See it. Secure it. Assure it.
Continuously identify, protect, and ensure the compliance of all cyber assets across your organization
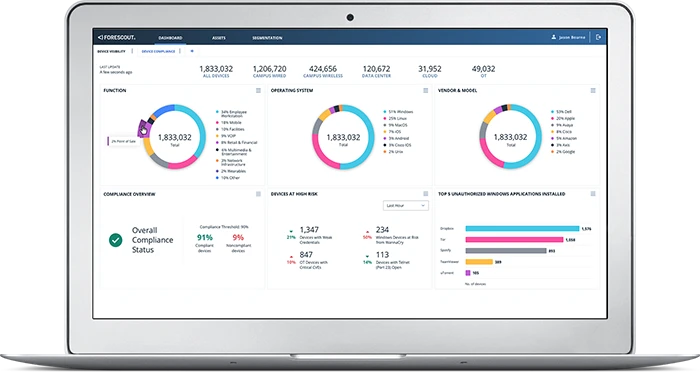
Explore the Forescout Platform
Forescout Forms Strategic
Partnership with Microsoft
Protect every connected asset, both managed and unmanaged
What Are Today’s Riskiest Devices?
Our latest research on the riskiest IT, OT, IoT and IoMT assets spans 19 million global devices across 10 major industries — and nine new categories.

Risk and Exposure Management
Identify, quantify and prioritize cybersecurity risk and compliance
- Cyber asset management
- Visibility & compliance
- Risk prioritization

Network Security
Assess, segment and enforce with proactive and reactive controls
- Network asset control
- Risk & threat containment
- Segmentation management
The Forescout Advantage
The only automated cybersecurity company that continuously identifies, protects and ensures the compliance of all managed and unmanaged assets – IT, IoT, IoMT and OT – so you can more effectively manage cyber risk and mitigate threats.
Vendor & Device Agnostic
Real-Time & Continuous
Managed & Unmanaged Cyber Assets
Flexible Deployment
Converged Platform
Proven at Scale
Dive into the Research
- What’s really happening in state-sponsored activity
- Threat actor trends by name including new threat actor groups
- Why VPNs and network appliances are being targeted at an accelerated rate
Customer Confidence
66M+
Devices Protected
39B+
Unique Data Points Monitored
23+
Years in Business
3000+
Customers Globally
Latest from Forescout
Rough Around the Edges: The State of OT/IoT Routers in the Software Supply Chain
Forescout Forms Strategic Partnership with Microsoft to Secure Managed and Unmanaged Devices
VPN Vulnerabilities As a Target: Virtual Private Not At All
Schedule a Demo
Get a personalized tour of our solutions and see how we can help you automate cybersecurity.