (TTPs) of the Vice Society ransomware group. Given that Vice Society has not announced any new victim since late June – when Rhysida started becoming more active – it is possible that the latter is a rebrand of the former, something which happens frequently with ransomware groups.
Rhysida ransomware overview
Although there are variations such as different initial access methods, the use of PowerShell for defense evasion and techniques for data exfiltration (see the TTPs section for details) a typical Rhysida attack looks like this:
![]()
The threat actor leverages phishing for initial access, uses the well-known Cobalt Strike tool for lateral movement and delivers the Rhysida payload to encrypt files on victims.
The encryption payload is typical for ransomware. It scans through directories A:/ to Z:/, encrypts the files it finds using the ChaCha20 algorithm – the same algorithm used by Vice Society – and appends the extension .rhysida to encrypted files. Files in directories used by the operating system, such as /Windows and /Program Files, as well as files with 27 specific extensions, such as .bat and .bin, are not encrypted by the malware.
After encryption, the malware displays a ransom note as a pdf and as a background wallpaper located at C:/Users/Public/bg.jpg. The ransom note calls Rhysida a “cybersecurity team” and instructs victims to visit the group’s leak site and provide their unique identification key to start ransom negotiations.
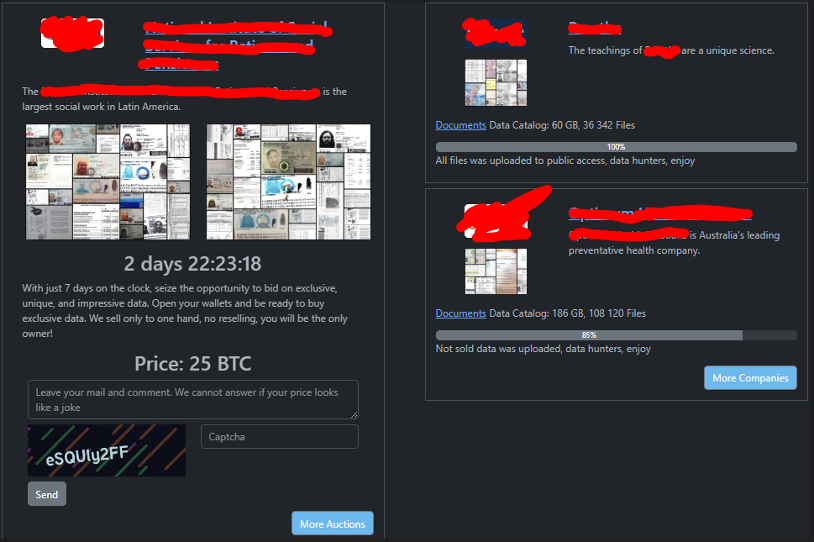
When a victim visits the group’s website, they see the following logo (including the Rhysida centipede the group is named for).

The website also displays a list of victims, including those whose data has been fully or partially published and those for which an “auction” is open before the data is published. At the time of writing this post, the price for the latest victim’s data was 25 Bitcoin, roughly US $730,000. It also appears that the group can sell parts of the data and publish the rest, as seen for the victim at the bottom right-hand side of the figure below.
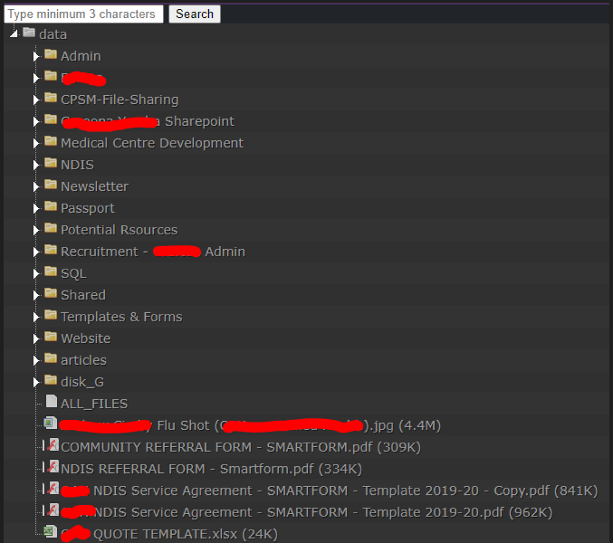
Published files for each victim are available on a dedicated part of the website, where they can be browsed, searched or downloaded. The example below contains the leaked files for one healthcare victim.
Rhysida activity and victims
As of writing this post, Rhysida has claimed 41 victims on their website. Nineteen victims were claimed in June, 17 in July and five up until mid-August. Four of those victims were published after the HHS issued its alert, which indicates that the group has not stopped. Rhysida was the eighth most active ransomware group in the seven days prior to August 16, behind LockBit, NoEscape, ALPHV, Akira, 8Base, Play and Medusa.
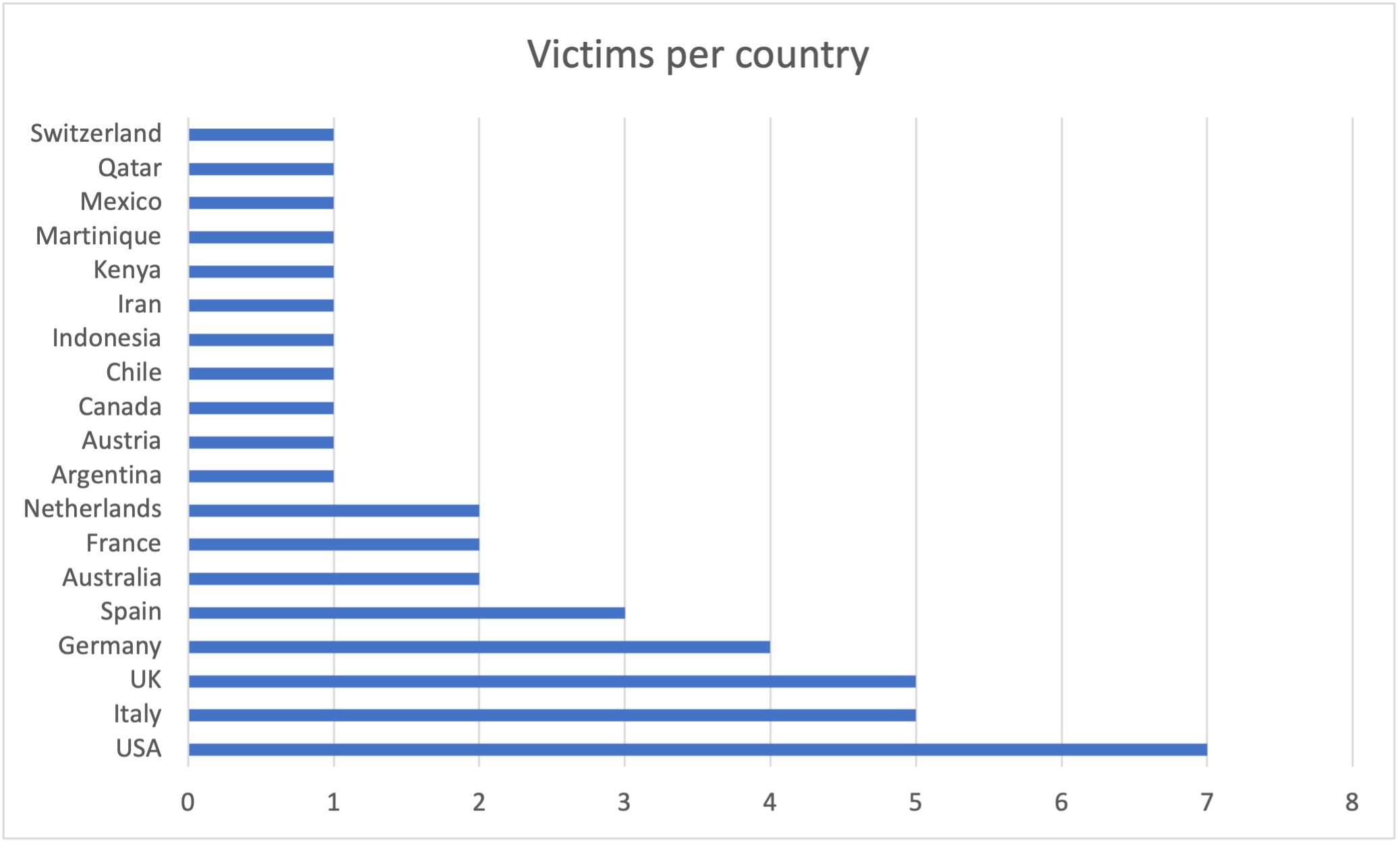
victims are based in eight European countries, with Italy being the most popular. The remaining 11 victims are distributed across the globe, without a clear geographical preference.
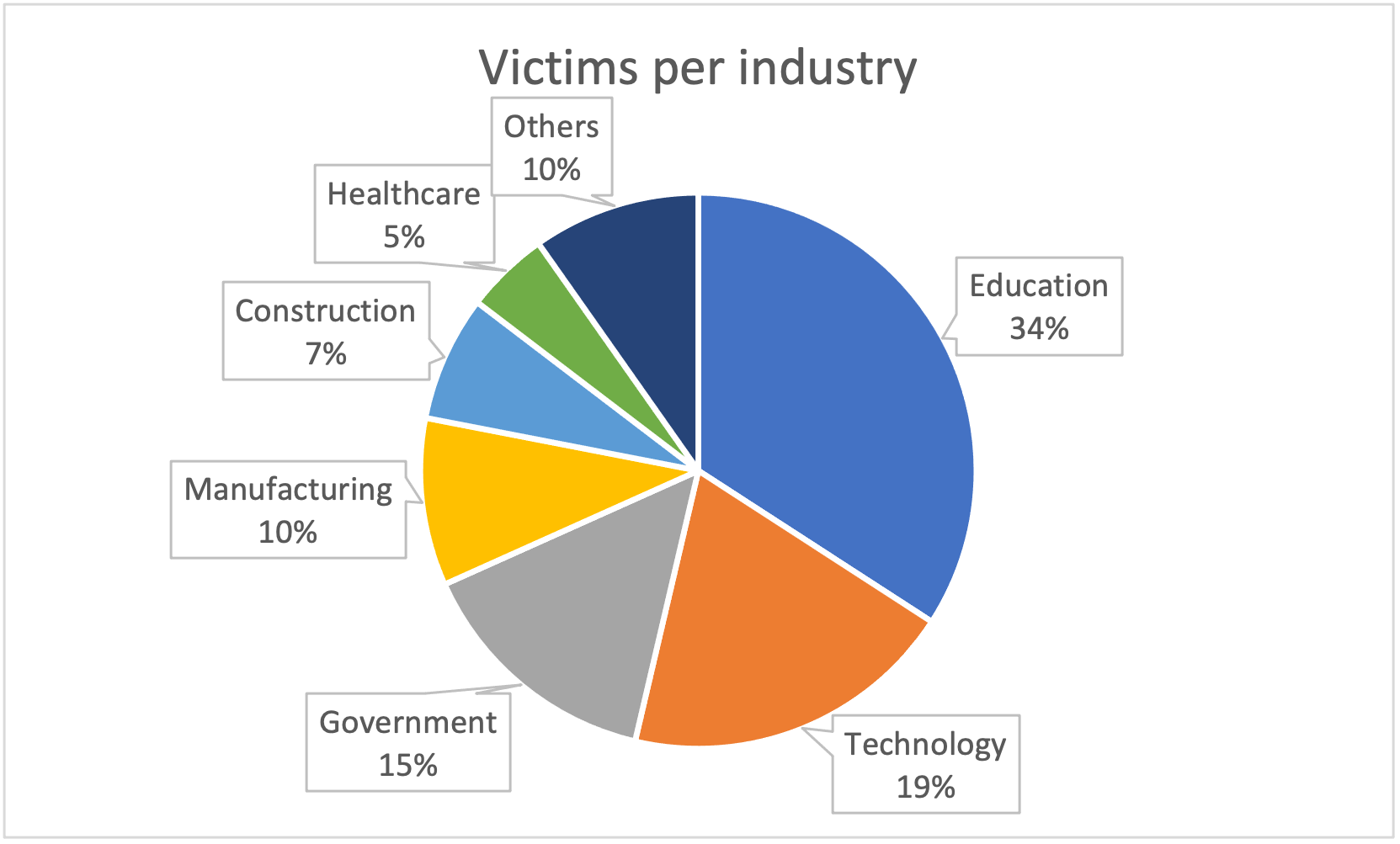
Victims are heavily concentrated in the education (34%), technology (19%) and government (15%) sectors.
Observed TTPs used by Rhysida
| Initial Access | Rhysida is delivered through a variety of mechanisms that can include phishing and being dropped as secondary payloads from command and control (C2) frameworks like Cobalt Strike. |
| Lateral Movement |
|
| Credential Access | The threat actor used ntdsutil.exe to create a backup of NTDS.dit |
| Command and Control | SystemBC, AnyDesk |
| Defense Evasion |
|
| Impact |
|
Mitigation and how Forescout can help
The TTPs employed by Rhysida lack innovation. They adhere to established methods that are already known and have been well documented for other ransomware groups.
This is positive for defenders, since it means that basic cyber hygiene recommendations are effective against Rhysida. These recommendations include identifying and patching vulnerable devices in your network, segmenting the network to avoid spreading an infection and monitoring network traffic to detect signs of intrusion, lateral movement or payload execution. They are detailed on CISA’s Stop Ransomware project page, especially their ransomware guide.
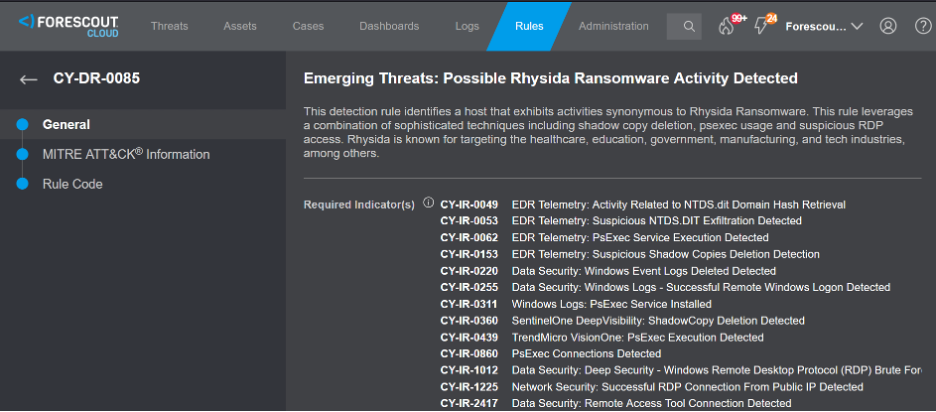
Forescout Threat Detection & Response can detect the execution of Rhysida ransomware with a new dedicated rule – CY-DR-0085 Emerging Threats: Potential Rhysida Ransomware Activity Detected – shown in the image below.
Are you covered for the most common ransomware TTPs?
This recent spate of attacks and the HHS alert about Rhysida reinforce the importance of ensuring your threat detection software covers you for the TTPs commonly used in ransomware attacks. While the TTPs used have remained mostly constant in recent years, ransomware has been evolving rapidly since 2020, with the increased use of double extortion, zero-day exploits and targeted attacks on specific organizations vs. casting a wide net.
Our recent analysis of Common Ransomware TTPs examines 36 techniques used across each stage of an attack and provides specific recommendations against them, including detection with Forescout Threat Detection & Response.