The global threat evolution of internet-exposed OT/ICS
Operational technology (OT) and Industrial Control Systems (ICS) are core parts of an engine fueling critical infrastructure in industrialized nations worldwide. Water treatment facilities. Wastewater plants. Electrical transmission and distribution hubs. Nuclear power and manufacturing plants. Energy pipelines.
Over the years, these traditional technologies have become more connected and integrated to information systems that use the internet – opening them up for more efficient monitoring and automation of operational processes.
However, many integrated systems that emphasize automation with digital connections have been fodder for state-sponsored cyberwarfare, criminal activity and political hacktivism. In fact, opportunistic attackers are increasingly abusing OT/ICS exposure at scale — sometimes with a very lax targeting rationale driven by trends, such as current events, copycat behavior or the emergencies found in new, off-the-shelf capabilities or hacking guides.
A recent wave of attacks by the Iranian-affiliated Cyber Av3ngers hacktivist group targeted Unitronics Programmable Logic Controllers (PLCs) around the world, including at a water utility near Pittsburgh. Unfortunately, it has brought internet-exposed OT/ICS back into the spotlight. A majority of media attention has been focused mostly on attacks on Israel and the US, but there are more countries and regions being exposed and attacked under the surface – and it extends beyond water utilities and Unitronics PLCs.
Forescout Research – Vedere Labs has been tracking internet-exposed OT/ICS data for over seven years – and the outlook remains mostly unchanged. Despite decades of raising awareness, navigating new regulations and advisories from CISA, critical infrastructure continues to be rife with open ports and hackable devices. For example, the same ICS/SCADA hacking guide that details how to attack Unitronics PLCs also has examples for Schneider Electric Modicon PLCs.
Take note: These Schneider devices are likely to be mass targeted in the future, so action should be taken as soon as possible to protect them.
In a new threat briefing “Better Safe Than Sorry”, we take a fresh look at exposed OT/ICS data between 2017 and 2024. We analyze and detail problem areas by region and offer mitigation strategies. We detail three recent cases of device exposure that we have been tracking: the Unitronics attack wave and our attempts to proactively identify and notify asset owners with exposed Schneider Electric Modicon and Wago 750 PLCs.
For complete details with detailed mitigation strategies, plus our data on the exposure of devices using the Nucleus NET and NicheStack TCP/IP stacks, access the report.
The evolution of OT/ICS exposure between 2017 and 2024
Using Shodan’s pre-configured ICS tag search filter – which finds many but not all exposed OT/ICS devices – we can see close to 110,000 Internet-facing devices as of the end of January 2024. The United States has 27% of exposed devices, followed by Italy, Spain, France and Canada with a combined total of 17%.
How has exposed OT/ICS evolved since 2017? Watch our research leaders discuss on-demand.
 |
|
 |
 |
 |
 |
 |
|
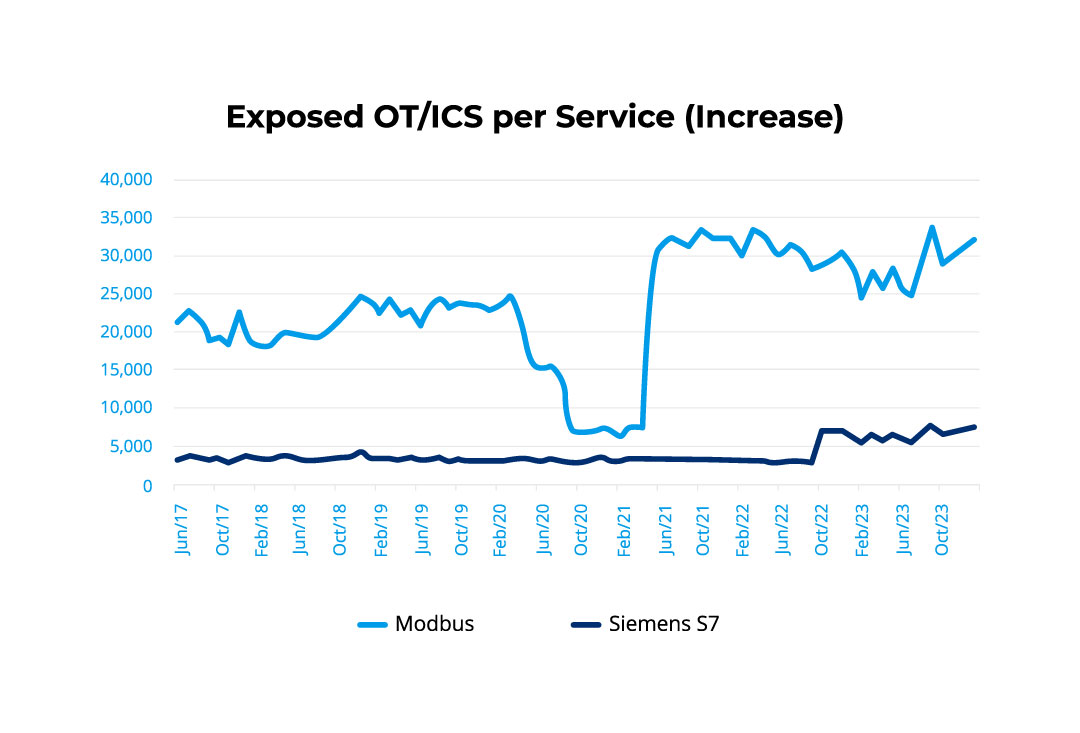
Manufacturing and building automation protocols make up a major portion of exposed device types.
Modbus represents 29% of exposed services, followed by three building automation protocols – KNX, BACnet and Tridium Fox – with a combined total of 32%.
The top 10 types of exposed services remained mostly constant since 2017, but Tridium Fox, Lantronix and MOXA Nport saw a significant decrease in the number of devices (70% for the first two and 53% for the last) while Modbus and Siemens S7 saw an increase: 48% for Modbus and 121% for S7. Some of these reductions correlate with proactive research and government notifications.
 |
 |
A fresh take on the Unitronics attacks: Israel and the US are not alone — and it extends way beyond water
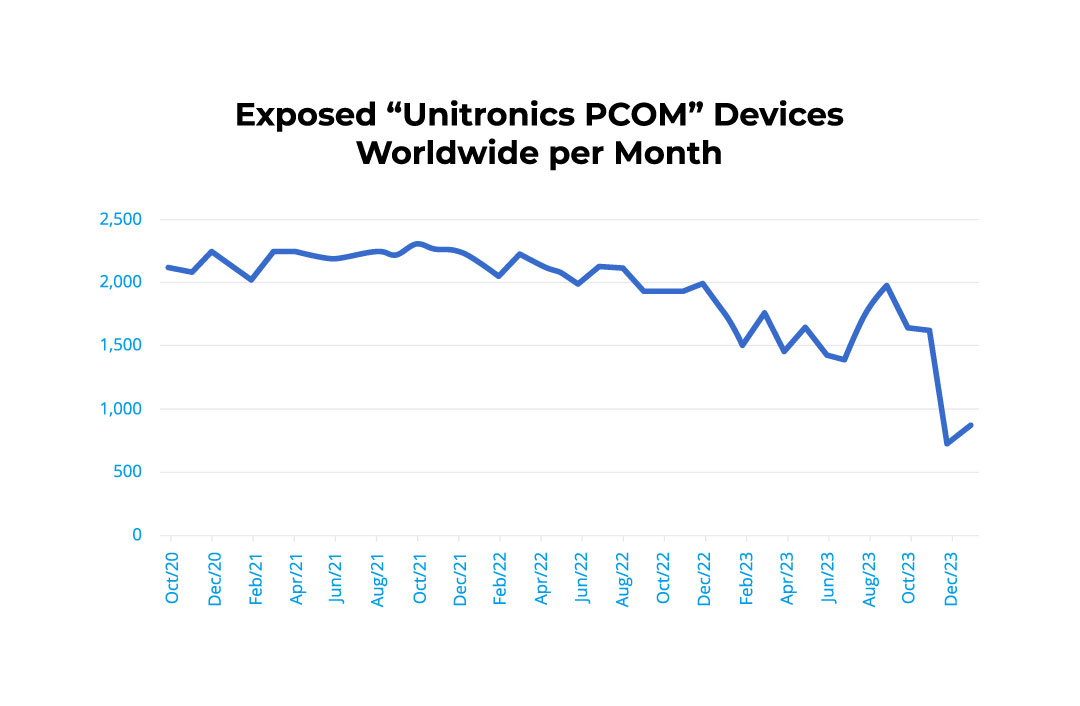
Media focus has mostly been on the effects of the Unitronics’ attacks on the US and Israeli water sectors, however, the attack waves have not been limited in geographic or sector scope. Deeper awareness has led to a reduction in exposed devices, according to our data. But the risk remains and is not limited to one flavor of PLC.
This indiscriminate wave hit everything from water utilities in Ireland and Romania, oil pumps and a public aquarium in the US, a brewery in Pittsburgh, a factory in the Czech Republic, and various unspecified victims on the Unitronics support forum, to several agricultural entities in Western Europe reported privately to Forescout.
Back in February 2022 and April 2023 defacement imagery on these PLCs had already targeted this equipment in agricultural water controllers and parcel distribution centers in Israel. By November 2023, there were a series of attacks on internet-exposed PLCs manufactured by Unitronics where hacktivists defaced the interfaces on those PLCs.
Secureworks reported the hacktivist group GhostSec also claimed to have targeted Unitronics PLCs in Israel in October 2023. In March 2023, a Telegram channel associated with GhostSec posted an ICS / SCADA hacking guide explicitly showing how to identify Unitronics devices and how to use Unitronics VisiLogic software to connect to these devices using the PCOM protocol (port 20256/TCP) and then take control of their HMIs.
We noted in November there were over 1,800 internet-exposed Unitronics PLCs across the globe. As of early February 2024, this number has fallen to 937 Figure 4.
 |
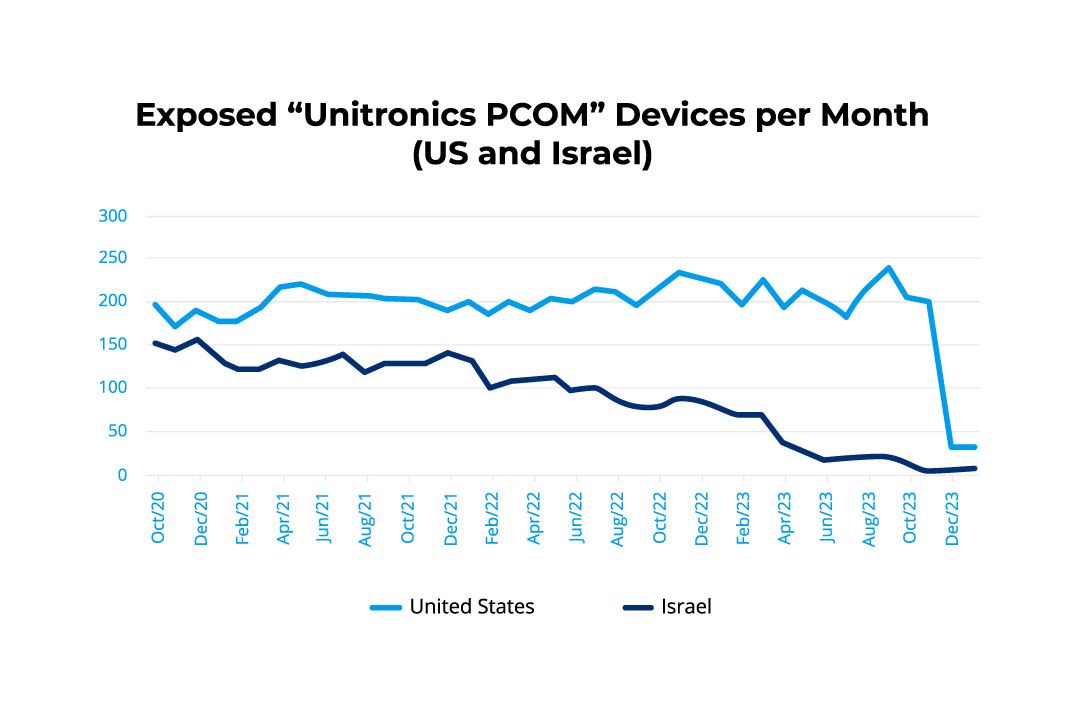 |
In the US, the decrease only started at the end of 2023. To be clear, this means that if the US authorities had paid attention to the attacks in Israel in 2022, the most recent attacks in the US could have been avoided.
The scope of PLC exposure and fresh use cases
Beyond that, we still see too many Unitronics PLCs exposed in the water and agricultural sectors, but also in building management systems, including at:
- A major distribution center
- A healthcare contractor
- A research lab gas management system
- Multiple residential apartment complexes managed by a property management company
Another interesting use case is the deployment of Unitronics PLCs in so-called packaged units or modular skid systems. These self-contained systems are typically integrated by a third party into a customer’s control system in a turnkey fashion, with the internals of the unit being a black box to the asset owner. We found examples of Unitronics PLCs as part of:
- Oil field pump controllers (previously unreported)
- Brewery solutions
- Biofuel boilers
- Industrial heating boilers
- Substation battery tripping units
Finally, we observed that many PLCs were exposed in similar ‘clusters’: e.g. various water controllers belonging to several different municipal utilities in a Nordic country, all with very similar configurations, which points to the likely role of system integrators servicing multiple asset owners in the misconfigured exposure to the internet.
Does proactive notification of exposed asset owners help?
As part of our Deep Lateral Movement research published in February 2023, we showed internet-exposed instances of two PLC lines covered in that research: the Schneider Modicon exposing UMAS and the Wago 750 series exposing web and/or FTP interfaces. At the time of that research, we identified dozens of affected asset owners and contacted CISA to alert them.
In light of the Unitronics attack wave, and considering the historical targeting of Modicon and Wago PLCs and the reported interest in Wago PLCs by the attackers to which Cyber Av3ngers have been attributed, we decided to reassess the exposed devices a year after we originally reported them to CISA.
Unfortunately, we noticed that about half of the reported PLCs still had the same ports open with no changes or measures taken. About 30% were no longer internet exposed, while the other 20% remained exposed but had closed the OT port in question (though sometimes leaving FTP and web interfaces open).
Although we saw a reduction in exposed devices due to proactive asset owner notifications, that has not happened with the same speed as for Unitronics – possibly because there has not yet been any mass exploit campaign against Schneider Electric or WAGO equipment. However, there are early examples of opportunistic attackers targeting these devices and the same ICS / SCADA hacking guide that detailed attacks against Unitronics also has examples of attacks against Schneider Electric Modicon PLCs.
We reinforce the message that these devices are likely to be mass targeted in the future and action should be taken as soon as possible to protect them.
Recommended mitigations
It is likely responsible asset owners are unaware that OT/ICS systems contain potentially vulnerable Unitronics, Schneider and Wago devices exposed to the internet, once again highlighting the need for an accurate and granular software and hardware bill of materials as part of a comprehensive risk management strategy.
To reduce risk, organizations should proactively leverage targeted notifications. Due to the increased scope of attacks on exposed OT/ICS, we recommend asset owners:
Harden connected devices
Identify every device connected to the network and enumerating known vulnerabilities, used credentials, and open ports. Change default or easily guessable credentials and use strong unique passwords for each device. Disable unused services and patch vulnerabilities to prevent exploitation.
Segment
Do not expose unmanaged devices directly to the internet, with very few exceptions such as routers and firewalls. Follow CISA’s guidance on providing remote access for industrial control systems. Segment the network to isolate IT, IoT and OT devices, limiting network connections to only specifically allowed management and engineering workstations or among unmanaged devices that need to communicate.
Monitor
Use an IoT/OT-aware, DPI-capable monitoring solution to alert on malicious indicators and behaviors, watching internal systems and communications for known hostile actions such as vulnerability exploitation, password guessing and unauthorized use of OT protocols. And monitor the activity of hacktivists on Telegram, Twitter and other sources – and watch what kind of hacking material is shared.
For specific details with complete mitigation strategies, access the report.