CYBERSECURITY A-Z
What Is Network Segmentation?
It is the architecture of dividing and subdividing a network into distinct segments or subnets for better operational and cybersecurity control. The goal of segmenting a network is to limit the blast radius of the attack surface by separating core functions and using access control to limit a user’s ability to cause harm — intentionally or unintentionally.
The National Institute of Standards and Technology (NIST) defines network segmentation as “splitting a network into subsections where firewalls reject unnecessary traffic for that section.”
Commenting on this NIST definition in a joint report, the Cybersecurity and Infrastructure Agency (CISA) and the National Security Agency (NSA) states: “This is a foundational cybersecurity principle, which, when properly implemented, can isolate malicious activities and vulnerabilities to a limited part of the network and minimize the effect of a breach.”1
In a similar overview of network segmentation, CISA defines it as “a physical or virtual architectural approach dividing a network into multiple segments, each acting as its own subnetwork providing additional security and control.”2 CISA further explains that segmentation limits access to devices, data, and applications and restricts communications between networks.
Why Is Network Segmentation Necessary?
Organizations traditionally focused their network security measures on protecting the network perimeter, relying on firewalls to keep bad actors off the network and limit the attack surface. However, that approach fails to prevent authenticated users from doing damage. CISA and the NSA highlighted the danger of not restricting users once they gain initial authentication: “When using this perimeter-focused approach to network security, MCAs [malicious cyber actors] who breach that first line of defense will have access to target user traffic and organization resources, exploiting any vulnerable or unauthenticated network protocols and delivering malicious payloads.”3
The threat also extends beyond malicious actors. Well-intended employees, remote workers, partners, automated applications, and other ‘friendly’ sources may unintentionally cause harm after gaining authenticated access to the network. For example, remote workers with virus-infected devices may pass through the firewall and spread malware across the enterprise. By segmenting the network, IT can establish policies and use access control measures to limit each user’s access to only the resources on a subnet or within specific subnetworks, such as a local area network, they need to perform their individual job role, preventing lateral movement across the entire network and unnecessary access to additional resources. In this way, the organization minimizes the attack surface and damage from a bad actor (or a good actor with a compromised device with malware).
The Benefits of Network Segmentation
While network segmentation offers benefits to any organization, it proves most valuable in three common use cases:
- Keeping OT separate from IT
- Supporting Zero-Trust Architecture (ZTA)
- Ensuring regulatory compliance
By applying network segmentation, IT can separate and protect the OT and IT/business networks from one another. Figure 1 (below) shows how a firewall does little to protect OT and IT from each other once a bad actor has entered the network, while Figure 2 (below) demonstrates how the use of network segmentation keeps the different resource types separated.
“Properly implemented Demilitarized Zones1 (DMZs) and firewalls can prevent a malicious actor’s attempts to access high-value assets by shielding the different networks from unauthorized access,” says CISA. Such a strategy dramatically reduces the effectiveness of many of today’s attack types, such as phishing.

[Source: CISA]
Of course, IT must make use of firewalls and DMZs in conjunction with higher-level measures, such as designing, implementing and enforcing policies and controls to monitor and regulate system access as well as the movement of network traffic and workloads between zones — which may require managing network congestion.
Supporting Zero Trust Architecture
Organizations must understand what is on their network before they can develop a plan to secure it. This means knowing each and every user and device seeking network access. “Current interest in network segmentation is being driven by Zero Trust,” according to Gartner.[iv]
Segmenting the network for each user and asset (or device) helps to improve security and
is a key capability under a Zero Trust architecture (ZTA). In Network Segmentation, IT policies grant proper network access to users/devices according to their role, such as moving printers to their own VLANs or granting developers access to certain systems while blocking others from them.
Consider a healthcare industry example: IT can set up a security policy that states, “medical devices can connect only to the medical records server” or “a security camera (which can be an IoT device) can connect only to the video server.” This approach prevents devices in a guest network from having access to these endpoints and limits access to their functions without connecting to the outside Internet. As a result, any unauthorized user cannot gain access to devices located in the network’s other zones. If, for example, a medical device moves within the network, the policy follows that endpoint device, eliminating the need to reprogram the network.
Ensuring Regulatory Compliance
As the previous section demonstrates, network segmentation allows for the creation of different zones for varying types of servers and devices, while simplifying the audit process to ensure compliance with regulatory standards. Expanding on the healthcare industry example, IT can adhere to HIPAA regulations by storing patient records in their respective compartments to ensure separation between patient data, procedure records, and doctors’ notations and simultaneously restrict the access of medical devices within their zones – making them unreachable from any other network or device.
It’s not just highly regulated industries like healthcare and finance (SWIFT, NYDFS) that benefit greatly from network segmentation. Even eCommerce companies use network segmentation to follow the PCI-DSS standard to receive credit card payments. PCI-DSS provides guidance on creating clear separation of data within the network, such as separating the network for Payment Card authorizations from the network for Wi-Fi traffic. Considering the number of industries that operate by accepting credit card payments, network segmentation helps thousands or millions of organizations across a wide range of industries.
How Forescout Can Help
Forescout solutions, particularly Forescout eyeSegment for network segmentation, supports all three common use cases described above.
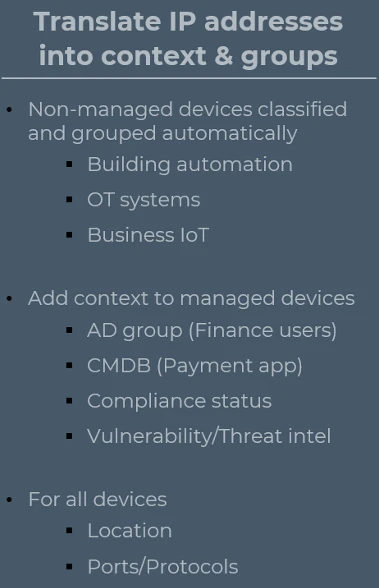
Forescout eyeSegment can translate IP addresses into context and, enabling IT and network administrators to:
- Classify and group non-managed devices automatically. These can include devices for building automation, OT systems, or business IoT.
- Add context to managed devices, grouping them in various ways, such as Finance users, payment apps, and compliance status. You can even group them based on the vulnerability intelligence which Forescout gathers about each device, as well as by location and ports/protocols.
- Visualize traffic flows by automatically mapping them to a logical taxonomy of users, applications, services, devices, and visibility.
Supporting Zero Trust Architecture
eyeSegment can continuously monitor any network type for new device events, traffic patterns, and anomalies that conflict with your defined segmentation policies. This understanding of your network traffic baseline will help you to design effective zero-trust policies and enforce least-privileged access.
By combining Forescout eyeSegment and eyeExtend, your IT team can implement a single set of policies across multi-vendor environments and multiple network domains, monitor happenings according to those policies, and respond appropriately. Forescout even provides closed–loop feedback so that your organization can improve segmentation controls over time – without impacting the business.
Forescout eyeSegment can provide an added aspect of compliance via network segmentation policies. Consider Figure 3 (below).
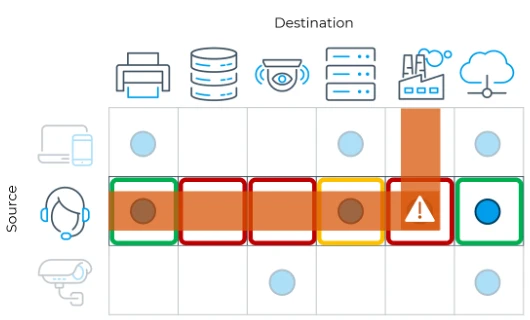
Figure 3. Segmenting for Compliance
Forescout can map all traffic to a connectivity matrix made up of ‘Sources’ and ‘Destinations’. You can display these by network segment, as well as device, user, or business groups. Wherever a blue dot is seen on the matrix, that indicates traffic detected between those two groups. Forescout’s strength in classifying devices and retrieving other information that yields contextual awareness beyond a simple IP underpins this unique way of viewing traffic flows.
The focus is placed on traffic from the service desk and the policies that allow service desk personnel to access only the resources needed to perform their jobs. You can create policies that allow access to printers and the internet, while granting only limited access to the internal servers these workers need. Once you put in place your policy for ‘Service Desk’, you will automatically restrict these workers from sensitive zones, such as database servers, surveillance systems, and manufacturing lines. Alerting and block will occur for any violating traffic.
As with Zero Trust, the path to successful network segmentation involves a process of continuous improvement. Forescout has helped organization of all levels of segmentation maturity to improve their compliance and security postures.
Contact Forescout today to experience a demo of Forescout eyeSegment and eyeExtend for yourself.
1 CISA and the NSA, Implement Network Segmentation and Encryption in Cloud Environments, March 2024
2 CISA, Layering Network Security Through Segmentation, January 2022. Accessed November 8, 2024 from the following source https://www.cisa.gov/resources-tools/resources/layering-network-security-through-segmentation-infographic
3 CISA and the NSA, Implement Network Segmentation and Encryption in Cloud Environments, March 2024
4 Gartner, Implementing Segmentation for Zero Trust Networking, January 25, 2024. Accessed November 8, 2024 from the following source https://www.gartner.com/en/documents/5141631