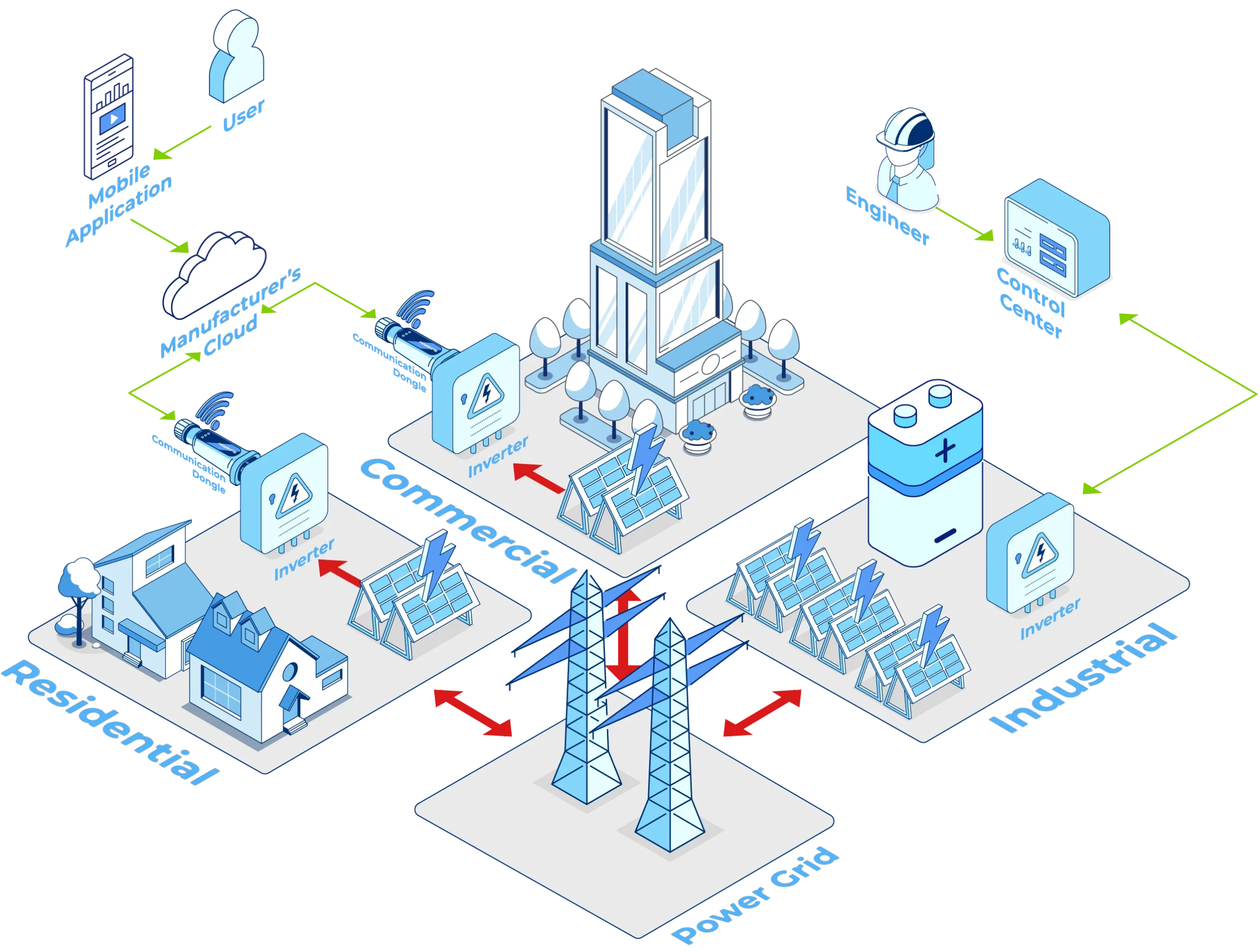
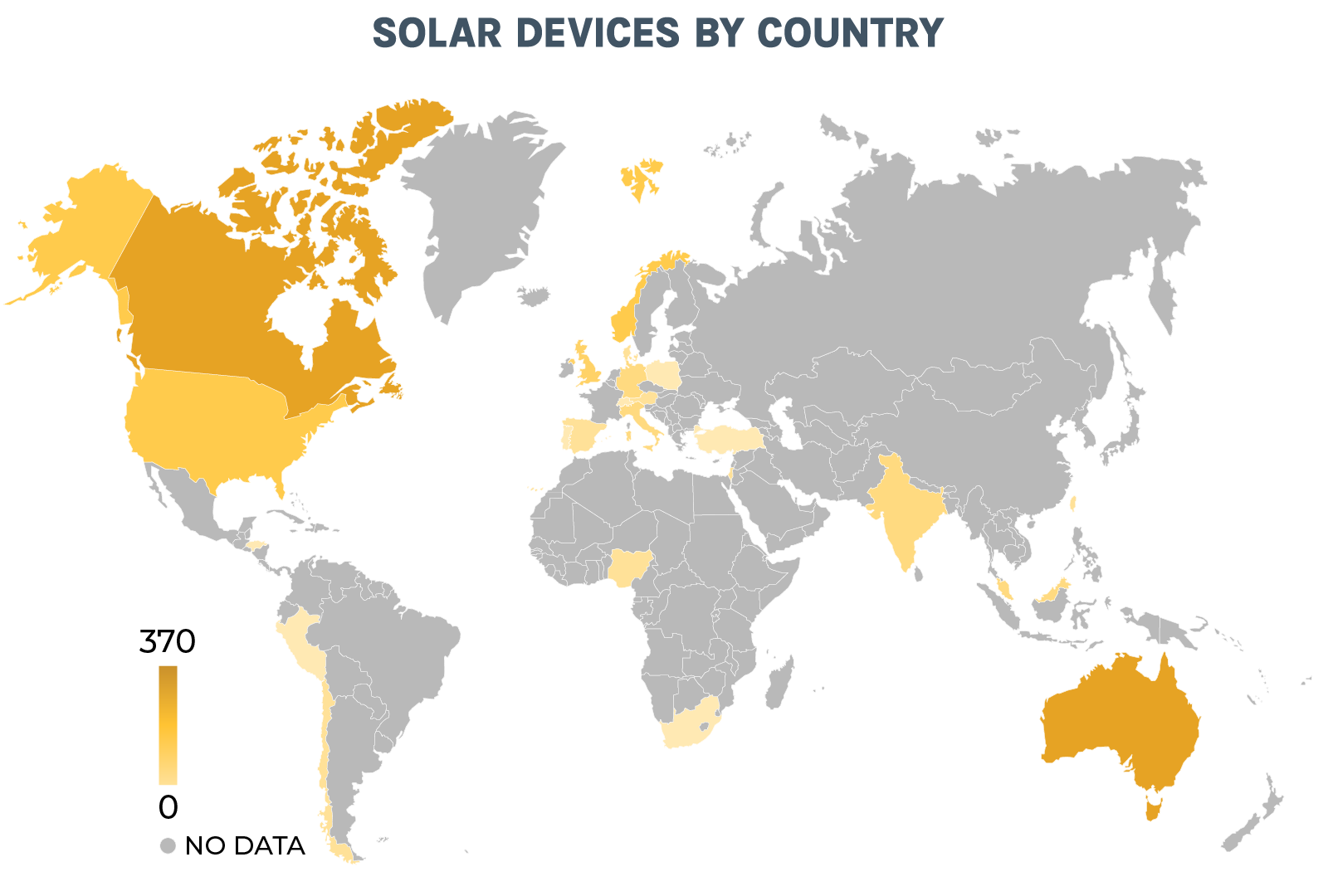
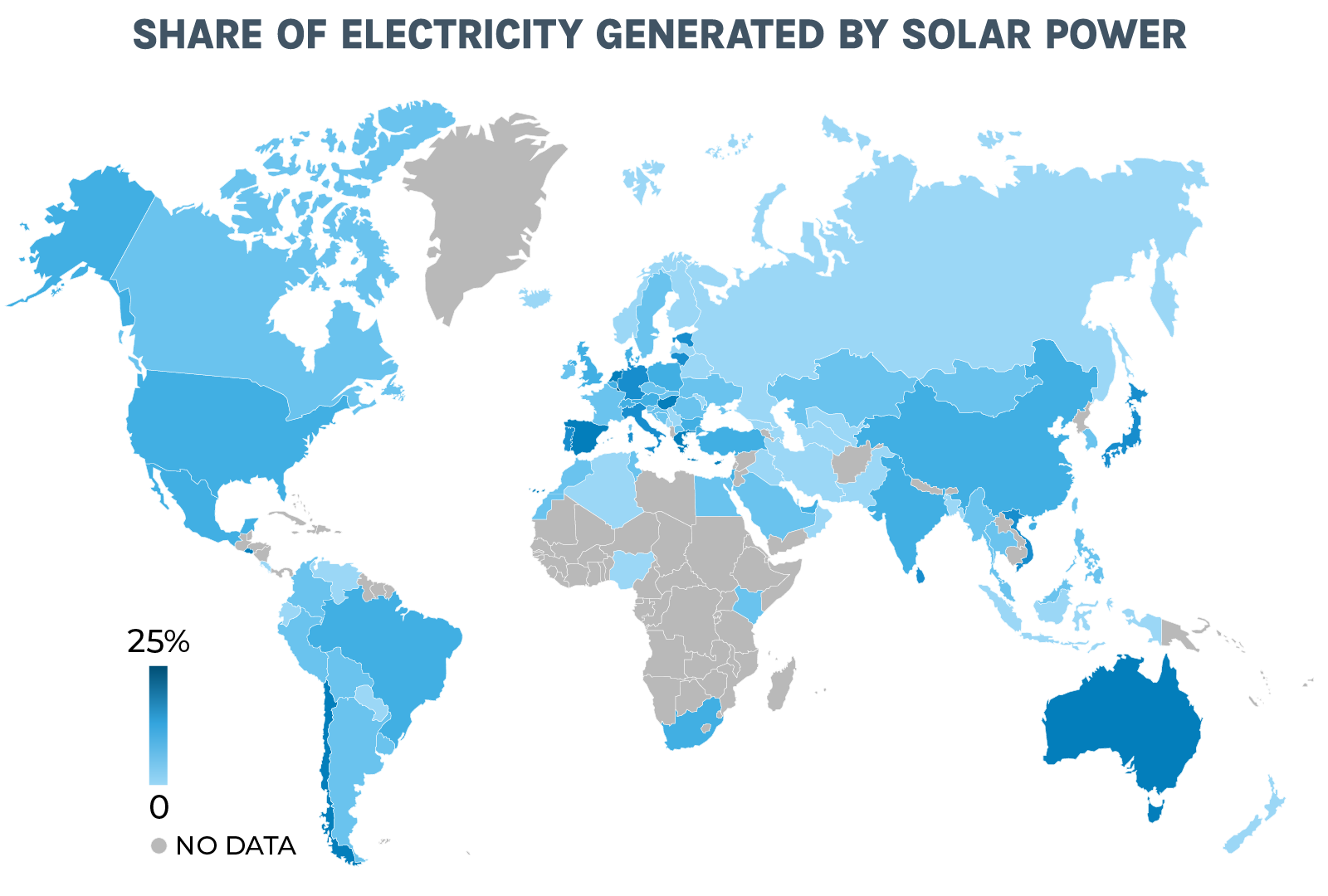
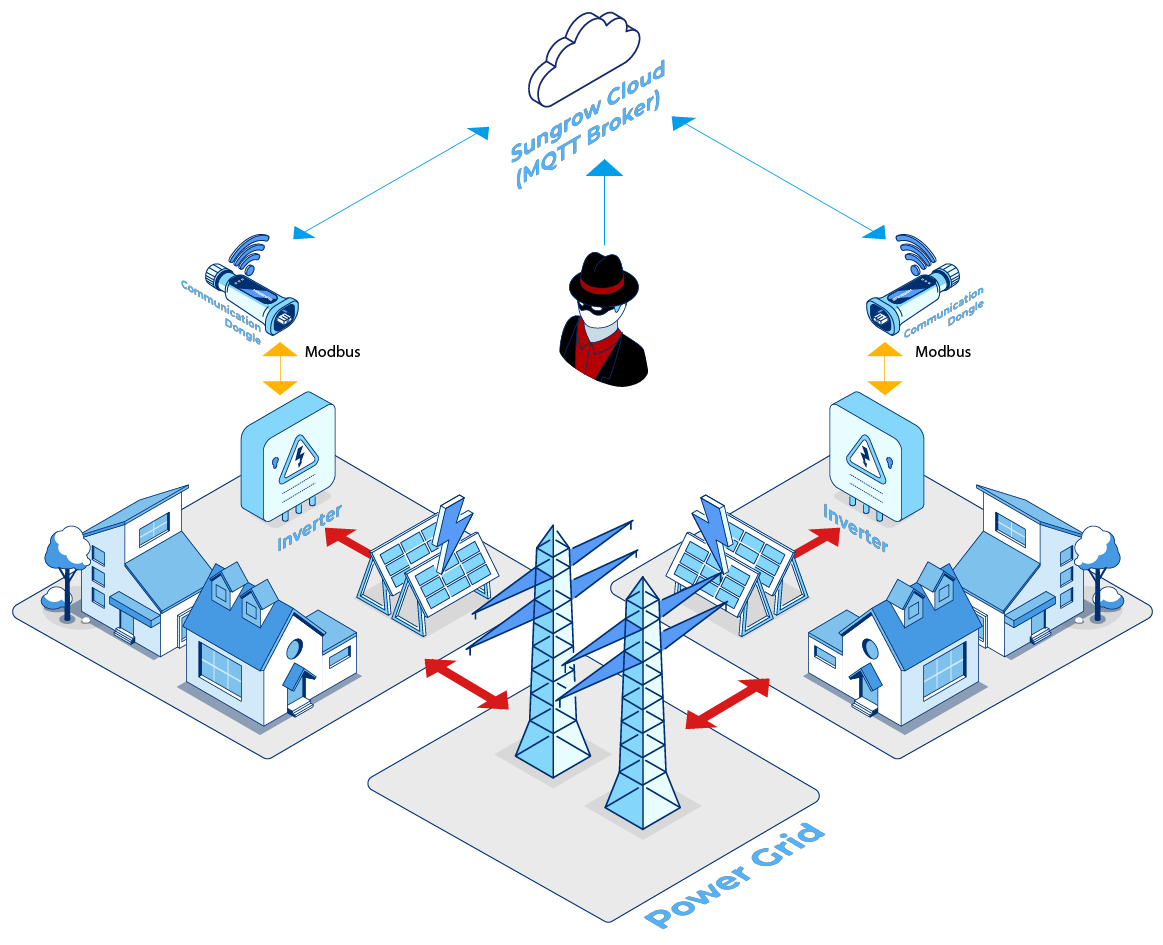
Strategic Recommendations:
How Forescout can Help
- Risk and exposure management. Identify, quantify and prioritize cybersecurity risk. Start by discovering and assessing every connected asset to gain real-time awareness of your attack surface.
- Network security. Continuously monitor all connected assets to govern network access, using real-time traffic visibility to manage segmentation and dynamic control policies to mitigate and remediate risk.
- Threat detection and response. Detect, investigate and respond to true threats and incidents using threat detection and response capabilities to collect telemetry and logs, correlate attack signals, generate high-fidelity detections and enable automated responses.