CYBERSECURITY A-Z
What Is a Zero Trust Architecture?
The SANS Institute states that “Zero Trust Architecture (ZTA) is a security model based on the principle of least privilege. This principle specifies that users and devices receive only the permissions necessary to perform their tasks.”
Least privilege means that users and devices are only granted the permissions they need to perform their tasks. Least privileged access helps reduce the attack surface of agencies and enterprises, making it more difficult for attackers to access sensitive data.1
The National Institute of Standards and Technology (NIST) Special Publication (SP) 800-207 builds on the SANS definition of ZTA. Zero Trust security assumes that the network is already compromised or breached. By assigning least privileged access based on identity, behavior, and context, network administrators and security staff can minimize the uncertainty in enforcing session-based least privileged access decisions.2
“Compromised” is a critical term. Zero Trust assumes that no user or device is inherently trusted, even if they are already inside the network. This is much different than traditional perimeter-based security models where users and devices inside and outside the network are trusted by authentication methods.
Why Is a Zero Trust Architecture Necessary?
It is now virtually impossible to enforce access controls at the perimeter of the enterprise environment and assume that all subjects (end users, applications, etc.) operating within it can be trusted. As enterprise resources and data have become more and more distributed across both on-premises environments and multiple clouds, protecting them has become more difficult. At the same time, users need access from anywhere, any time, from any device to support their work efforts. (think remote workers everywhere). As a result, data is stored, transmitted, and processed across different network boundaries under the control of various organizations to meet evolving business needs.
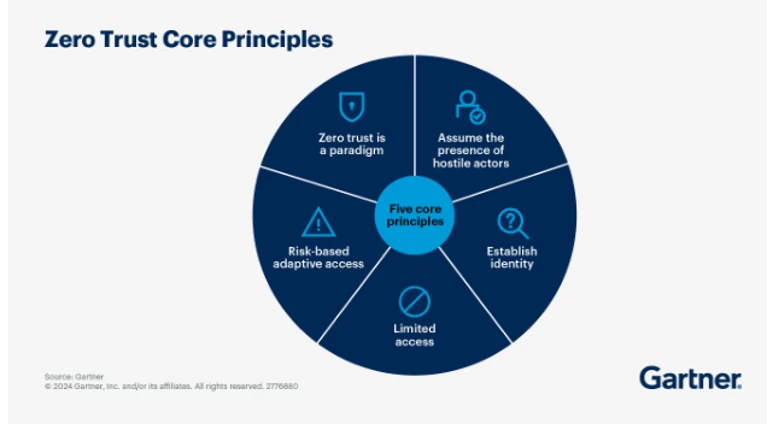
Based on these core principles, Forescout recommends all agencies and enterprises, regardless of size, implement Zero Trust Architecture to adapt to a shifting threat landscape. ZTA should be used in conjunction with a context-aware cybersecurity approach that goes beyond perimeter-based defenses.3
What Does a Zero Trust Architecture Look Like?
The Cybersecurity and Infrastructure Agency (CISA) provides a Zero Trust Maturity Model (ZTMM) that helps guide priorities as it pursues ZTA. It focuses on five distinct pillars – Identity, Devices, Networks, Applications and Workloads, and Data. Cross-cutting capabilities include Visibility and Analytics, Automation and Orchestration, and Governance (see below).
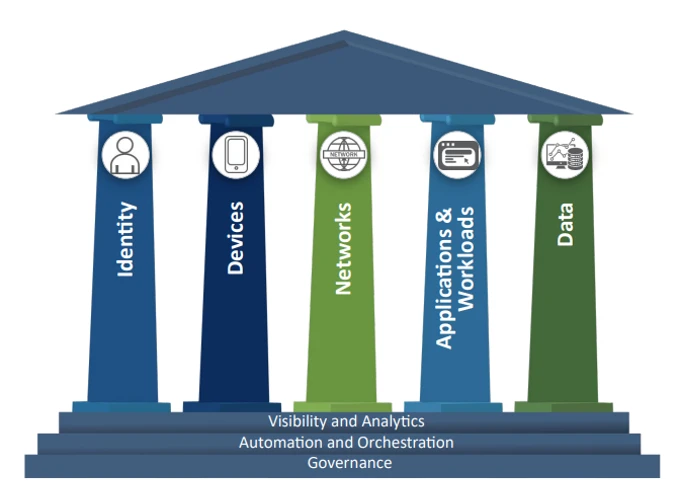
[Source: CISA “Zero Trust Maturity Model”]
Using this model, CISA advises that organizations can align their implementations with the seven tenets of zero trust as outlined in NIST SP 800-207:
- All data sources and computing services are considered resources.
- All communication is secured regardless of network location.
- Users are granted access to individual enterprise resources on a per-session basis.
- Access to resources is determined by dynamic policy.
- The enterprise monitors and measures the integrity and security posture of all owned and associated assets.
- Dynamic resource authentication and authorization are strictly enforced before allowing access.
- The enterprise collects as much information as possible about the current state of assets, network infrastructure, and communications and uses it to improve its security posture.
“This shift [to ZTA] provides the visibility needed to support the development, implementation, enforcement, and evolution of security policies,” concludes CISA.4
Forescout reminds customers that it is important to understand that ZTA is a security design approach, not a single-vendor solution or even a single architecture model. For this reason, CISA insists that ZTA implementations that align with the concepts and principles in NIST SP 800-207 can be deployed in whole or in part, gradually enabling organizations to incorporate ZTA into their legacy environments. This makes for a process of continuous improvement that is more pragmatic to achieve ZTA goals that align with an organization’s own priorities based on risk, cost, and resources. Below is a sample ZTA architecture demonstrating a hypothetical organization’s ideal starting point.
Sample ZTA Logical Architecture
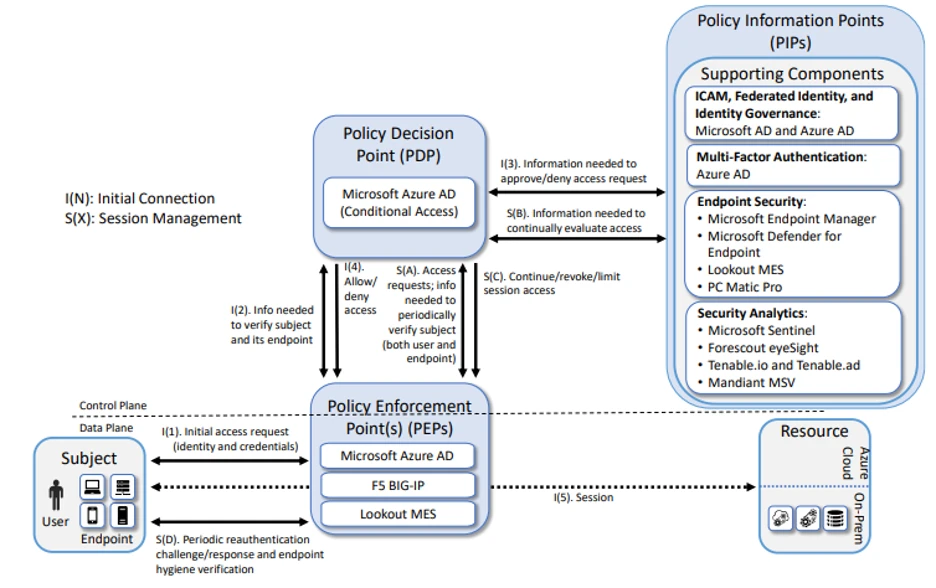
[Source: NIST SPECIAL PUBLICATION 1800-35B “Implementing a Zero Trust Architecture”]
Note: This kind of architecture is modular — and allows for gradual expansion and continuous improvement.
ZTA in Action
For each data access session requested, ZTA verifies the requester’s:
- Identity
- Role
- Authorization to access the requested assets
- The requesting device’s health and credentials
- And other relevant information
When defined policies are met, ZTA dynamically creates a secure connection to protect all information transferred to and from the accessed resource. ZTA delivers real-time, continuous behavioral analysis and risk-based assessment of the access transaction or session.
The Benefits of ZTA
According to CISA, “Regardless of starting point, successful zero trust adoption can produce numerous benefits such as improved productivity, enhanced end-user experiences, reduced IT costs, flexible access, and bolstered security.”5
Through our own work with customers and partners, we see organizations benefitting in these specific ways:
- Improved remote worker support
- Location-agnostic protection of resources and assets
- Provisioning of verified “healthy” devices
- Improved end-user experience
- Limited insider threat
- Limited movement after a breach
- Improve incident detection, response, and recovery
- Protection of sensitive corporate data
- Improved visibility into specific users accessing specific resources
- Dynamic, risk-based assessment of resource access
The Challenges to Adopting ZTA
Many organizations want to implement ZTA, but various organizational factors can hold them back. As noted in the opening section above, legacy systems often rely on “implicit trust,” with access and authorization rarely assessed and lacking dynamism. Changing to a dynamic, real-time ZTA requires recognizing that the technology landscape continues to evolve, as does the threat landscape. The progression involves buy-in from senior leadership, IT staff, data and system owners, and users.
Many organizations want to implement ZTA, but various organizational factors can hold them back. As noted in the opening section above, legacy systems often rely on “implicit trust,” with access and authorization rarely assessed and lacking dynamism. Changing to a dynamic, real-time ZTA requires recognizing that the technology landscape continues to evolve, as does the threat landscape. The progression involves buy-in from senior leadership, IT staff, data and system owners, and users.
-
- Lack of adequate asset inventory and management needed to fully understand the business applications, assets, and processes that need to be protected, with no clear understanding of the criticality of these resources.
- Lack of adequate digital definitions, management, and tracking of user roles across the organization is needed to enforce a fine-grained, context-aware access policy for specific applications and services.
- The increasing complexity of communication flows and distributed IT components across environments on-premises and in the cloud make them difficult to manage consistently.
- The business must hire and retain skilled personnel while continuously upleveling and informing IT and security teams.
- The business must hire and retain skilled personnel while continuously upleveling and informing IT and security teams.
- Lack of awareness regarding everything that encompasses the organization’s entire attack surface. Organizations can usually address threats with traditional security tools in the layers that they currently manage and maintain, such as networks and applications. However, elements of ZTA often extend beyond that purview. False assumptions hinder device health understanding, as well as its exposure to supply chain risks.
- Understanding interoperability issues can be challenging, and administrators, security personnel, operators, end users, and policy decision makers may need additional skills and training. Furthermore, organizations often lack the resources to develop necessary policies and to implement a pilot or proof-of-concept project that would inform a transition plan.
- Making progress toward ZTA while balancing priorities and leveraging existing investments.
- Integrating various types of commercially available technologies of varying maturities, assessing capabilities, and identifying technology gaps to build a complete ZTA
- Concern that ZTA might negatively impact the operation of the environment or end-user experience.
- Lack of a standardized policy to distribute, manage, and enforce security policy causes organizations to face either a fragmented policy environment or a lack of interoperability.
- Lack of shared understanding and language of ZTA across the community and within the organization, gauging the organization’s ZTA maturity, determining which ZTA approach is most suitable for the business, and developing an implementation plan.
- The perception that ZTA is suited only for large organizations and requires significant investment rather than understanding that ZTA is a set of guiding principles suitable for organizations of any size.
- Not knowing how to prioritize or scope individual ZTA projects.
- There is not a single ZTA that fits all for both organizations and subsets of their users. ZTAs need to be designed and integrated for each organization and its users based on the organization’s requirements, risk tolerance and its existing technology investments and distributed environments.
How Forescout Can Help You Adopt ZTA
Forescout can enable you to build a robust foundation for your own ZTA based on total visibility, least privilege network access and compliance. For over a decade, we have been providing both government agencies and private enterprises with the guidance and solutions they need to move toward adopting a NIST SP 800-207-based ZTA within their existing multi-vendor environment – from identifying, monitoring and controlling connected assets to orchestrating enforcement and remediation. Customers can benefit from Forescout’s Zero Trust expertise to save time and money by choosing a solution that does not require a total rip and replace of the existing infrastructure.
Read our latest whitepaper to explore how an adaptive approach to Zero Trust can simplify this process and help your organization meet security mandates effectively.
1 SANS Institute, What is a Zero Trust Architecture, August 2, 2023. Accessed November 5, 2024 from the following source: https://www.sans.org/blog/what-is-zero-trust-architecture/
2 NIST SP 800-207: Zero Trust Architecture. 2020. https://nvlpubs.nist.gov/nistpubs/SpecialPublications/NIST.SP.800-207.pdf
3 Gartner, Implement Zero-Trust Architecture to Adapt to a Shifting Threat Landscape. Accessed November 5, 2024 from the following source: https://www.gartner.com/en/cybersecurity/topics/zero-trust-architecture
4 CISA, Zero Trust Maturity Model, April 2023. www.cisa.gov/sites/default/files/2023-04/zero_trust_maturity_model_v2_508.pdf
5 CISA, Zero Trust Maturity Model, April 2023. www.cisa.gov/sites/default/files/2023-04/zero_trust_maturity_model_v2_508.pdf