CYBERSECURITY A-Z
What Is DORA in the EU?
The Digital Operational Resilience Act (DORA) is a cybersecurity regulation in the European Union (EU) designed to help protect against evolving digital threats to financial systems. The goal is to strengthen the IT security of financial entities, such as banks, insurance companies and investment firms so Europe’s financial sector stays resilient, even in the event of a severe operational disruption.1
By reshaping how financial firms approach and ensure operational resilience, the European Banking Authority will apply DORA to companies starting January 17, 2025. DORA aims to:
- Improve the sector’s overall security posture
- Enhance consumer trust in the financial system
- Provide a unified risk management framework for managing Information, Communications, and Technology (ICT) risk across the EU
DORA requirements apply to more than 22,000 financial organizations and ICT service providers operating within the EU, plus the ICT infrastructure supporting them from outside the EU, according to PwC.2 Companies impacted by DORA include:
- Credit institutions
- Central securities depositories
- Data reporting service providers
- Crowdfunding service providers
- Payment institutions
- Central counterparties
- Insurance and reinsurance undertakings
- Securitization repositories
- Account information service providers
- Trading venues
- Insurance intermediaries
- Electric money institutions
- Trade repositories
- Institutions for occupational retirement provision
- Non-financial entity: ICT service provider*
- Investment firms
- Managers of alternative investment funds
- Credit rating agencies
- Crypto-asset service providers
- Management companies
- Administrators of critical benchmarks
Failure to comply with DORA can result in GDPR-class sanctions with fines that can amount to:
- Two percent of an organization’s total annual worldwide turnover
- Or three times the profit a financial organization has made because of the rule violation
*This could be an internet service provider, a cloud service provider, a telecommunications company, an outsourced technology provider, and more.
Why DORA Is Needed
According to the EU parliament, a risk management framework such as DORA is needed because “the financial sector is increasingly dependent on technology and on tech companies to deliver financial services. This makes financial entities vulnerable to cyber-attacks or incidents.”3
Forescout’s 2024 research on the riskiest devices found that financial firms rank fourth for most risky devices across 10 major industries, behind manufacturing, education, and technology.
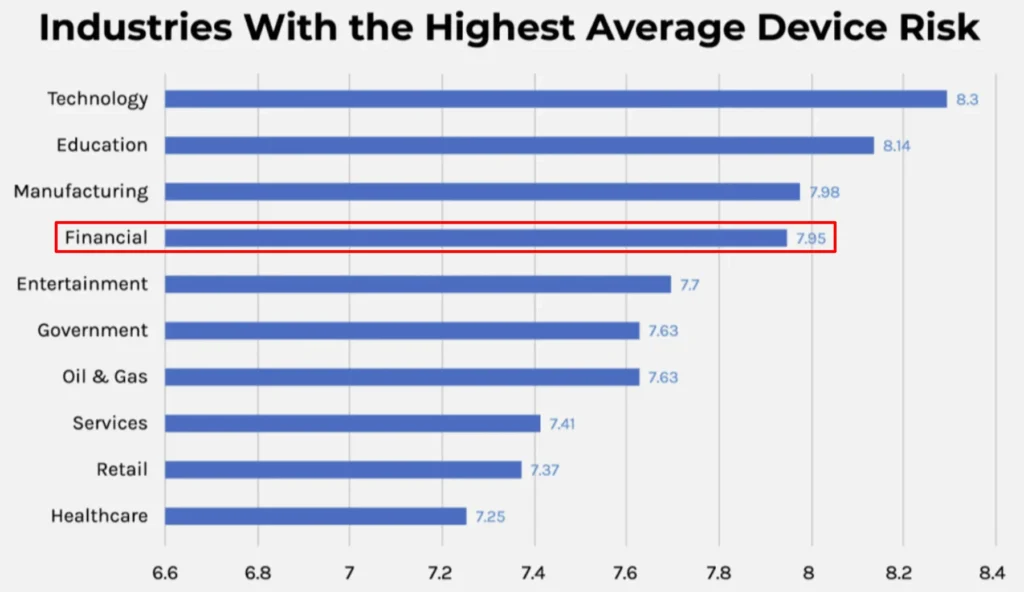
From ransomware as a service to digital fraud to AI-based scams, the financial industry is a prime target for digital crime. Between cyberinsurance premiums growing and spending increases in cybersecurity budgets, financial services organizations are seriously invested in shoring up their digital security.4
With companies in the financial sector relying on digital technology, more are using cloud-based fintech for analytics, artificial intelligence (AI) and other applications. Many are also adopting cloud models to stay competitive and keep pace with customer needs. With more applications and server infrastructure moving to the cloud, the attack surface is growing.
As of December 2022, banks had moved 15 percent of their workload to the cloud – twice that of 2021, stated Accenture.5 In the next three years, 61 percent plan to shift most or all of their data center workloads to the cloud, according to American Banker’s Bank of the Future 2024 research report.6
Plus, the financial industry works with, and manages, many third-party partners and vendors – often requiring digital connections on the back end. According to Fabio Colombo, Global Financial Services Security Lead for Accenture, “ICT providers are one of the…big topics for this regulation, because ICT risk is not only in the financial institution, but is in the supply chain and the broader third and fourth parties that support these type of services.”7 As a result, DORA also applies to these vendors and service providers in ICT.
Prior to DORA, EU members states managed ICT risk in varied ways across a disjointed regulatory environment. Though frameworks like the NIS2 directive addressed a wide range of sectors, they didn’t address the financial industry or fall under enforceable regulation.
What Are DORA’s Five Pillars?
Covering the following five areas, DORA builds on an established regulatory foundation for managing risk within ICT. These areas – or pillars – are referred to as secondary legislation drawn up by the European Supervisory Authorities and the European Commission.
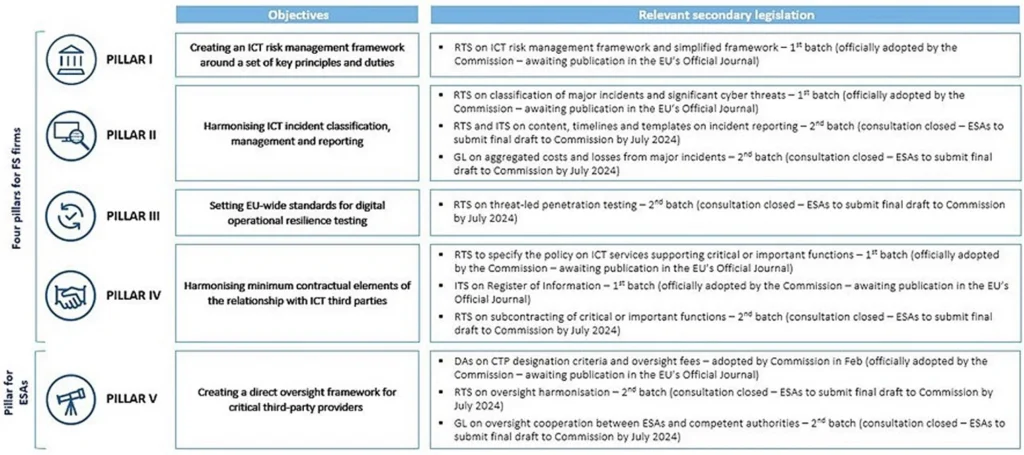
Source: Deloitte, The EU’s Digital Operational Resilience Act (DORA)
ICT Risk Management
Under DORA, a financial firm’s management team is accountable for managing ICT risks. Among other responsibilities, this includes determining and approving the firm’s resilience strategy, and reviewing and approving its policy on the use of ICT Third Party Service Providers (TPPs). In-scope firms face penalties for breaches of DORA, including criminal penalties, administrative fines, and mandatory implementation of remedial measures. Members of the firm’s management team can also be fined and named individually in public decisions.
Incident Reporting
Standardizes the process for logging and reporting ICT-related incidents, with the goal of streamlining a number of existing EU incident reporting obligations that apply to financial firms. DORA adds “significant cyber threats” to the list of events firms must classify, and requires firms to record these incidents and submit an initial report to regulators within four hours of classifying an incident as “major”—and no later than 24 hours after it is detected. Firms must report the following details: number of clients/users affected, amount of data lost, geographical spread, economic impact, duration and service downtime, and reputational impact. Should a client or counterparty be exposed to a significant threats, firms must notify them and provide information on measures they can take to defend against the threat.
Digital Operational Resilience Testing
Mandates regular, rigorous testing of digital resilience. All in-scope firms must provide evidence of appropriately and at least annually testing security and resilience of their “critical ICT systems and applications.” They must also “fully address” any vulnerabilities discovered during testing. Firms deemed of high importance and maturity by a Regulatory Technical Standard will need to conduct advanced Threat-Led Penetration Testing (TLPT) every three years, and include all TPPs supporting Critical or Important Functions (CIFs) in these testing exercises.
TPR Management
Requires that firms monitor and manage risks associated with TP service providers. Firms must negotiate and include specific contractual terms in ICT outsourcing contracts, such as the TPP providing “unrestricted access to premises” in contracts supporting CIFs.
Information and Intelligence Sharing:
Promotes the exchange of threat intelligence among financial entities to promote awareness of emerging threats and best practices for mitigation. European financial institutions are required to share indicators of compromise; adversaries’ tactics, techniques, and procedures; security alerts; and configuration tools in a safe, secure, and trusted manner.
Analyst Perspectives on DORA
Implementation Challenges
Analysts firms have highlighted the significant operational and technological challenges financial institutions will face implementing DORA’s requirements. Large financial services firms with mature cybersecurity measures will likely only need to make incremental changes to satisfy DORA. However, smaller firms and ones with less robust security postures might feel burdened by DORA. They will need to conduct a thorough gap analysis to determine where their current practices fall short and address these shortcomings before the regulation fully applies in 2025.
As Deloitte says, “The DORA presents a high level of prescriptiveness and a particularly challenging timeline. Although firms in scope were officially granted a two year-long implementation period, a good portion of the technical detail required to build effective compliance was not available right after entry into force of the DORA text.” Adding to this, Karine Pariente, Partner, PwC France, underscores, “The main challenge will be to coordinate actions with the main stakeholders involved. This requires strengthening governance and can only be achieved by involving top management.”
Compliance Costs
Financial consulting firms such as Thomson Reuters suggest that organizations will need to make substantial investments in:
- Technology upgrades
- Risk management infrastructure
- Cybersecurity capabilities
A survey by McKinsey found that “One large FI reported that its final planned DORA implementation spend across the group amounted to nearly €100 million…” The consulting firm expects similar costs across the financial industry—”particularly at large companies or those that struggle to adopt a risk-based approach to scoping.”
Third-Party Risk Oversight
Analysts emphasize the act’s stringent requirements for managing and monitoring ICT TP service providers, which will require more comprehensive vendor management processes. As McKinsey emphasizes, “To manage TPR effectively, financial institutions must make significant efforts on two fronts: ensuring comprehensive oversight of all ICT service providers and their associated risk and proactively managing the digital risk associated with critical ICT TP service providers.”
Moreover, any company providing ICT services to the financial sector must also ensure its cybersecurity measures are robust and compliant with DORA.
How Forescout Helps With DORA Compliance
As financial entities strive to follow the stringent regulations in DORA, Forescout is a strategic partner that helps fortify operational resilience. Here’s how the Forescout Platform delivers unmatched support across all five pillars of DORA:
- Risk Management: Gain full visibility into IT, OT, and IoT assets, both managed and unmanaged, to reduce the risk of potential attacks. Pair this with the Forescout Platform’s comprehensive capabilities for network security, risk and exposure management, and threat detection and response to strengthen supply chain security.
- Incident Management: Forescout facilitates rapid threat detection and response to security incidents with automated solutions. Real-time monitoring and incident response capabilities empower organizations to adhere to DORA’s mandates for timely and accurate reporting.
- Operational Resilience Testing: Forescout’s continuous asset monitoring and threat detection and response capabilities help organizations meet DORA’s operational resilience requirements. By continuously assessing and adapting their cybersecurity posture, organizations can maintain compliance and operational strength.
- TPR: The Forescout Platform supports financial organizations by providing enhanced visibility over their third-party service providers, enabling them to manage and secure these critical digital service contributors.
- Information Sharing: Securely share incident reports, logs, and audit data securely with stakeholders. Plus, benefit from Vedere Labs’ threat intelligence, which is integrated into the Forescout Platform and shared with the broader security community.
Go deeper: Get our DORA Mapping guide today.
Schedule a demo to see how the Forescout Platform continuously identifies, protects and ensures the compliance of all managed and unmanaged assets without business disruption
1 European Insurance and Occupational Pensions Authority: (DORA). Accessed December 3, 2024 at the following source: EIOPA
2 PwC. DORA and its impact on UK financial entities and ICT service providers. Accessed December 3, 2024 at the following source: PwC UK
3 European Insurance and Occupational Pensions Authority. Digital Operational Resilience Act (DORA). Accessed December 3, 2024 at the following source: EIOPA
4 Moody’s Ratings. Cyber budgets increase, executive overview improves, but challenges lurk under the surface, September 26, 2023. Accessed December 3, 2024 at the following source: Moody’s Cyber Survey
5 Accenture. Banks need a flight plan to navigate the cloud, December 7, 2022. Accessed December 3, 2024 at the following source: Banks Need a Flight Plan to Navigate the Cloud | Accenture
6 Matt Kuhrt, American Banker. Cloud migration hits its stride, June 21, 2024. Accessed December 3, 2024 at the following source: Cloud migration hits its stride | American Banker
7 World Finance and Fabio Colombo of Accenture. What the Digital Operational Resilience Act means for third party ICT providers. Viewed December 2, 2024 at the following source: World Finance