What Devices Pose the Highest Security Risk? Forescout Answers in New Research: The Riskiest Connected Devices in 2024
Defines Emerging Areas of Risk, Showcases Industry Improvements in Device Security and Where Gaps Persist
SAN JOSE, Calif., June 10, 2024 – More than ever this year, attackers are crossing siloes to find entry points across the full spectrum of devices, operating systems, and embedded firmware forming the basis for the report, The Riskiest Connected Devices in 2024. Forescout Technologies, Inc., a global cybersecurity leader, delivers this fourth annual review of data sourced from nearly 19 million devices through its research arm, Vedere Labs, a leading international team dedicated to uncovering vulnerabilities and threats to critical infrastructure.
“The device has evolved from a pure asset to a reliable, sophisticated, intelligent platform for communications and services, driving a transformation in the relationship between devices, people, and networks,” said Elisa Costante, VP of Threat Research, Forescout. “We analyze millions of data points to publish the Riskiest Connected Devices report to integrate important threat context into how organizations use different devices and to redefine what it means to connect and interact securely. Forescout is committed to delivering device threat intelligence that helps organizations respond faster to potential threats and take advantage of opportunities to enhance security postures.”
The Riskiest Connected Devices in 2024 identifies the five riskiest device types in four categories, IT, IoT, OT and IoMT. Here are the key highlights.
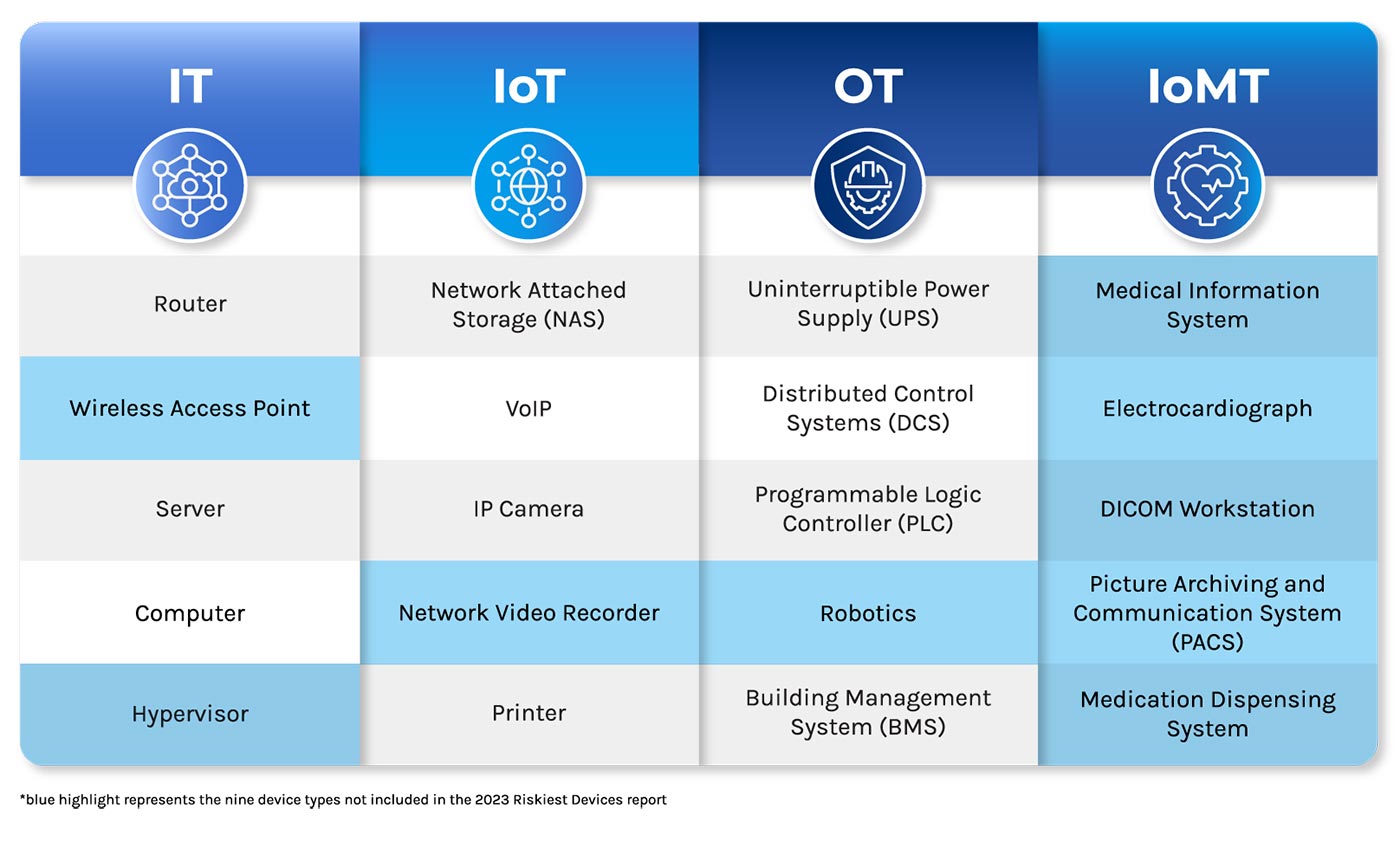
Most Risky: IT Devices
IT devices – network infrastructure and endpoints – still account for the most vulnerabilities at 58% despite being down from 78% in 2023.
Network infrastructure devices – routers and wireless access points – are often exposed online and have dangerous open ports. Endpoints – servers, computers and hypervisors – remain high-risk as entry points for phishing or because of unpatched systems and applications.
At the beginning of 2023, endpoints were riskier than network devices. At the end of 2023, there was a reversal in the number of vulnerabilities found and exploited in network infrastructure devices. Today, network equipment has become the riskiest IT device category surpassing endpoints.
Persistent Risk: IoT Devices
IoT devices with vulnerabilities expanded by 136% since 2023.
The riskiest IoT devices include the most persistent suspects – NAS, VoIP, IP cameras and printers. These are commonly exposed on the internet and have been historically targeted by attackers. This year’s analysis uncovered one IoT device making the Riskiest Connected Devices list for the first time: Network Video Recorder (NVR).
NVRs sit alongside IP cameras on a network to store recorded video. Like IP cameras, they are commonly found online and have significant vulnerabilities that cybercriminal botnets and APTs have exploited.
Ubiquitous and Insecure: OT Devices
Industrial robots debut as an area of emerging risk for OT devices.
The riskiest OT devices include the critical and insecure-by-design PLCs and DCSs. It also consists of the UPSs in many data centers with default credentials — and the ubiquitous, often invisible building automation systems.
Industrial robots make the list of Riskiest Connected Devices for the first time. Often used in logistics and military applications, robots are growing in use in industries like electronics and automotive manufacturing. Many robots share the same security challenges as other OT equipment, including outdated software, default credentials, and lax security postures.
Notable Changes in Healthcare Device Security: IoMT Devices
Healthcare is no longer the industry with the riskiest devices, but IT equipment for medication dispensing systems is the second-most exposed IoMT device type.
Just one year after the 2023 analysis highlighted the high level of device risk within the healthcare industry, our research today indicates that many organizations are closing ports by replacing remote management of devices from Telnet to SSH. Healthcare marked the highest decrease in open ports from 10% in 2023 to just 4% this year. Healthcare also had the highest decline in RDP from 15% to just 6%.
Despite this good news, IoMT devices – the IT equipment used for healthcare like medical information systems and workstations – continue to pose a risk for the industry, especially in medication dispensing systems. Medication dispensers have been known to be vulnerable for almost a decade, yet they represent the sixth most vulnerable device type overall and the second most in the category.
“Modern risk and exposure management must include devices in every category, to identify, prioritize and reduce risk across the whole organization. Beyond risk assessment, risk mitigation should use automated controls that don’t rely only on security agents and also apply to the whole enterprise instead of silos like the IT network, the OT network, or specific types of IoT devices,” adds Costante.
Among the immediate steps organizations can take to reduce device risk are:
- Upgrade, replace or isolate OT and IoMT devices running legacy operating systems known to have critical vulnerabilities.
- Implement automated device compliance verification and enforcement to ensure non-compliant devices cannot connect to the network.
- Improve network security efforts, including segmentation, to isolate common, exposed devices such as IP cameras and dangerous open ports such as Telnet.
Understanding the perceptions of the riskiest devices is vital to define a roadmap for the key elements of cyber-defense to reduce risk. To read the full report and learn more, visit:
- Riskiest Connected Devices in 2024
- Check out the blog: What are the riskiest connected devices right now?
- Hear from the research team, register to join the webinar based on the report
About Forescout
The Forescout cybersecurity platform offers comprehensive asset intelligence and control across IT, OT, and IoT environments. Trusted by Fortune 100 organizations, government agencies, and large enterprises for over two decades, Forescout serves as a cornerstone for managing cyber risk, ensuring compliance, and mitigating threats. With seamless context sharing and workflow orchestration integrated with over 100 security and IT products, Forescout enhances the effectiveness of every cybersecurity investment.
Forescout Research Vedere Labs leads the industry in device intelligence, providing unique and proprietary threat intelligence that fuels the Forescout platform.
Media Contacts:
Rose Ross
OMarketing for Forescout
[email protected]
Sarah Olney Ross
Omarketing for Forescout
[email protected]
Jenna Shikoff
RH Strategic for Forescout
[email protected]